Every network has its weaknesses.
But do you know what they are and the impact they have on your network security? With the large amount of data on systems and advances in attack sophistication, it’s more important than ever to have a complete picture of what’s going on in your network.
What is Network Visibility?
Network visibility, at a basic level, is an awareness of all of the activity and data on your network. It allows you to expose and resolve blind spots in security, optimize and reduce inefficiencies, and monitor applications and overall traffic.
It provides a proactive approach to security, helping you to detect your network’s weaknesses so you can increase and optimize your security measures. Ultimately, network visibility means increased security. As your team is equipped and aware of potential attacks, they are able to better defend against a growing number of threats, protecting your company and customer data.
Why Does Network Visibility Matter?
Network visibility remains a topic of interest as attacks continue to advance and IT teams discover previously unknown issues on their networks.
This becomes even more important as the amount of data and the number of vulnerable endpoints within an organization rise. These challenges increase the threat of attacks making their way onto the system through phishing attempts or other targeted means, focused on gaining access to the systems and data on the network.
Start by Assessing the Current Risks
As you look to achieve network visibility, it’s important to have the architecture in place to see each element of network activity and traffic. Many companies will build and add different components or technologies along the way to manage their network—yet, this method can create blind spots due to the complexity of your systems. Analyzing your existing technology is the first step to see if there are any holes that make you vulnerable to additional attacks.
From there, you’ll want to take additional steps to find those weaknesses on your network.
Risk Assessment
After you have analyzed the technology and software you have in place, take the next step and assess it for risks. This will help you see if you’ve optimized your spending when it comes to security so that you have the protection you need with your technology and services.
You can resource outside partners to perform a risk assessment, providing an analysis of your company’s security and building a strategy to reduce the risk.
These assessments will provide an outside perspective on potential risks and vulnerabilities—including a collection of the existing data, examinations of your systems and processes, and evaluations with reporting on the areas of potential weakness.
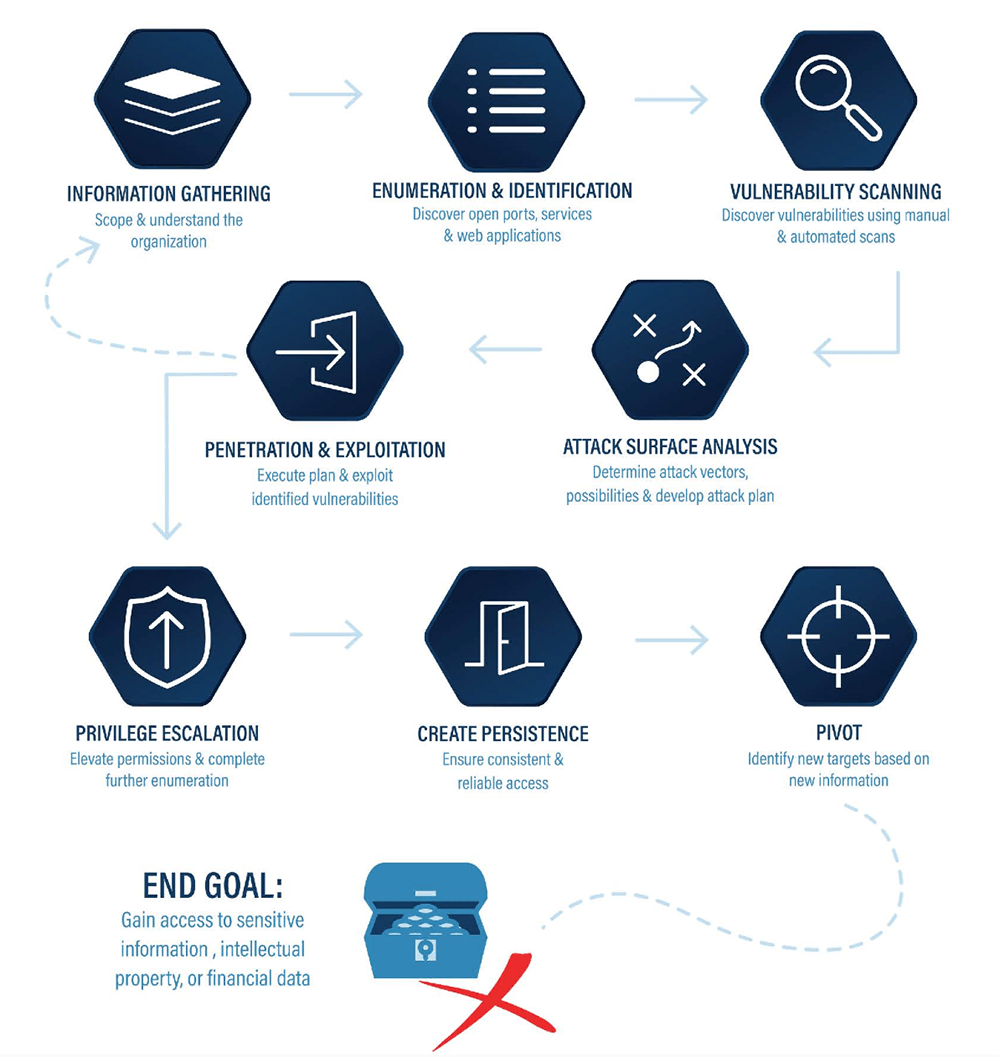
Penetration Testing
In addition to finding vulnerabilities through a risk assessment, you can also invest in penetration testing. These tests go a level deeper than performing scans and assessments to search for the weaknesses. Penetration testing performs a real-world attack simulation where security experts show the weaknesses in your network. This allows you to see what areas are lacking in your technology and better manage the blind spots that open you up to attacks.
Be Proactive in Network Visibility
After companies analyze, many will use different tools to manage their data and keep a close eye on vulnerabilities and network activity. This means taking a proactive, rather than reactive, approach to your security.
Security Information and Event Management (SIEM)
This technology will collect the logs from devices on the network as well as firewalls and servers. It consolidates these logs, which allows your team to track behavior and investigate threats. SIEM technology primarily reports on network activity, and specific rules or queries must be created to tell the SIEM what behaviors to track. It can provide a holistic view of your network, but alone it doesn’t give the depth of visibility that you need to actively detect and fight potential threats.
Vulnerability Management
Detecting risks or tracking data isn’t enough—you also have to create a strategy to manage and take action against those potential threats. A vulnerability management strategy gives you the technology and team to fight potential threats. It is the foundation necessary to understand what’s on your network and the risk for every asset you have so that you can prioritize and fight back. With a vulnerability management service, you can see the threats inside and outside of your network. The process of vulnerability management helps you discover, assess, prioritize, and remediate threats, adding a level of strategy to increased network visibility.
Endpoint Detection & Response (EDR)
Network visibility does more than give you data on traffic or show where your vulnerabilities are. It gives you the ability to see when someone or something is on your network when it shouldn’t be, no matter how advanced the attack. Endpoint Detection & Response helps you protect against even the most advanced attacks, like fileless attacks or advanced persistent threats (APT). When your prevention fails and threats look like legitimate user activity, EDR gives you visibility into the attack using behavioral analysis and advanced algorithms, helping you achieve true visibility and protect your endpoints.
Managed Detection and Response
Unless you have a full in-house IT and security team, it can be a challenge to achieve network visibility on your own. That’s why many companies work with partners to detect vulnerabilities and respond to potential threats. Managed detection and response (MDR) is an outsourced service that gives you visibility through threat hunting services and a team of security engineers who help monitor networks, open the door to visibility, and respond to attacks. This brings additional resources and security to companies whose visibility is limited on their own.
The Benefit of Network Visibility
The benefits of increased network visibility can impact nearly every aspect of your company and IT team. Taking a proactive approach to security can help you detect weaknesses and mitigate them with technology or services. That optimization ultimately tightens your network security, reducing the costs of investigations to create a safer network for your company and customers.

