What is the MITRE ATT&CK Product Evaluation?
The ATT&CK evaluation framework, according to MITRE, is a new development that provides a transparent, customer-centric approach to product evaluation for cyber detection software and solutions.
The ATT&CK evaluation framework is intended to help the different stakeholders in Detection & Response (“defenders and vendors”) work together to improve product capabilities for a more secure industry.
What does ATT&CK look for?
The ATT&CK evaluation employs two attacks to machines running an endpoint detection solution and evaluates the ways the solution detects and reacts to attack techniques. This method balances both the data collected by the solution and what it does with the data, rather than just measuring coverage or block rate. The MITRE ATT&CK framework evaluates the following factors to measure the effectiveness of a detection product:
- Identification of malicious activities.
- Level of relevant data collection on malicious activities.
- Level of context gathered around malicious activities.
- Degree of enrichment provided to the end user.
- Speed and ease of gathering relevant information and artifacts about the malicious activity.
Each product is evaluated on the previous qualifications by identifying the main detection methods and the modifier detection types employed by the detection solution in response to the attack.
Here’s a brief look at the different detection methods charted in the ATT&CK framework:
- None: Solution unable to detect activity.
- Telemetry: Solution collects minimally processed data and identifies malicious activity.
- Indicator of Compromise: Solution identifies activity based on reputation.
- Enrichment: Solution captures telemetry data and enriches it with additional activity data, such as evidence, suspicion, or path of malicious operation.
- General Behavior: Solution creates an alert for activity based on a rule, not including details on the specific activity.
- Specific Behavior: Solution creates an alert for activity based on a specific rule for the exact technique being used.
In addition to the main detection methods, the following modifiers are also analyzed:
- Delayed: Solution triggers a detection alert after a significant period of time, rather than in real time.
- Tainted: Solution triggers a detection alert by association.
- Configuration Change: Solution triggers a detection alert when there is a configuration change.
For a more detailed look at detection methods, their definitions, and examples, check out this blog.
Results — What This Means for You
While MITRE’s product evaluation framework does not assign scores, rankings, or ratings to the products tested, it does provide a comprehensive look at the strengths and weaknesses of each detection software or solution.
We’re proud to say that our solution not only held up against the enterprise vendors, but it also delivered some of the best performance on the charts. With Infogressive’s Managed EDR service, your network is protected by a team of experts that stay ahead of the threats. Our service delivers the most coverage, the most correlation, the most real-time detections, and zero delays.
See More
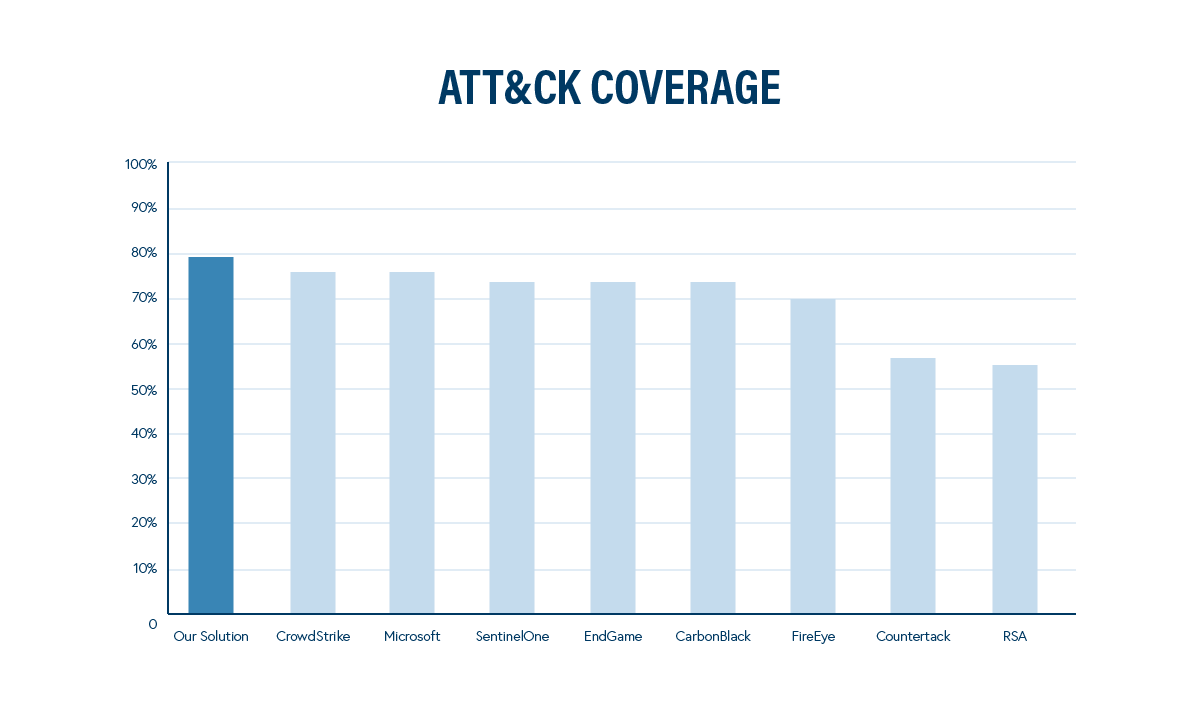
Our solution demonstrated the most coverage across all phases of the evaluation, proving to be the most extensive and most consistent.
Understand More
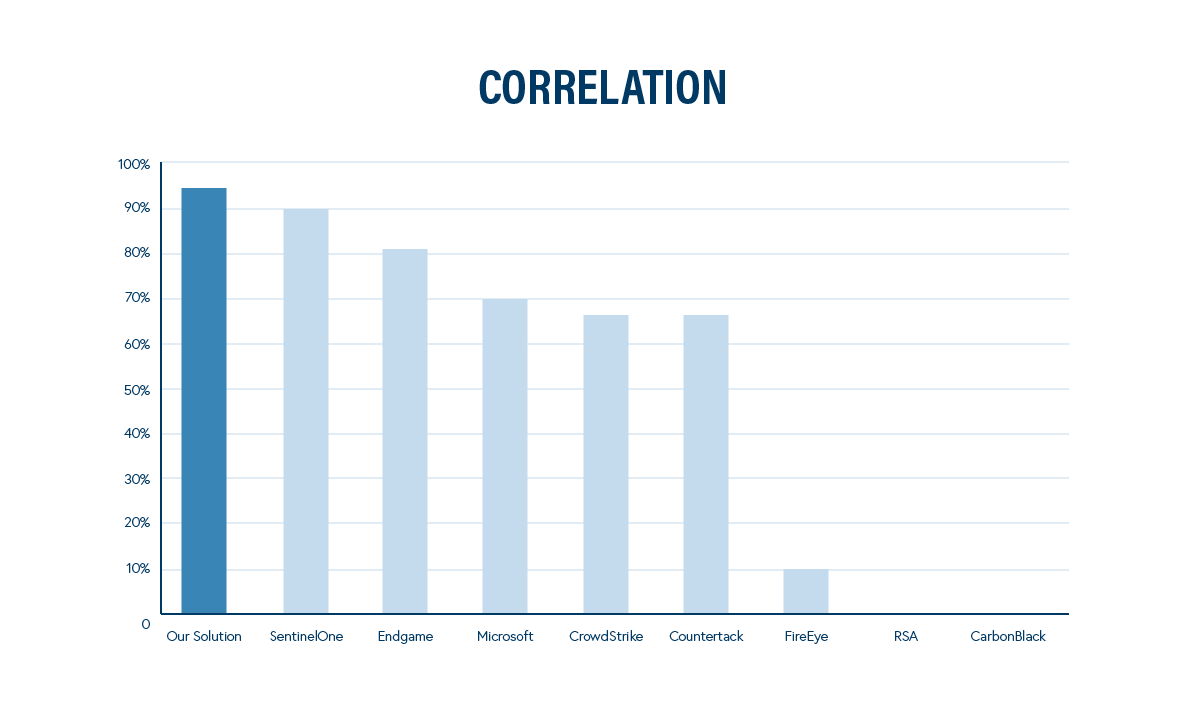
The most correlation means that events taking place in your network will be easier to understand and quicker to evaluate—making it that much faster to move from detection to response.
Stop More
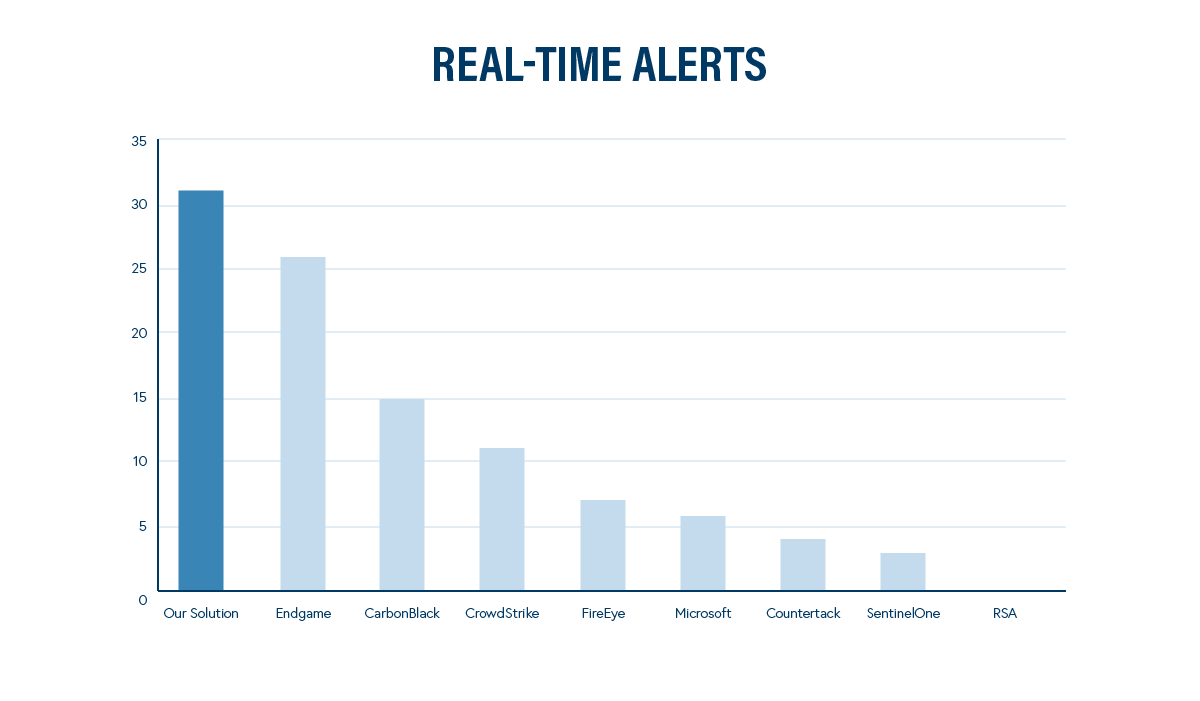
The most real-time alerts are fully contextualized, enriched, and automatically generated without delays, so threats can be stopped quickly before harm is done.
For a look at the raw results, visit the MITRE ATT&CK Evaluations.
Pair the best EDR solution with a dedicated team of cybersecurity experts and 24x7 Security Operations Center (SOC) support. Dominate detection.

