Ignore security at your own and your customers’ peril.
Recently there was a post on r/sysadmin from a network administrator who had a client system hacked because he left their iLO card facing the internet…
and didn’t stay up to date on vulnerabilities and patching. His lack of situational awareness led to what he initially viewed as a brief operational interruption, but has now come to understand it was a major breach requiring expensive forensic investigations and most likely the end of his business.
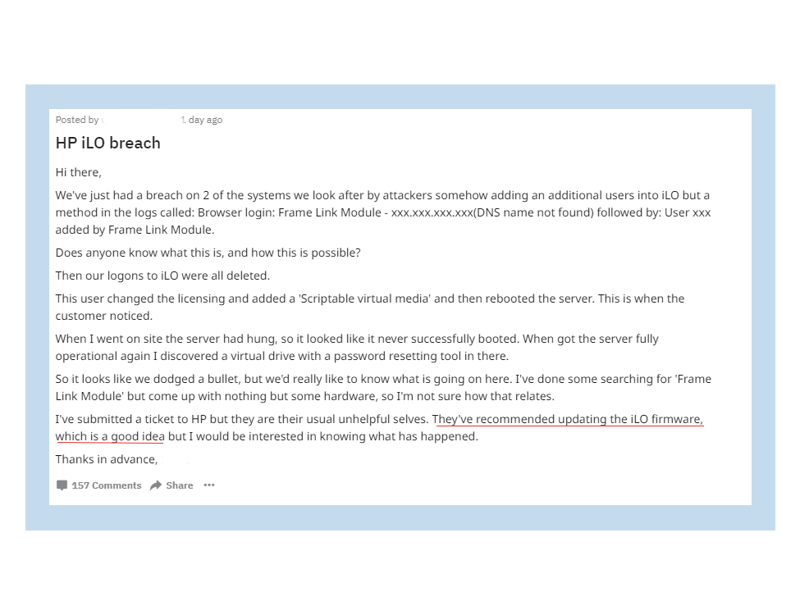
Original post on reddit.com/r/sysadmin
MSPs and system administrators are primarily focused on maintaining the availability of their networks. They do this by building a high performing, redundant infrastructure capable of meeting their client’s operational needs while staying inside their budget. Knowledge of the various fields necessary to be competitive in that arena is esoteric and rapidly changing. System administrators need to be constantly updating their knowledge regarding new technology, new vendors and new capabilities. If they spend their time worrying about security (another esoteric and rapidly changing field of study), then they do their clients a disservice by not offering the best return on investment for the services they were contracted to perform.
In INFOSEC terms, a vulnerability is a flaw in a system that can leave it open to attack. It can refer to a weakness in hardware, software, or implementation which leaves an information system exposed to a threat. MITRE—an American non-profit organization based in Bedford, MA—maintains a database of common vulnerabilities and exposures called the CVE list. MITRE began tracking vulnerabilities in this fashion in 1999. In that year, they cataloged 894 vulnerabilities. In 2017, there were over 14,000 vulnerabilities cataloged, and now, just halfway through 2018, over 10,000 new vulnerabilities have been discovered. As information systems become more complex and ubiquitous, the likelihood of compromise becomes greater, as does the potential for damage.
Strangely enough, remediating discovered vulnerabilities tends to be relatively simple. Most software and hardware vendors track new vulnerabilities and, as soon as they’re made aware, begin writing and releasing patches. (Update your Windows servers regularly!) But with thousands of new vulnerabilities being discovered monthly, how do you track where you’re exposed?
What you can do…
Infogressive’s Vulnerability Management program is your solution. We scan all internal and external assets and identify where you’re weak. We produce regular reports that define your vulnerabilities in an easy-to-read format and allow you to track your progress in their remediation.
If you’re worried about your exposure (and you should be!) contact us at Infogressive today to discuss Vulnerability Management or any of our other managed security products.
If you think your organization may be at risk or affected by the vulnerability mentioned in this post, read more about it here.
