What’s your game plan if prevention fails?
As attack techniques continue to advance, it’s crucial to have a plan in place. Last year, 77% of successful attacks used fileless attack techniques, something even the best antivirus solution can’t track or prevent.

Endpoint Detection & Response (EDR) can provide answers when an attack makes it through your defenses—and help you fight back.
What is EDR?
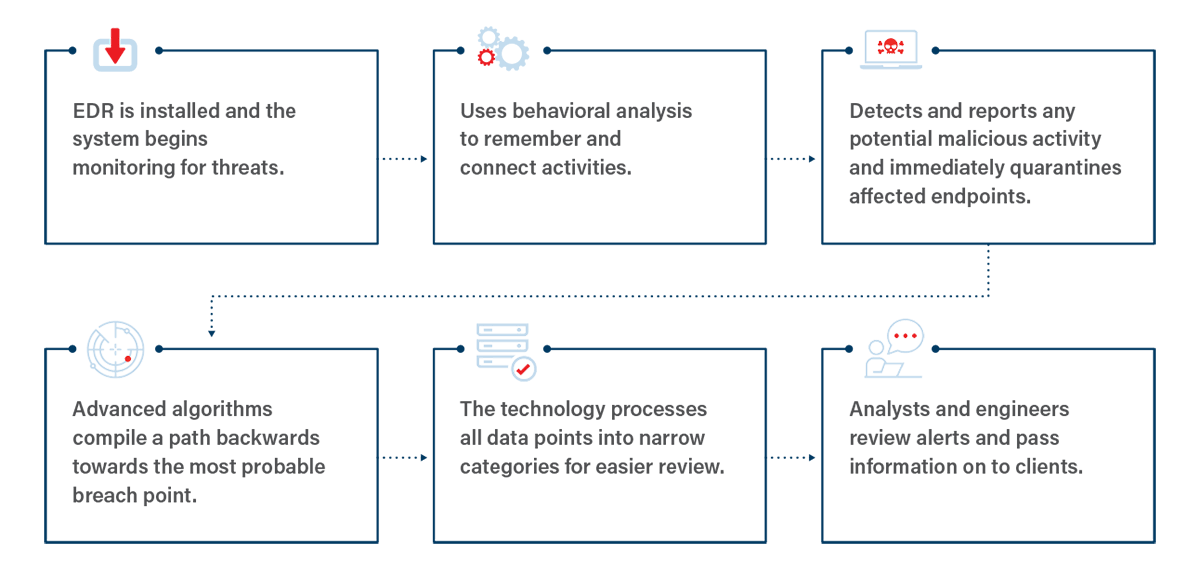
Endpoint Detection & Response (EDR) technology monitors endpoints and proactively hunts for threats through advanced algorithms and behavioral analysis. It gives greater visibility into endpoint activity, tracks the path of an attack, and consolidates data for more efficient investigations.
EDR uses advanced algorithms to monitor endpoint activity.
EDR uses behavioral analysis to analyze and connect the activity of individual users on your system. If an attacker is on your network, it can “sense” behavior that is out of the ordinary for a given user. A lack of endpoint security opens your company to many advanced attacks, making it imperative to find a solution like EDR that can successfully handle these threats.
EDR consolidates the data and tracks the path of attack.
With so much endpoint and network data, if there is a breach, it can be nearly impossible to sift through to manually detect the path of the attack or its point of entry. EDR consolidates all data points into narrow categories called MalOpsTM, short for Malicious Operations. Traditional methods are often limited in the depth of information you receive after an attack, but EDR uses MalOpsTM to tell you when it happened, how it entered, and its path.
How Does EDR Software Work?
EDR starts working as soon as it is installed on your system. The technology can then funnel the data from sensors on your endpoints back to your Managed Security Service Provider’s (MSSP) main console, so alerts can be monitored and reported.
That’s where the behavioral analysis comes in. Once EDR is installed, it tracks user data, so it can detect behavior that is out of the ordinary and notify you of possible breaches.
If a threat of malicious activity is detected on the network, EDR immediately quarantines the affected endpoints to disrupt the attacker’s lateral movement. The algorithms then create a path back to the most probable entry point onto the network. This data is consolidated into MalOpsTM to be reviewed, alerting the main console.
What Are the Benefits of EDR?
Because of its thorough, proactive approach, EDR can have a dramatic impact on the way that your team fights potential threats so you can rest assured that your network is safe. But network safety isn’t the only benefit.
EDR saves time during investigations.
Rather than having to manually parse through alerts and compare them to other data, EDR consolidates the data, saving enormous amounts of overhead and time while protecting the company. These MalOpsTMmake it easier for analysts and engineers to quickly review the attack data, which, in turn, reduces the overall time and cost of post-breach analysis.
EDR gives back control of endpoints.
According to a report from the IDC (International Data Corporation), 70% of successful breaches start on endpoint devices. Because of the number of endpoints on modern networks, it’s increasingly difficult to fight against advanced attacks that enter through these endpoints. Investing in endpoint detection gives back control so you can protect your company knowing you’re well-equipped against the large number of endpoint variables.
Is EDR right for my company?
As potential threats continue to increase and the intelligence of hackers continues to grow, it’s even more important to find new ways to protect your network and always be on the hunt for breaches.
While EDR can make a difference for any company, often the most dramatic impact is on companies who are unable to invest in an in-house security team but who struggle to find the capital to recover if there is an incident.
As you consider investing in Endpoint Detection & Response (EDR), ask these questions:
- How quickly can we find and catch an attack?
- Is our customer data safe if there is a breach?
- Does our team have the capacity to handle these threats?
- Do we have visibility into network activity?
- Are our endpoints protected sufficiently?
- How do we know if we’ve already been breached?
There is too much at risk not to have a solution in place if an attack makes it past your line of defenses and has access to your network and customer data. Don’t let advanced threats keep you up at night. With EDR, you can sleep soundly knowing that you have a plan in place if your prevention fails.