Cyber criminals have no off season. Here are some of the most popular attack tactics and techniques your organization should be prepared to defend against.
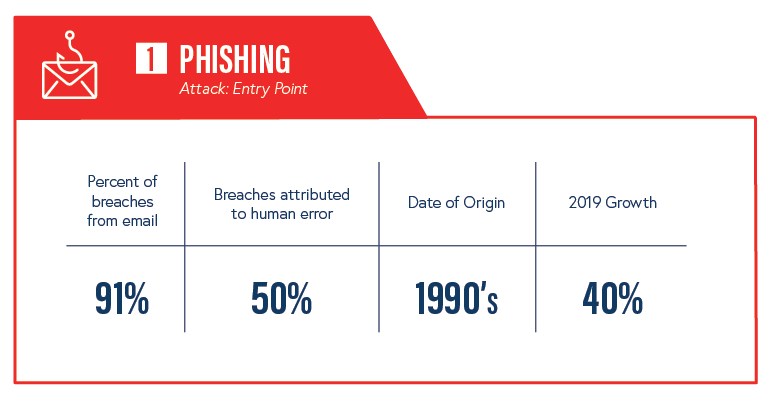
1. Phishing
One of the most infamous cyberattack tactics.
You have probably heard of phishing, and likely even experienced some variation of a phishing attack in either your personal or business communications due to its rising popularity.
If you’ve been an active email-user for a while, you know that this technique isn’t new—despite its recent surge in usage.
Phishing can be traced back to the early 1990’s, when a group of hackers used AOL messaging to spam and trick users into handing over their information. After messenger scams caught on and the public became less susceptible to the trick, cyber criminals saw an opportunity and switched to email. By 2003, some of the now-classic phishing techniques began to arise—leading to a new era of sophisticated phishing. Fraudulent lookalike domains, web-designed email messages complete with legitimate logos, and altered URLs became the standard for successful phishing attacks. Then came Spear Phishing and Business Email Compromise (BEC), which have quickly gained in popularity—and success—due to the extensive research and sophisticated techniques attackers have adopted.
Today, the bad guys use phishing to accomplish one of the following goals:
- To trick the recipient into handing over money, information, or something else of value. A “one-and-done” approach.
OR
- As an entry-point to compromise their victim and begin a larger-scale attack.
Despite the resources available to the public about the common indicators of a phishing email , this tactic is sophisticated, successful, and an easy first-choice for attackers to compromise their victims.
2. Command & Control
The age of cyber warfare is now.
No, we’re not talking about the military tactic—although experts declare cyber warfare is on the rise and already affecting communities within the United States.
Cyber Command & Control, or C2, is a technique used within cyber attacks to establish a connection between the attacker network and the victim network. C2 servers essentially act as an attacker’s “Headquarters.” These servers are often used to send commands to compromised systems (read: the computer that was hacked) and receive stolen information in return.
Once an attacker has compromised their target and gained access—either through exploiting open vulnerabilities, delivering malware via phishing, or another method—they can utilize the C2 technique to begin an advanced attack. C2 servers can send commands to bypass built-in security on a computer, deliver malicious code or files, and steal data.
3. LOLBin
Lol-what?
LOLBins—Living Off the Land Binaries—are non-malicious binaries that cyber criminals will use in their attacks to hide malicious activity on a system. The idea behind the LOLBin technique is that attackers can find legitimate, benign, and usually built-in executables present within an operating system, and then use those binaries to achieve malicious goals without relying on malicious code or files.
Using LOLBins, attackers can “live off the land” or use a machine’s resources against itself to progress their attack.
Check out this recent example of LOLBin attacks in the news.
4. Credential Harvesting
A constant in the threat landscape.
Things are always changing for cyberattacks and cybersecurity, but one thing remains true: passwords (or credentials) are a valuable resource—and users are always going to be at war with cyber criminals over the security of their credentials.
The credential harvesting tactic can be used in different stages of a cyberattack:
- either as a point of entry, harvesting credentials through a phishing campaign and then using those credentials to gain access
or
- within a compromised system to escalate privileges and gain access to other areas within the network.
Credential harvesting tools exist, like one called Mimikatz, that attackers use on compromised computers to harvest records of all passwords stored in memory on the computer.
5. Brute-Forcing
Inelegant, but effective.
Keeping with the theme of credentials, brute force attacks are a trial-and-error method used by attackers to repetitively guess account credentials using automated software. Brute-forcing is a relatively unsophisticated attack, relying simply on “brute force” to get in.
Using resources like open source password breach records, common combinations of letters and numbers, and even lists of dictionary words, attackers can automate consecutive “guesses” in an attempt to crack an account. The method has been prevalent since the inception of computing devices, and is not likely to slow down or go away anytime soon in our digital age.
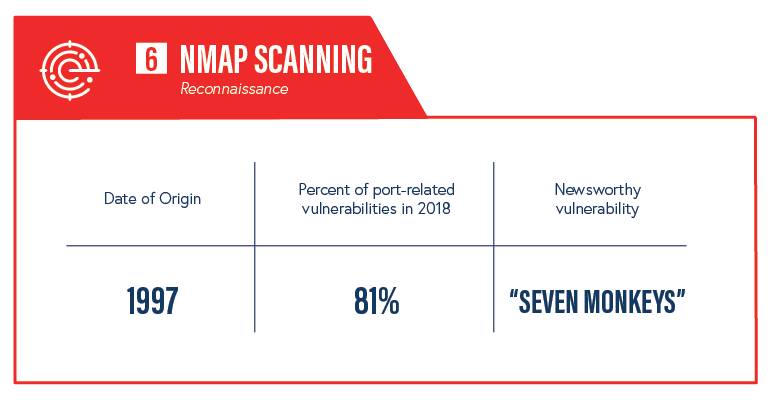
6. NMAP Scanning
How network discovery leads to easy exploits.
Network scanning isn’t malicious by nature, but it provides an easy route for attackers to gather information about a target and develop a plan of attack.
The NMAP scan was developed in 1997 as a resource for network security professionals for network discovery, port scanning, OS and version detection, and more. Access to this information is also valuable for attackers looking for information about a target because it can be used to strategize an attack plan.
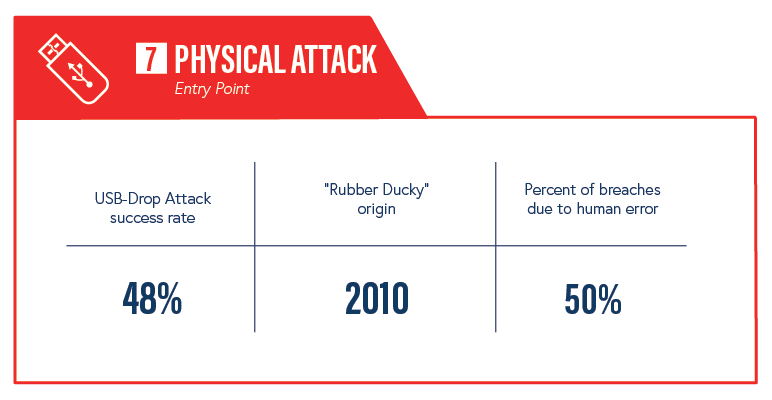
7. Physical Attacks
Where cyber meets physical.
A cyberattack isn’t always the result of a distant “bad guy” on the other side of a screen—some stages of an attack can take place in person. Not only that, but new cyber-physical hybrid attacks are on the rise, combining digital attack vectors like accounts, operating systems, and the like with physical techniques and onsite hacking.
Have you ever been given the following advice?
If you find a USB drive (thumb drive, flash drive), don’t plug it in.
This advice stems from a cyber-physical attack tactic which started gaining popularity in 2010 with the invention of the USB “Rubber Ducky.” The Rubber Ducky hacking tool, along with similar tools, gave criminals an easy way to take the ease and portability of a “flash drive” and use it to hack. The Rubber Ducky uses keystroke injection technology to run malicious code quickly and easily on a device—serving as an unsuspecting way to steal passwords, drop malware, install “backdoors” into systems, exfiltrate data, and more. Attackers can leverage USB attacks by leaving USB drives behind and waiting for users to pick them up, or by entering a physical establishment and using social engineering tactics to gain access and plug the drives into systems themselves.
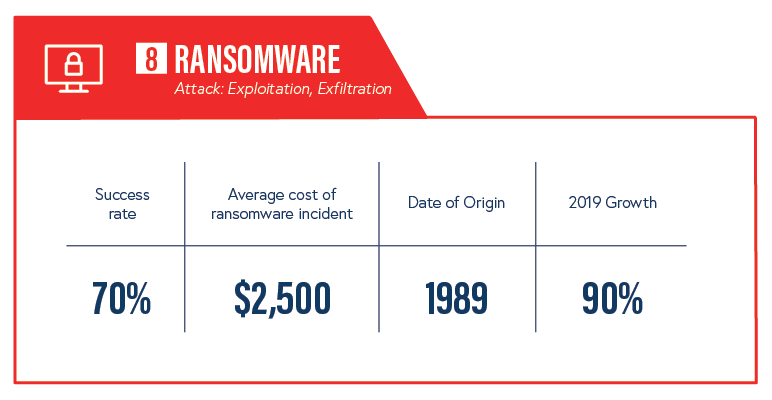
8. Ransomware
Turning hacking into profit.
Like phishing, ransomware is an attack tactic that doubles as a cybersecurity buzzword—constantly making the news thanks to its popularity among cyber criminals. Demanding a ransom was a tactic invented to profit off kidnappings, now criminals can kidnap your digital data and use the same tactic to make a profit.
Attackers will deliver ransomware through a variety of routes—phishing emails, infected sites, compromised machines—but the strategy is always the same post-delivery: encrypt files, demand a ransom, get paid.
It’s a simple attack technique, which is why attackers like to use it as a quick and easy way to make money off hacking.
These are your opponents—what’s your lineup?
Stay tuned to our Cyberattack Series to learn more about these attacks and how to be proactive in defending against them.