As the intelligence of hackers continues to grow, so does the technology built to protect against even their best attacks.
Technology like Endpoint Detection & Response (EDR) can be invaluable to businesses or managed service providers (MSPs), but with such a powerful tool, there are many questions that need to be answered to understand how it works, what it protects against, and the benefits it can offer.
What is EDR?
Endpoint Detection & Response (EDR) is a proactive approach to security that monitors endpoints in real time and hunts threats that have infiltrated a company’s defenses. It’s an emerging technology that offers greater visibility into what’s happening on endpoints, providing context and detailed information on attacks. EDR services allow you to know if and when an attacker is in your network and to detect the path of the attack if it happens—helping to respond to incidents in record time.
Why does it matter?
“It’s no longer about preventing attacks at the endpoint—that can’t be done 100 percent of the time—but instead catching an attack or attack attempt ASAP. The goal is to mitigate the damage and stop any further infiltration into the network via the victimized user’s machine.”
—Kelly Jackson Higgins, Dark Reading.
Because of the large number of endpoints on a given system, it’s increasingly difficult to protect from advanced attacks that enter through endpoints, such as individual computers or mobile devices. This is often where hacker activity takes place and, even with the most advanced protection, a breach could still occur. According to a report from the IDC (International Data Corporation), 70% of successful breaches start on endpoint devices. These types of attacks can be detrimental due to reputation loss or financial ruin. Customer information and network security must be protected, and yet most small and mid-sized businesses don’t have the resources for 24/7 monitoring as it becomes increasingly difficult to withstand these types of attacks. Businesses of all sizes need to protect their data and have greater visibility into advanced threats—all in a cost-effective manner. An EDR solution can do just that.
How does EDR work?
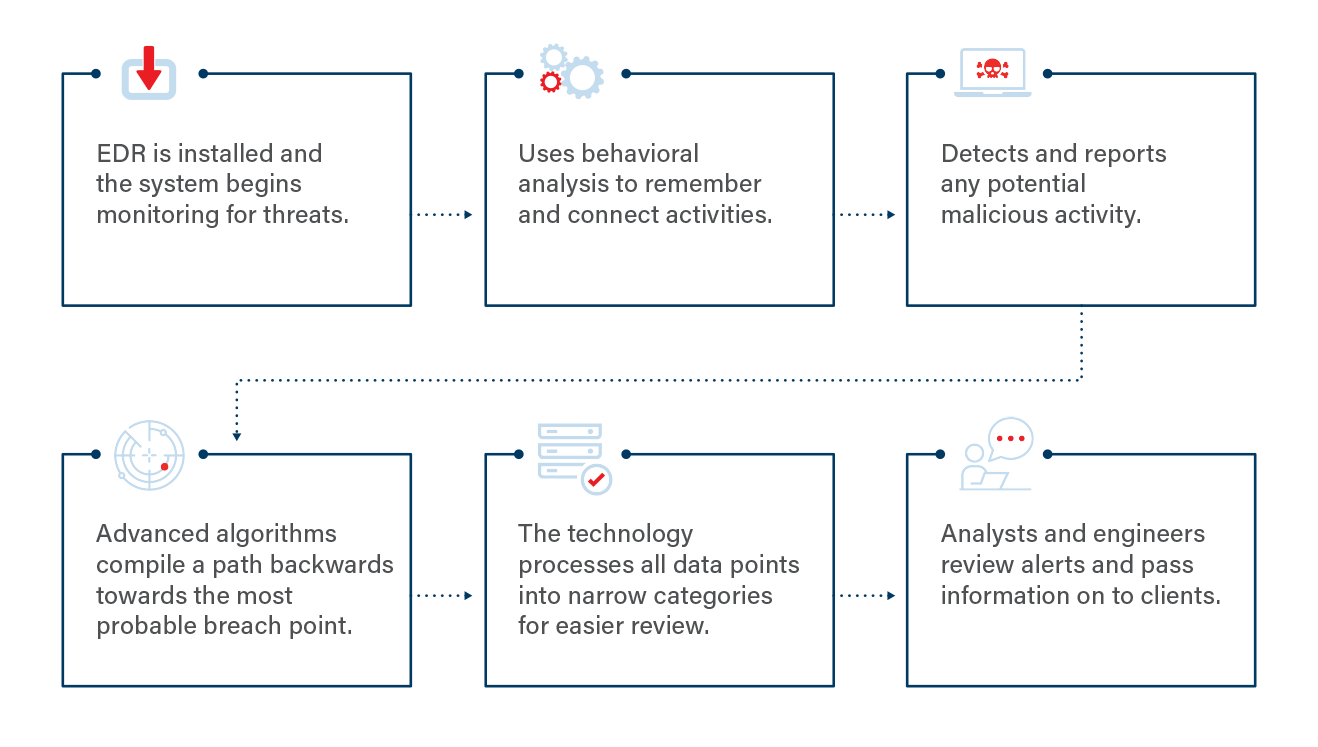
Once EDR technology is installed, it uses advanced algorithms to analyze the behaviors of individual users on your system, allowing it to remember and connect their activities. In the same way that you often notice when something feels off or different about someone you’re close to, the technology can “sense” behavior that is out of the ordinary for a given user on your system. The data is immediately filtered, enriched, and monitored for signs of malicious behavior. These signs trigger an alarm and the investigation begins—determining if a hit is true or a false positive. If malicious activity is detected, the algorithms track the path of the attack and build it back to the point of entry. The technology then consolidates all data points into narrow categories called MalOpsTM (Malicious Operations) to make it easier for analysts to review. In the event of a true hit, the customer is notified and given actionable response steps and recommendations for further investigation and advanced forensics. If it is a false positive, the alarm is closed, investigation notes are added, and the customers are not notified.
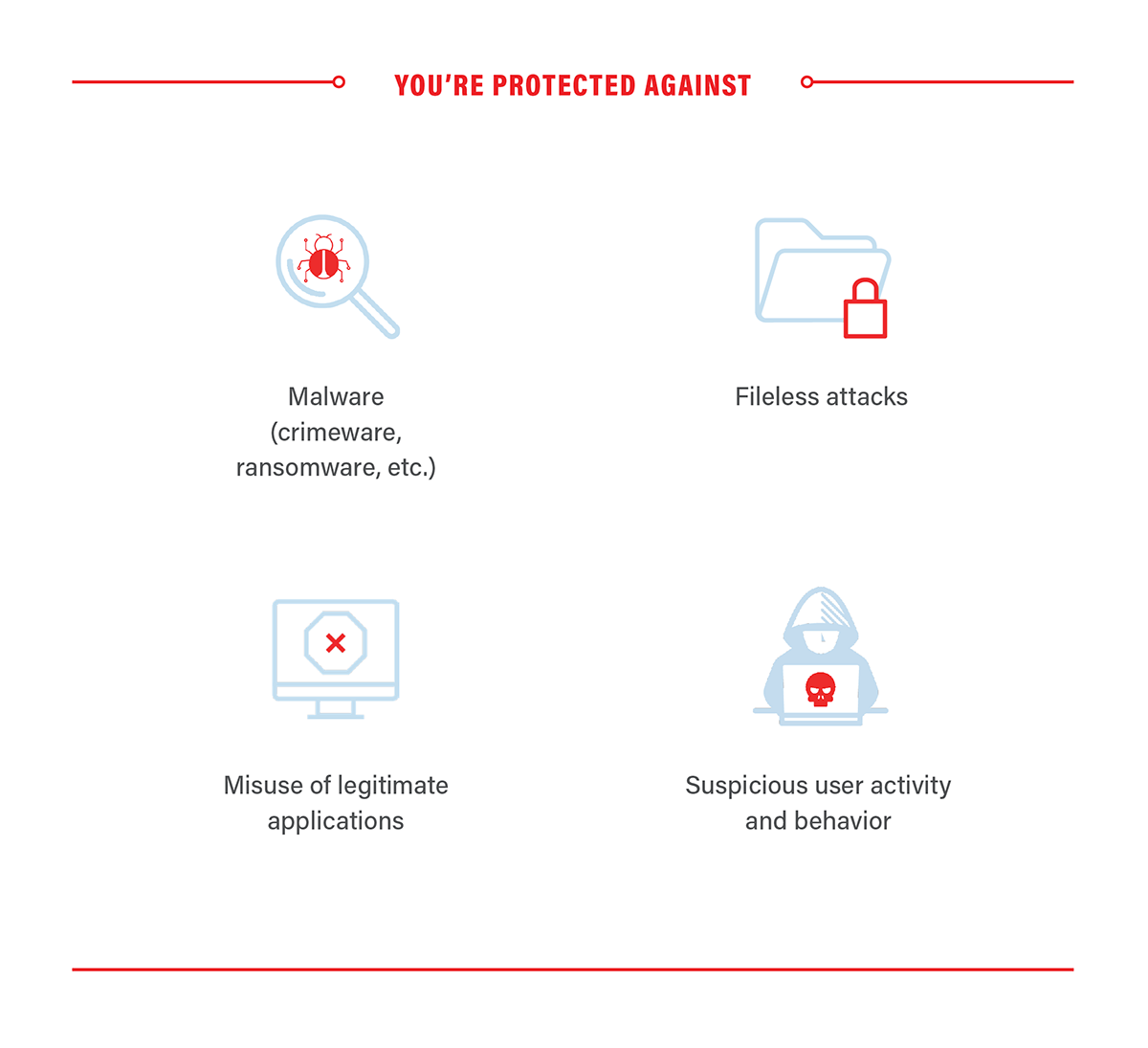
What type of threats does EDR detect?
EDR protects against fileless malware, malicious scripts, or stolen user credentials. It is designed to track the techniques, tactics, and procedures that an attacker uses. But it goes even deeper. Not only does it learn how attackers break into your network, but it also detects their path of activity: how they learn about your network, move to other machines, and attempt to accomplish their goals in the attack. You’re protected against:
- Malware (crimeware, ransomware, etc.)
- Fileless attacks
- Misuse of legitimate applications
- Suspicious user activity and behavior
What are the elements of EDR?
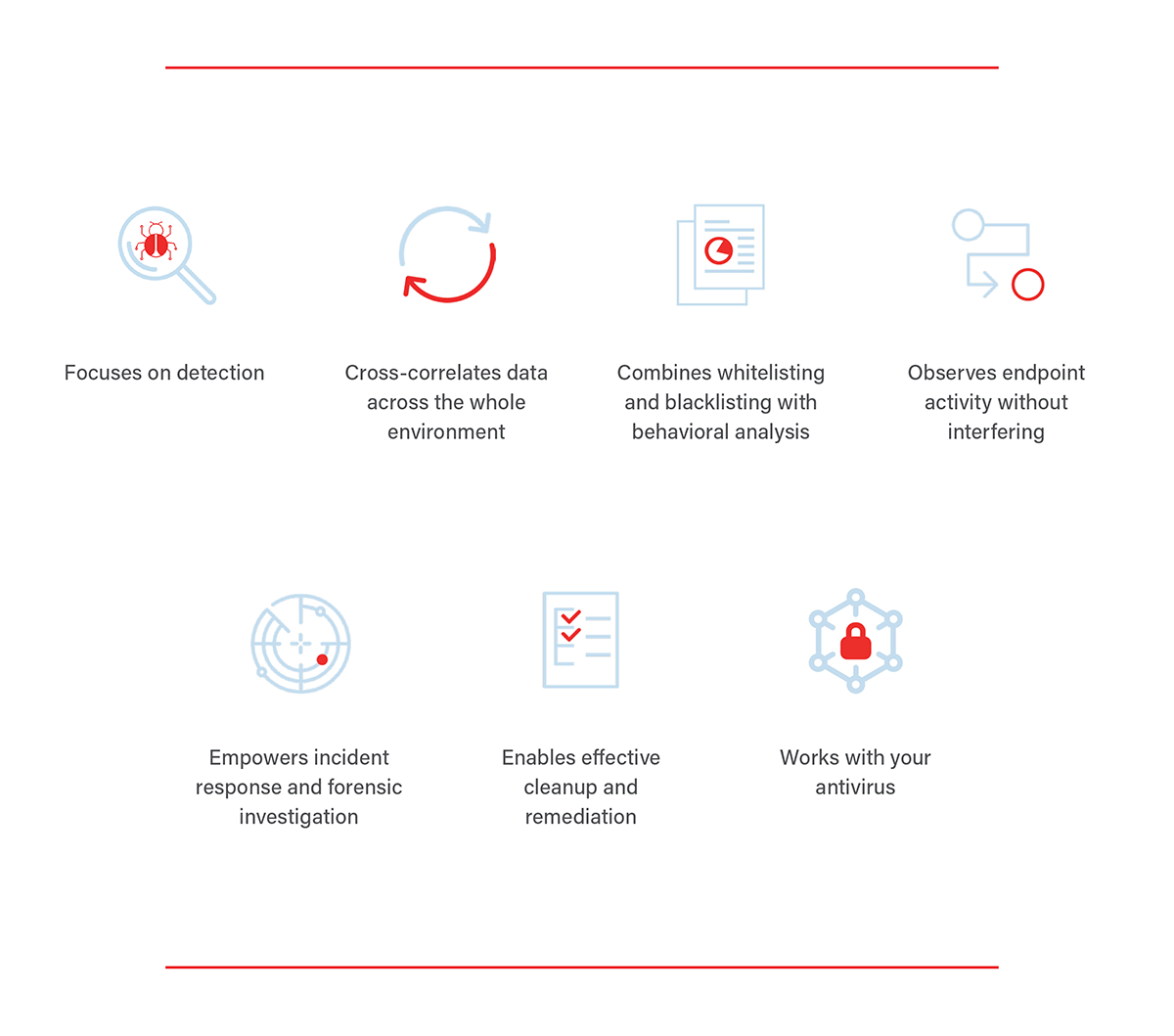
EDR is unique because its algorithms not only detect and fight threats, but also streamline how alerts and attack data are managed. Using behavioral analysis to analyze user activity in real time allows for immediate detection of potential threats without interfering with endpoints. It empowers the forensic investigation by consolidating attack data into stories that can be analyzed, working with your antivirus and other tools to provide a safe and secure network.
How are incidents processed with EDR?
EDR processes and responds to threats in an innovative way that streamlines analyst investigations, saving both time and money. The system monitors hundreds of thousands of data points or alerts and consolidates them into narrow categories called MalOpsTM. That data is then processed and filtered through the AI engine and compared to previous dataset patterns and behaviors to help identify previously unknown or known malicious activity. After the current and past data is compared, decisions are made within the AI engine to send an alert about the incident, restrict the activity, remove the threat, and repair any damage. Because the incidents are consolidated into narrow categories using MalOps, the investigation hours required from an analyst are dramatically reduced. 
According to the Infosecurity Group, there were at least 360,000 new malicious files detected every day in 2017, which means companies must aggressively fight against these threats and have a more streamlined detection and review process. This allows analysts to efficiently fight and detect the biggest threats.
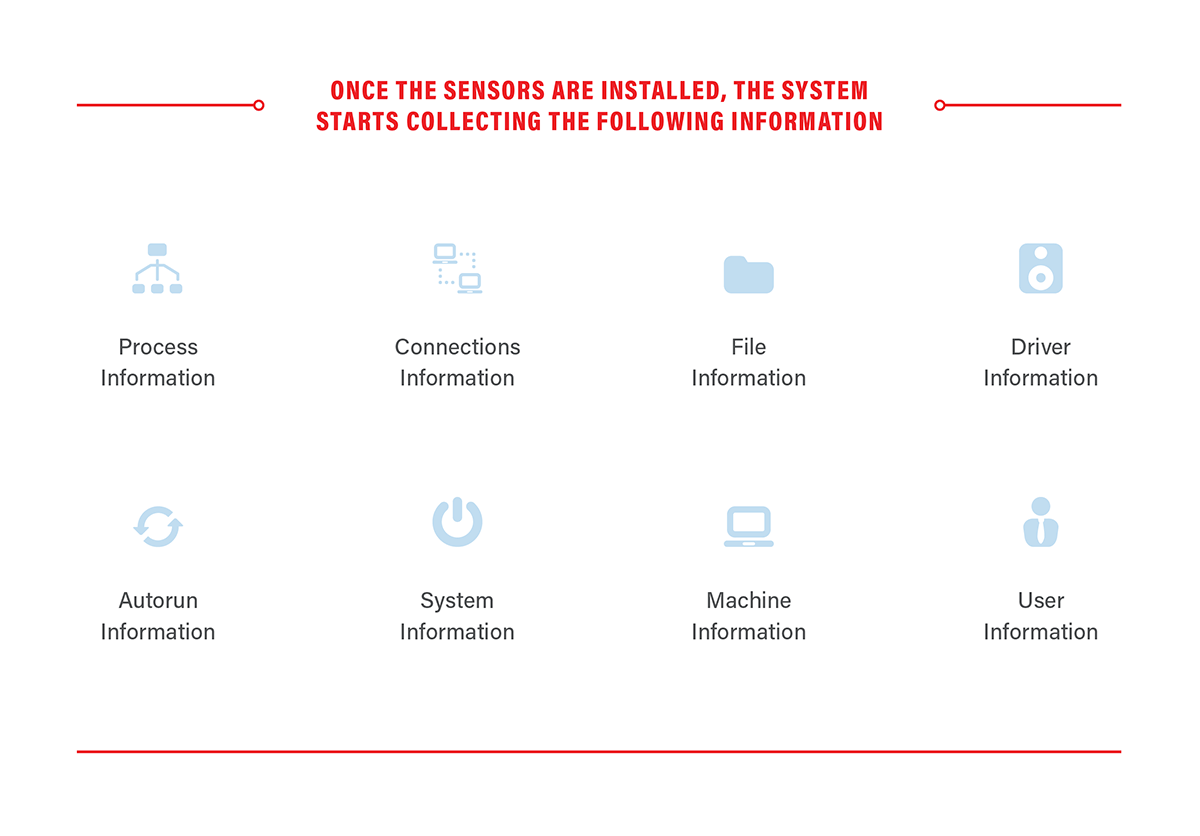
What information does EDR collect?
Endpoint Detection & Response runs through sensors installed on your endpoints—no reboot required. All of this data is pieced together to build a complete picture of endpoint activity, no matter where the device is located.
Why is EDR better than traditional methods of post-breach analysis?
As attackers become more skilled and adjust their methods to current technology, traditional methods of post-breach analysis are no longer enough. First is the response time.
After an attack, time is critical and a slow investigation may be detrimental to your company.
Traditional methods require extended time for an investigation—all while the attacker might be doing more damage to your network and putting your clients and data at risk. Traditional methods are also limited in the depth of information and breadth of the investigation. Even if they are able to determine the impacted areas, traditional methods are typically unable to show where the attack entered and the path it took. EDR lets you know when an attack occurred, but also compiles the behavioral data to show the attack path on your network, from where it entered to the actions it took. In addition, EDR compiles the data in a way that is easier for analysts to review, significantly reducing the amount of data to analyze. This, in turn, reduces the overall time and cost of post-breach analysis.
Traditional AV vs EDR
A common question people ask is the difference between EDR and a traditional antivirus (AV) or next-generation antivirus (NGAV). In their minds, they don’t need both technologies. But that is not the case. The reality is that both technologies serve different purposes in protecting your network. AV and NGAVs are focused on prevention but have zero visibility into what happened during an attack. They’re designed to catch the bad before it enters your network. But even when they do that correctly, they aren’t designed to show you where the malware came from and how it spread in the system. EDR tells the whole story and helps you track how the executable gained access to the machine and attempted to run. EDR not only provides visibility when an attack is stopped by an AV, but when control fails with a good NGAV, you’re most likely dealing with a serious attack such as fileless malware, zero-day exploits, or advanced persistent threats. These types of attacks don’t leave signatures, which makes them harder to prevent and nearly impossible to detect without a service like EDR. It will warn you of attempted attacks and provide insight when attackers have gotten past all of your defenses and are currently in your network.
The difference between EDR & SIEM
Another common question is the difference between EDR and Security Information and Event Management (SIEM). SIEM is a technology that collects logs from firewalls, servers, and network devices. It consolidates all of your network logs to help track behavior, identify threats, and investigate them. However, rules and queries must be set to tell the SIEM what to look for and what behaviors to track. SIEM is a great service for a holistic view of the activities that take place across your network. EDR consolidates and analyzes the endpoint data specifically, equipping analysts rather than requiring them to analyze hundreds of thousands of logs or events. Ultimately, the two technologies serve different purposes and can complement each other in a secure network environment, but the main purpose of EDR is streamlined, effective detection and response to threats.
Additional Benefits of EDR
The innovative and effective nature of EDR alone proves its worth, but there are additional benefits that go even deeper than the technology.
- More cost-efficient. Rather than hiring a 24/7 in-house security team or leaving yourself open to a large-scale attack, EDR allows you to invest in the security of your company and data in a way that is realistic for a small to mid-sized team.
- Saves time. Because there are fewer alerts to analyze with MalOpsTM and fewer false positives, EDR allows analysts to spend more time investigating legitimate threats.
- Increased team efficiency. Instead of parsing through alerts and comparing them to other data points, EDR correlates data points into one single story, saving analysts enormous amounts of overhead and time. This allows the team to more efficiently process data and protect the company.
What role do security analysts play?
The beauty of EDR is the way it combines advanced technology and analyst expertise.
No human element is required during the detection, path analysis, and lateral movement stages. Analysis and interpretation of the collected data sets are still important, but not during the initial seconds of a detected incident. This allows for increased protection of the network and allows security analysts to investigate the legitimate threats rather than filtering through false positives. Because of how the data is consolidated with EDR and MalOpsTM, it is easier and more intuitive to understand, diagnose and remedy problems. This equips analysts to investigate and provide solutions for legitimate threats.
How is EDR installed?
Installation is simple—just an executable that can be manually installed, scripted, or deployed through a software distribution tool. For our clients, the sensors connect back to the Infogressive main console over HTTPS, so there’s no need for additional firewall rules. All alerts are monitored and reported from the main console.
The impact of EDR
Ultimately EDR can have a dramatic impact on small to mid-sized companies and the protection and security they can provide for their business, customers, and data. As the intelligence of hackers continues to grow, businesses are increasingly at risk. There is too much at stake to not have an endpoint detection and response plan in place.