What defines a cyber “incident”, and if it happens to your business, how serious is it? These are two prominent questions among businesses of all sizes and industries. These questions, however, are especially vital to answer for small businesses who often lack the staffing, technology, and resources to understand and implement adequate cybersecurity.
Cybersecurity has been a term increasing in popularity throughout the past two decades, likely aided by countless news-breaking data breaches and cyber threats – but what is it? And what counts as a cyber incident or breach?
This guide will cover everything you need to know about cyber incidents, their consequences, and the Incident Response process.
Cybersecurity: Defining an Incident
Cybersecurity is the broad term that encompasses the security of information technology, networks, computer systems, and digital data. Therefore, a cybersecurity incident happens when any, or all, of those components are compromised. Here are a few examples of the varying levels of cybersecurity incidents and the attack tactics that cause them:
-
Phishing Attacks
Some phishing attacks are broad and mass-delivered, using a ‘spray-and-pray’ style of approach, while others are highly targeted to your organization. The type of phishing emails you receive may tell you something about your organization’s online security.
If you’re receiving broad, un-targeted attacks, then its likely that one or more of your organization’s email addresses have been made public through a data breach or perhaps through the information available from your own online presence (i.e. company website, social media, or employees’ online activity.) If phishing emails are directly targeting your company, which often looks like impersonating an important individual or making company-specific comments and requests, this points to a more direct attack and a more involved attacker on the other end.
If a phishing email becomes successful (when someone clicks), you could be facing almost any level of security incident. Phishing is one of the most commonly used entry methods for attackers because it’s so easy, effective, and versatile. The attacker can use the file or link in the email to do any number of things—drop malware, begin a ransomware attack, steal legitimate user credentials, and more. To put it simply, the severity of a successful phishing attack depends on the intent of the attacker behind it.
Read about how attackers can use a simple phishing link to gain control in your network.
-
Malware
Any kind of software with malicious intent is considered “malware.” This includes the many types of malware you may have heard of: worms, viruses, trojans, and more. There are over 350,000 new malware strains registered every day, and each type of malware is designed to move, spread, and perform tasks differently. Some malware strains steal data, others replicate themselves across networks, some execute scripts and complete tasks, while some simply serve as a launch point for bigger and stronger threats.
The important point is, if malware has successfully made it past your defenses and onto one or more of your devices, it’s worthy of an investigation. There’s no telling what damage may be done unless you find out what kind of malware and what its purpose is.
-
Zero-day Exploits
Malware and attack tactics designed to exploit software bugs, unpatched vulnerabilities, and other newly-discovered security flaws are often referred to as zero-days—essentially, exploits that are out in the world for attackers’ use with no protection against them. Zero-days are vulnerabilities that even developers are unaware of until the exploit. Some say the name comes from the idea that a patch or resolution for the problem has existed for zero days, while others say the zero is for the amount of days the vulnerability has been publicly known.
Just one zero-day exploit—or worse, a combination of zero-days, malware, and remote hacking—can allow an attacker to get inside a network and gain control over their target.
-
Man-in-the-Middle Attacks
Some attackers will use one or more of the tactics listed above as a means to intercept an organization’s communications. While they are becoming less common due to the capabilities of advanced malware, these “Man-in-the-Middle” (MITM) attack methods can be used to obtain credentials, steal data, and even redirect the transfer of funds.
Usually, a MITM attack takes place outside of a network’s internal and device-based security protections at the point of communication between an organization and the “outside.” This leaves a MITM attack harder to detect until after the damage has already been done, meaning successful MITM attacks can be significantly more severe and harder to “clean up” than a simple malware incident.
-
Ransomware
The big buzzword you’ve all been waiting for. Ransomware is actually just another type of malware, but it has grown so popular that it now stands alone as its own named threat. Ransomware is essentially the same as the other malware threats explained above—a malicious file that, when executed, performs a specific task. In this case, the task is to encrypt all the files it can get its hands on and then hold them for ransom, usually presenting a ransom message on the computer screen and demanding payment in bitcoin from its unlucky victim.
For organizations with backups, avoiding that payment can be easy—but ransomware attack cleanup is more than just restoring from backup. Ransomware can just as easily be the front-end of a much larger attack, so it’s important to treat ransomware incidents as a high-level threat.
-
Advanced Persistent Threats (APT)
Speaking of high-level threats, APTs are exactly that. An APT is a type of attack where the attacker not only “hacks” into a network for their own gain, but establishes persistence and lurks around for an extended period of time. APT attacks can be executed by individuals or larger hacking groups and used to accomplish any number of hacking objectives.
APTs are the mega-attack in this list, as they may use one—or even all—of the previously listed tactics at some point in their persistent attack. The catch is that in an APT situation, the attackers are pretty clever when doing so. Their goal is to remain undetected for as long as possible, move around to gain as much access as possible, and inevitably do as much damage as possible in the end. This is why, if you find signs of one of the “smaller” cyber incidents in your network, thorough investigation is vital to ensure that the incident isn’t just one part in a much larger, ongoing attack.
Want to learn more about cyberattack tactics? Read our Cyberattack Roster.
What counts as a breach?
Sometimes, news coverage and articles will use “incident” and “breach” interchangeably, but many organizations wonder, when is something an incident and when does it become a breach?
It’s a bit like how a square is always a rectangle, but a rectangle is not always a square.
To put it simply, a breach is a form of cybersecurity incident—but not every incident is a breach. Under the Omnibus Rule, first published in 2013, HIPAA defines a cyber breach as “the unauthorized acquisition, access, use or disclosure of protected (health) information which compromises the security or privacy of such information.” Other compliance frameworks, industries, and legal bodies have adopted similar definitions over the years. Therefore, the best way to identify if a security incident should be categorized as a breach is to determine the following:
- Has any protected information (customer data; personally identifiable information (PII) of customers, partners, or employees; sensitive files; etc.) been accessed by an unauthorized user or attacker?
- Has any protected information been encrypted or locked by an attacker?
- Is there evidence that protected information has been exfiltrated or stolen by an attacker?
- Has your protected information been leaked on the internet, dark web, or to another source outside of its intended audience?
If the answer to any of those questions is yes, then your security incident is a data breach. Some are tempted to accept no signs of data leak as enough proof that there is no data breach, but beware – attackers are crafty and often very good at what they do. Your systems can be used against you and you may not even see the signs without completing an investigation into the first signs of a cyberattack.
How serious is a cyber incident?
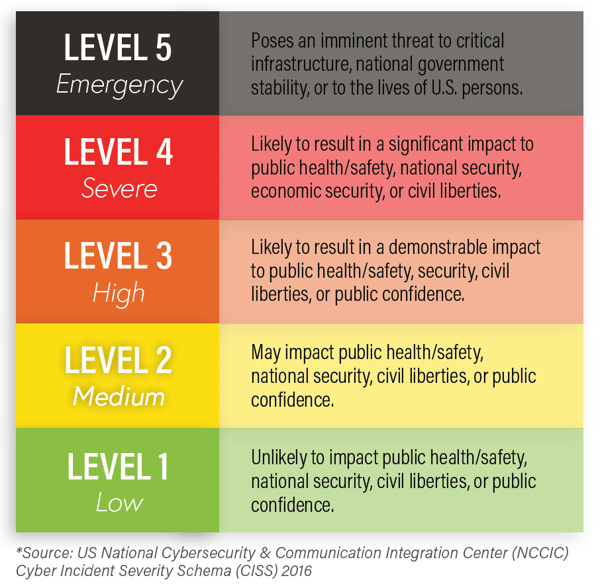
The U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) has defined a scale of severity for national cybersecurity incidents which defines a score based on frequency, priority level, and other factors. How can this be translated from national security to the everyday small and mid-sized organization and their incident response plans?
You may be thinking, “A breach at my organization could never be big enough to impact public safety or national security!” but does that mean a breach at your organization will never be more than a low priority? Of course not. Let’s break it down to a more tangible level.
Here’s a scale of cyber incident severity for the everyday organization:
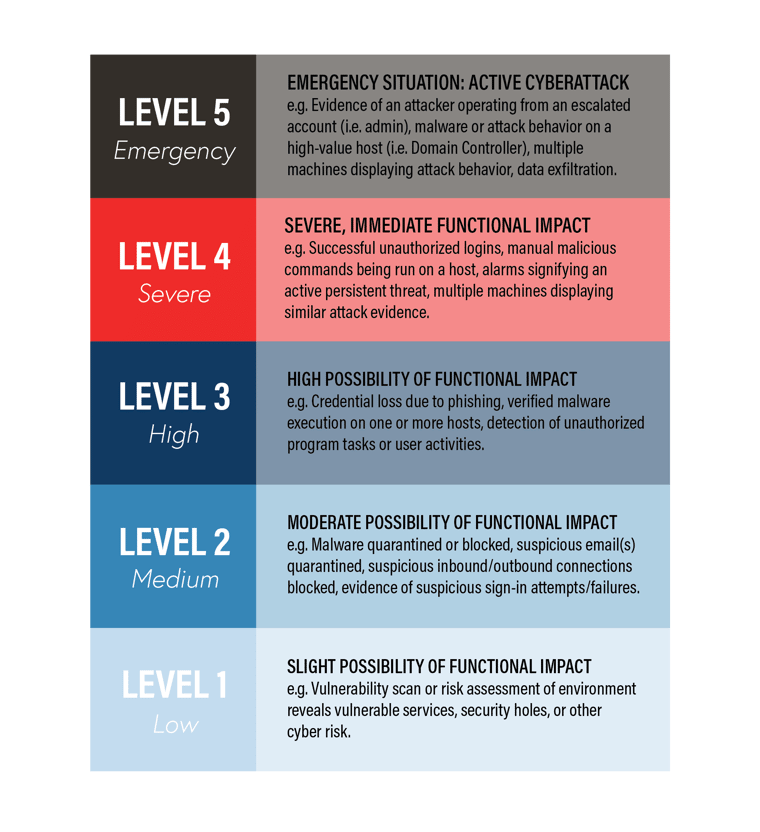
*Note: Incident triage and investigation will always be the necessary first step when categorizing an incident. Never guess the extent or impact of an incident when determining its severity.
An incident's "Functional Impact" is the measurement of the direct, ongoing impact it will have on an organization's business operations. The severity of an incident or the true functional impact may also be affected by the location of observed attack activity. In other words, if attack activities are observed in areas such as critical workstations, servers, or control systems, the incident may automatically escalate in severity to a four or five due to the impact those network devices have on both security and business function. These levels are simply a guide—every cyber incident is unique.
Consequences of a cyber incident
While “getting hacked” seems scary enough on its own, there are plenty of additional consequences that go along with it—including some you may not have realized.



What is Cyber Incident Response?
When a cyber incident occurs, Incident Response (IR) is the organized effort to investigate and manage the aftermath.
Depending on the nature of the incident, an IR may involve a range of actions including threat identification, in-depth investigation, vulnerability mitigation, legal actions, breach notifications, and more. The severity of the incident is often determined within the first few post-attack steps, which will define what type of IR actions may be required.
IR services are typically performed by security experts trained in cyberattack investigation techniques and procedures. Some security firms provide only IR and risk management services, some IT service providers offer IR as needed, and some cybersecurity service organizations provide both emergency services (like IR) and preventative security services. It’s best to do your research before the unthinkable happens, allowing you the time and resources to pick the right provider for your needs. Look for things like cybersecurity incident handling certifications, security engineer qualifications, and other indicators of expertise when vetting potential Incident Response providers.
Phases of Incident Response
Cyber IR is broken down into six phases, with one pre-incident phase, four intra-incident phases, and one post-incident phase.
1. Preparation
This is the pre-incident phase, meant to ensure you have an IR plan or know who to call in case an incident ever occurs.
2. Identification
This phase includes the investigation and forensics that identify the type of cyber incident, extent of the breach, and the status of the attack.
3. Containment
Containment sometimes happens concurrently with the identification phase, other times immediately following it. The affected systems are removed from production and locked down to prevent compromise from spreading further.
4. Eradication
After comprehensive investigation has finished, it’s finally time to remove, remediate, restore, and reset accordingly to eradicate the hacker’s access.
5. Recovery
Once the attack is over and the vulnerabilities have been fixed, you can transition back to business as usual.
6. Lessons Learned
In this final (and often-skipped) phase, it’s equally important to reflect on the incident as a whole, the steps taken during each phase, and the vulnerabilities discovered in order to move toward improving your organization’s security.
Creating an Incident Response Plan
Now knowing the 6 phases of incident response, you may see the value in having a pre-developed plan before finding yourself on the cusp of a cyberattack. Here are a few key steps when creating your organization’s IR plan:
-
Build your team
Beyond including leadership and key individuals, you should also think outside of your immediate organization. Do you have a member of your legal counsel to contact if a breach occurs? PR? Cybersecurity experts?
-
Assign responsibilities and authority
Determine who will have the authority to declare an incident and what roles other team members will play in the IR process.
-
Make contingency plans in the event of system failures
Find out from each department what concerns them about potential system failure—what would they lose? What services and tools are most critical for their daily operations? Create a plan for your organization in case one—or all—of these systems go down in an incident.
-
Establish communication plans
Who will be responsible for assembling the team, contacting necessary third-parties, and informing the rest of the organization? If email becomes compromised, create a plan for alternative bulk communications.
-
Define your plans & processes
When you’ve planned all you can and defined your processes, document them and ensure that all necessary parties have access to that documentation, understand it, and will be ready to follow it if the time comes.
-
Test & refine
Run a cyber fire drill if you can – this will allow you to find any flaws in the process you’ve built so far and continue to improve your emergency IR plan.
Proactive Security – Minimizing the need for IR
The cost of Incident Response services and breach recovery will always be more damaging than what it would have cost to invest proactively in cybersecurity. Here are the top proactive security tips from our cybersecurity experts:
1. Assess your current standing, identify where you need to go
Take a look at what security measures you already have in place and analyze how well they’re working. Is your current setup providing the best protection and best value for your organization?
If you’re not sure how to assess your security posture or are looking for a 3rd-party perspective to verify your findings, we’ve got your back.
2. Mitigate existing security holes
Scan your environment for existing security vulnerabilities and prioritize a list of necessary fixes, ranging from high priority to low.
Look for security-focused configurations (or lack thereof), hardware and software patches, vital updates, and other “holes” in your network’s security protection. Continue scanning even after your first list of fixes have been completed, as new vulnerabilities emerge every day.
3. Train your teams
The common statistic is that over 90% of successful breaches can be attributed to human error. Whether that means clicking on a link in a phishing email, downloading and launching a suspicious file, accidentally giving away legitimate credentials, or otherwise opening up your network to unwanted attacks, one thing is clear: security awareness is vital in organizations of all sizes, and security ignorance is a #1 threat.
At minimum, we recommend providing phishing testing and training to everyone in your organization, if not implementing a full Security Awareness Training program to ensure every member of your teams are prepared to both identify and avoid common cyberattacks.
4. Add what’s missing
After you’ve determined your current security standing, fixed the high-priority vulnerabilities, and informed your users, now is the time to start looking at some of those shiny new cybersecurity tools! But not so fast – there are so many available and the industry is packed with constantly-emerging buzzwords, new technology, and more confusion… so how do you know what to choose?
Keep it simple by looking to cover the four basics of cybersecurity: Prevention, Protection, Detection, and Response. Some of your existing security tools may already address some of these components. This makes it easier to search for what you’re missing and find a solution that fits your organization’s needs.
All in all, it can be overwhelming to plan for, or recover from, a cyber incident. Reach out to a cybersecurity expert if you'd like a hand in applying these tips to your organization's network.