The battle of cybersecurity is constantly advancing.
As hackers move to more complex, focused efforts, their strategies have changed and the threat has increased.
One of these strategies, advanced persistent threats (APT), is a customized, focused attack that is difficult to detect and nearly impossible to prevent. So how do companies of all sizes protect their networks and keep their customer data safe?
What is an advanced persistent threat?

Rather than using a broad approach, APTs are designed with a specific target in mind. Because of this, they are customized to the system, having investigated the security measures in place and been designed to capitalize on those weaknesses. They often gain access to the network through a phishing attempt or a zero-day exploit.
The goal of an advanced persistent threat is to achieve ongoing access to a system, rather than a quick entry and exit. This allows them to continually monitor activity and steal data, company information, and more.
How do advanced persistent threats work?
One of the primary ways advanced persistent threats gain access is through valid network credentials. An attacker will use employee access obtained through phishing attempts or other means. This helps them to remain undetected as they move throughout the company’s systems and continue with their attack.
These threats have multiple phases that add to their complexity and make it even harder for security technology to detect their presence on the system.
The phases of an advanced persistent threat (APT):
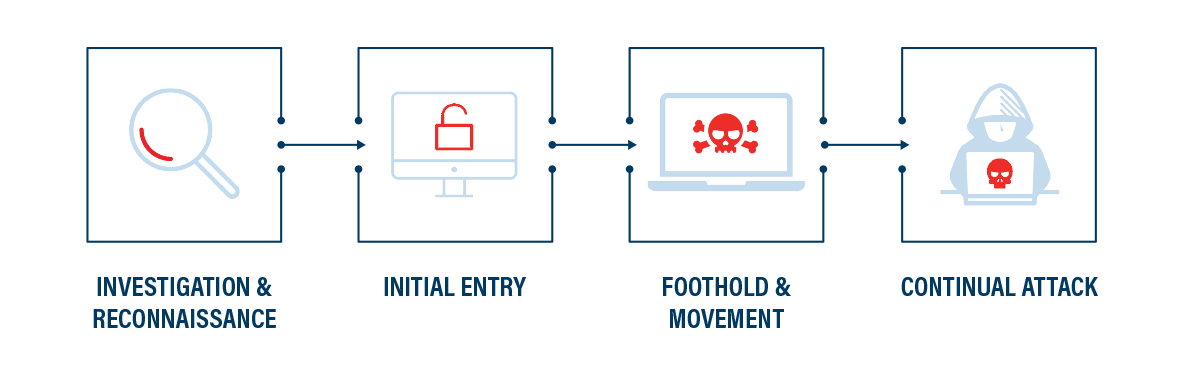
- Investigation and reconnaissance: Due to the targeted nature of these attacks, the process begins by using either external or internal sources to learn about the network, its defenses, and potential holes or entry points.
- Initial entry: Once the advanced persistent threat finds those weaknesses, they exploit them and make their initial attempt at access.
- Foothold and movement: Once access is achieved, the primary goal is to remain undetected on the system and gain a stronger foothold.
- Continual attack: At this point data is collected and passed back and forth from the attacker’s network. The threat will remain on the network until it is detected, which could be months or even years. The persistence of the threat is clearly seen.
The advanced, multi-phase nature of these attacks means a more advanced solution is necessary to fight back.
Signs of an Advanced Persistent Threat
These threats are difficult to detect, and their success relies on remaining undetected. However, there are often warning signs that can help your company fight back.
- Strange user behavior. If a verified user has network behavior that is out of the ordinary, this can be a sign of an attack. An example of this might be logging in multiple times in the middle of the night.
- Large movement of data. If there is a sudden increase of activity on the database, such as large amounts of data being moved throughout the network or to an external server, this could be a sign of an APT.
- Multiple backdoor trojans. If you find multiple backdoor trojans, these are used to gain and maintain access across the network.
- Unusual data files. As data is transferred off the server, strange data files are often created to streamline the process.
Your antivirus is not enough.
As the threat of APTs continues to increase, your company might be open to a data breach without additional security in place. The highly organized, sophisticated nature of APTs threatens that security because your antivirus, even a next-generation antivirus (NGAV), isn’t equipped to fight these advanced, and often fileless, threats.
Because the APTs often enter the network through legitimate sources or through an intense search for weaknesses, they are hard to prevent and even harder to detect. Instead, you need a system that can detect abnormal behavior from credible users on the system.
The multiple phases of an advanced persistent threat work slowly and tactfully, looking to avoid detection and maintain control of the network. This allows them to move undetected across the network and achieve their goals without being noticed by traditional security methods.
But one technology, Endpoint Detection & Response (EDR), supports your security team in the fight against these advanced attacks.
How does EDR fight advanced persistent threats?
EDR equips your team to detect and fight advanced persistent threats as it constantly analyzes endpoint activity on the network, tracks behaviors, and consolidates the data for more efficient investigations.
EDR fights advanced threats by using algorithms and behavioral analysis to track user activity in real time. It triggers alerts based on unusual activity, like multiple logins late at night, or large movements of data on your network, so you can catch the threats quickly instead of allowing them to remain on your network for months or even years.
It is constantly monitoring your network activity so you can rest assured that anything unusual will be brought to light, giving you the opportunity to fight back before additional damage is done.
EDR supports your security team by consolidating the data into reports that can be analyzed by security experts—it streamlines how the alerts and attack data are managed. It also works with your antivirus and other security tools to fight against even the most advanced attacks.
The time to protect is now.
The first advanced persistent threats were high-scale and targeted, frequently used by large organizations, governments, and crime syndicates. However, that’s no longer the case. Hackers at all levels are now creating more sophisticated, focused attacks. No matter the size of your company, it’s important to be aware and put systems in place to protect your network from these types of attacks.

