Learn one method used by attackers to gain a foothold in a network and escalate their privileges.
One of the more common perceptions of cyberattacks is that “getting hacked” usually involves malicious software or files. The truth is, cyber attackers can easily gain traction in an attack without using any malicious software at all. One of the ways they can do this is by using your computer against itself.
Enter defense evasion and privilege escalation—namely LOLBins and User Account Control (UAC). Attackers’ goals—once they have initiated an attack—are mainly to avoid being stopped by existing security defenses and to escalate their user privileges. Escalating privileges within a network is key for attackers' progress, allowing them to do more, access more, and, to put it simply, cause more damage.
LOLBins – what are they?
LOLBins—Living Off the Land Binaries—are non-malicious binaries that cyber criminals have discovered can be used to hide their malicious activity within a system and evade cyber defenses. The idea behind the LOLBin technique is that attackers can find legitimate, benign, and usually built-in executables present within an operating system, and then use those binaries to achieve malicious goals without relying on malicious code or files.
Using LOLBins, attackers can “live off the land”—as the name suggests—and use a machine’s resources against itself to progress their attack.
LOLBins are Microsoft-signed files, meaning they are either native to the Operating System (OS) and come pre-installed, or are available from Microsoft (i.e. a Microsoft program or add-on). Despite being legitimate (and well-intentioned) files, these binaries can be exploited by an attacker and used in an attack.
LOLBins can provide a range of features and abilities to the savvy cyber criminals who discover them—ranging from executing code, to performing file operations (downloading, uploading, copying, etc.), to stealing passwords.
One common LOLBin is Regsvr32.exe, sometimes called the Squiblydoo attack. “Regsvr32” is a standard utility that aids in registering and unregistering system controls. To put it simply, it’s a function used primarily by advanced users to complete computing tasks like adding programs to the Windows Registry. While the everyday computer user or device owner is not likely to manually run this command in their day-to-day computing, Regsvr32.exe is still a fundamental 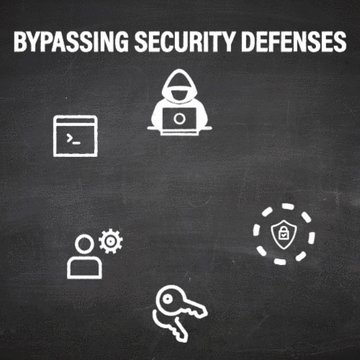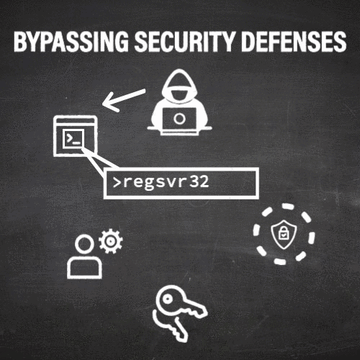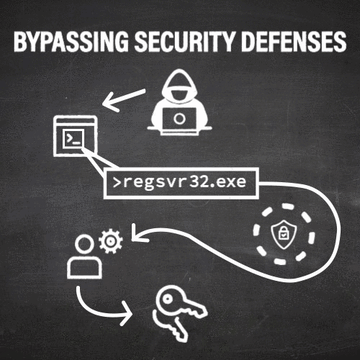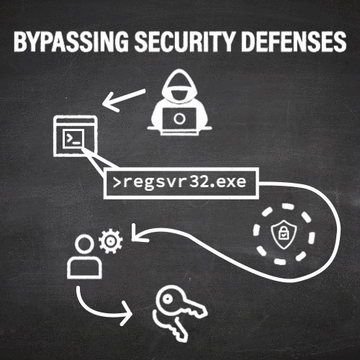 binary and a built-in function on Windows devices.
binary and a built-in function on Windows devices.
Because Regsvr32 is present on every windows machine and has inherent code-running capabilities, cyber criminals like to use it to bypass a computer’s existing Application Whitelisting and execute code that would otherwise be blocked from running. With this ability, attackers can bypass existing security defenses (such as Application Whitelisting and User Account Control) and then run other variations of code to escalate their privileges on the machine.
Why attackers want to bypass User Account Control (UAC)
User Account Control (UAC) is another built-in security feature of Windows devices that acts as a roadblock to cyber attackers. UAC helps separate the capabilities of an administrative user from those of a standard, non-admin user.
Have you ever tried to install, open, or change a program and been faced with this popup box?
That’s UAC in action. These credential prompt boxes keep standard users from being able to make changes to their system that could impact their security or otherwise put their device at risk, leaving the responsibility to IT or security admins to make the right call.
It can be frustrating when you’re trying to install an application on your work laptop, but that means it’s doing its job. Having UAC in place helps prevent attackers from installing programs or running code that requires administrative-level permissions.
With the help of LOLBins, however, attackers can sneakily bypass UAC and escalate their user privileges without having access to administrative credentials. With “stolen” admin capabilities, an attacker can run programs or malicious code, use programs to steal legitimate credentials, and more.
The attack in action
In the short video below, Infogressive Engineer Will demonstrates the use of regsvr32.exe to evade Application Whitelisting and then the UAC bypass tactic in action, as well as some of the ways to prevent and detect this type of cyberattack.
Cybersecurity Game Plan
Offense
If an attacker was present on your network and and using LOLBins to bypass security, strong detection solutions have your back.
With a combination of Endpoint Detection & Response (EDR) and expert Log Analysis, signs of an attack would be detected and alerted upon immediately.
EDR actively tracks and analyzes user behavior on computers—it knows what’s “normal” and what’s out of the ordinary. When an attacker bypasses security or runs a program that a regular user wouldn’t be accessing, that creates an alert for security analysts to investigate and identify the ongoing attack.
Adding EDR’s capabilities to traditional SIEM monitoring and alerting, backed by a 24x7 Security Operations Center (SOC) allows you to rest assured that even the sneakiest attack tactics can be identified and stopped before the damage is done.
Defense
Prevention is still possible for this type of attack—there are multiple areas where an attacker could be stopped before reaching their end goal, and layered cybersecurity is an effective way to cover those bases.
Starting with an effective malware prevention solution, you can stop an attacker in their tracks. If your AV can detect and block attacks running in memory, then an attacker would be out of luck trying to use a LOLBin like Regsvr32.exe to bypass your security.
But why wait until the attacker is already in your network? With a combination of a Next-Generation Firewall configured to secure “open doors” and exploitable vulnerabilities, strong email security to block attacks entering via phishing or spam, and well-trained users who know how to identify cybersecurity risks, you can prevent the attacker from getting on the computer in the first place.
Tune in to our Cyberattack Series to learn more about the top attacks you face in today’s threat landscape and some of the techniques used by your cyber adversaries.

