Can Intune deploy my Group Policy settings?
The likely answer is yes! We’ve helped many organizations transition and manage their group policy with our Digital Workspace Deployment solution using Intune. Microsoft Endpoint Manager (a.k.a. Intune) can evaluate your group policies to determine if they can be translated to the cloud.
You can check for yourself in 3 easy steps:
1. Export your GPO settings from your group policy management console. Right-click a GPO and select “Save Report…” as the XML file type
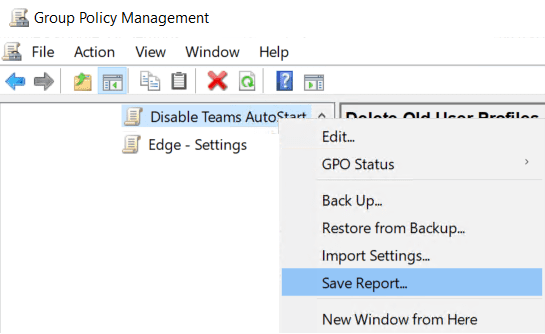
2. Go to your Microsoft Endpoint Management console: Devices > Group Policy analytics (preview) > Import
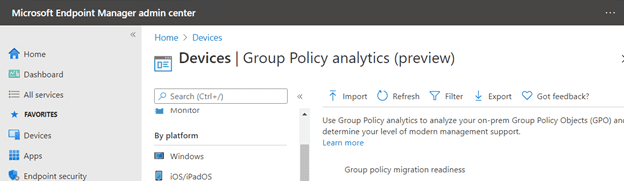
3. Import the XML files you exported from the GPAC.
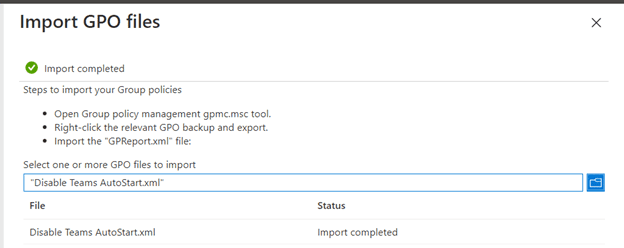
Now you can view which GPO settings can be translated into Intune configuration profiles. Click the MDM Support percentage value to view the specific settings that can or cannot be translated.
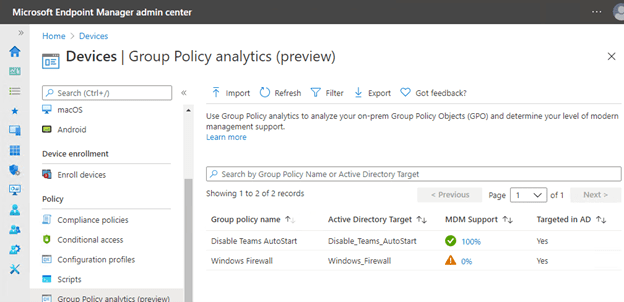

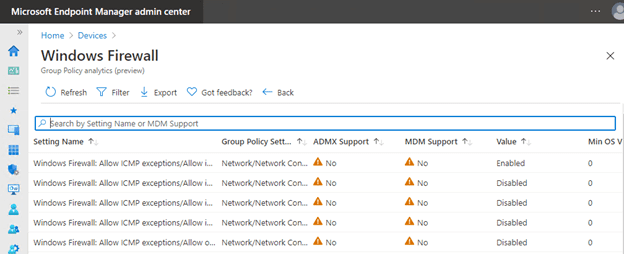
Some group policy settings have ADMX support and can be configured using Intune.
Not all group policy settings are supported, but Intune may have cloud-appropriate settings for the same component.
Intune Makes it Easy
Intune contains many settings that can be configured right out of the box. Administrative Templates are built into Intune and don’t require any customizations, including using OMA-URI.
As part of your mobile device management (MDM) solution, use these template settings as a one-stop shop to manage your Windows 10 devices.
The Settings catalog is in preview and lists the settings you can configure all in one place. This feature simplifies how you create a profile and see all the available settings. Use the settings catalog as part of your (MDM) solution to manage and secure devices in your organization.
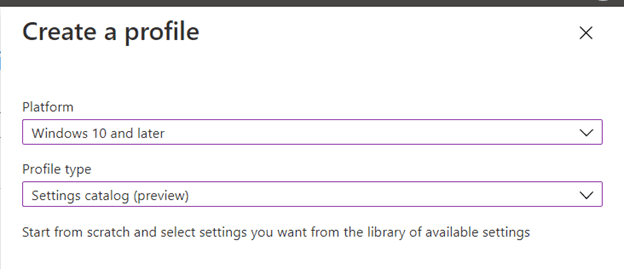
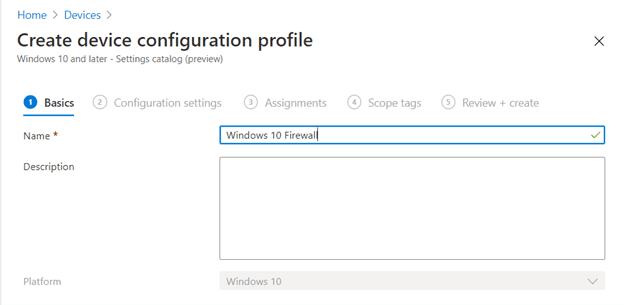
For example, we can create a Windows 10 Firewall profile:
Go to the Microsoft Endpoint Management console:
Devices > Configuration profiles > + Create profile
Platform – Windows 10 and later
Profile type – Settings catalog (preview)
Basics > Name – Windows 10 Firewall
Next: Configuration settings > +Add settings
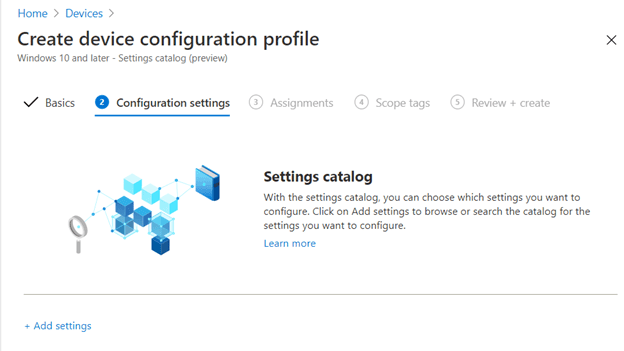
Select the Firewall category and enable the desired settings
Additional Configurations
Intune can also deploy group policy settings that are not included out-of-the-box, using a procedure called ADMX file ingestion.
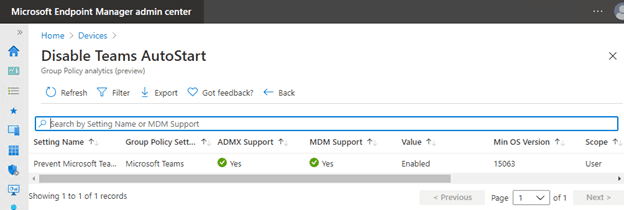
For example, if we want to replicate the GPO setting “Prevent Microsoft Teams from starting automatically after installation” with Intune:
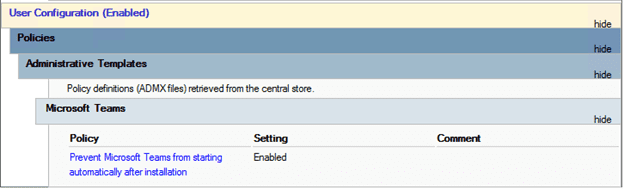
Go to the Microsoft Endpoint Management console and create a Configuration profile
Devices > Configuration profiles > + Create profile
Platform – Windows 10 and later
Profile type – Templates
Template name – Custom
Next
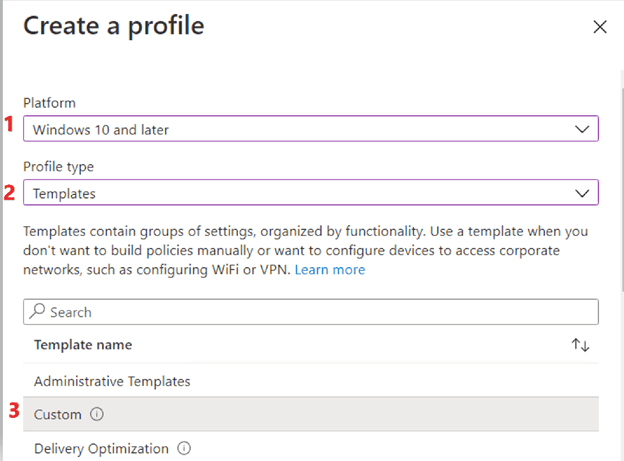
Basics > Name – Disable Teams Autostart
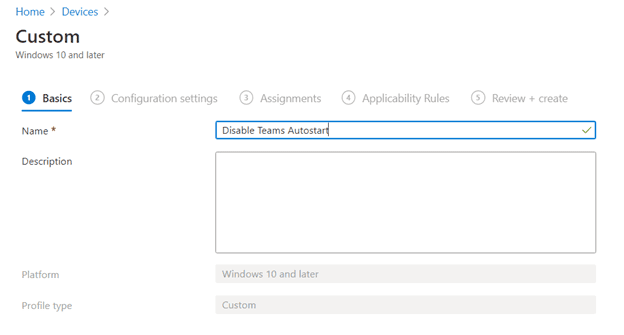
Next - Download the Teams ADMX file from Administrative Template files (ADMX/ADML) and Office Customization Tool for Microsoft 365 Apps for enterprise, Office 2019, and Office 2016
Download Administrative Template files (ADMX/ADML) and Office Customization Tool for Microsoft 365 Apps for enterprise, Office 2019, and Office 2016 from the Official Microsoft Download Center
Open teams16.admx with a text editor such as notepad++
To ingest an ADMX file, we must use the following OMA-URI format:
./Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/{AppName}/{SettingType}/{AdmxFileName}
OMA-URI stands for Open Mobile Alliance Uniform Resource Identifier
AppName – This should be the name of the application “Teams16”
SettingType – This will be “Policy” when doing ADMX ingestion
ADMXFileName – This can be anything, such as “Teams16ADMX”, but the meaning should be obvious to your peers
Devices > Configuration profiles > + Create Profile
Platform: Windows 10 and later
Profile type: Templates > Custom
Basics – Name: Teams
Configuration settings > Add
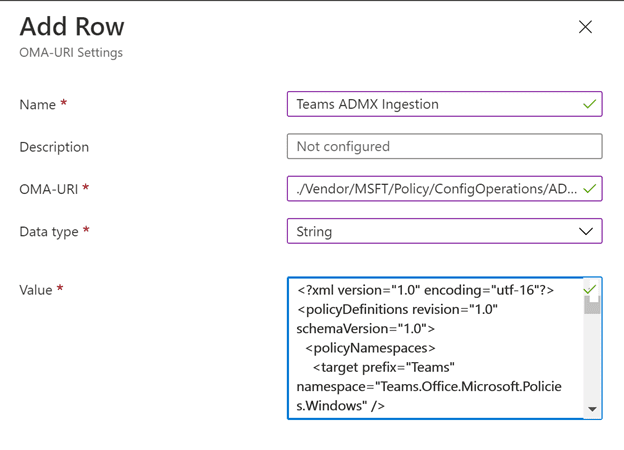
Name: Teams ADMX Ingestion
OMA-URI:
./Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/Teams16/Policy/Teams16ADMX
Data type: String
Value: paste in the text of the teams16.admx file you opened with your text editor
Now let’s build the setting OMA-URI for our custom profile:
The settings OMA-URI must use the following format:
./User|Device/Vendor/MSFT/Policy/Config/{AppName}~{SettingType}~{CategoryPathFromADMX}/{SettingFromADMX}
We can fill in some of the variables from the information found in the ADMX file.
The class is “User” and is found in the ADMX file.
The AppName “Teams16” will be the same name we used in our ADMX ingestion OMA-URI
The setting type “Policy” is the same as used in our ADMX ingestion OMA-URI
The category “L Teams” is found in the ADMX file
The value will be “<enabled/>”
The complete setting OMA-URI will look like this:
./User/Vendor/MSFT/Policy/Config/ Teams16~ Policy ~L_Teams/ Teams_PreventFirstLaunchAfterInstall_Policy
Teams16.admx:
<?xml version="1.0" encoding="utf-16"?>
<policyDefinitions revision="1.0" schemaVersion="1.0">
<policyNamespaces>
<target prefix="Teams" namespace="Teams.Office.Microsoft.Policies.Windows" />
<using prefix="windows" namespace="Microsoft.Policies.Windows" />
</policyNamespaces>
<resources minRequiredRevision="1.0" />
<categories>
<category name="L_Teams" displayName="$(string.L_Teams)" />
</categories>
<policies>
<policy name="Teams_PreventFirstLaunchAfterInstall_Policy" class="User"
displayName="$(string.String_Teams_PreventFirstLaunchAfterInstall_Policy)"
explainText="$(string.String_Explain_Teams_PreventFirstLaunchAfterInstall_Policy)"
key="software\policies\microsoft\office\16.0\teams"
valueName="preventfirstlaunchafterinstall">
<parentCategory ref="L_Teams" />
<supportedOn ref="windows:SUPPORTED_Windows7" />
<enabledValue>
<decimal value="1" />
</enabledValue>
<disabledValue>
<decimal value="0" />
</disabledValue>
</policy>
<policy name="String_Teams_SignInRestriction_Policy" class="User"
displayName="$(string.String_Teams_SignInRestriction_Policy)"
explainText="$(string.String_Explain_Teams_SignInRestriction_Policy)"
presentation="$(presentation.Teams_SignInRestriction_Policy)"
key="software\policies\microsoft\office\16.0\teams">
<parentCategory ref="L_Teams" />
<supportedOn ref="windows:SUPPORTED_Windows7" />
<elements>
<text id="RestrictTeamsSignInToAccountsFromTenantList"
valueName="restrictteamssignintoaccountsfromtenantlist" required="true" />
</elements>
</policy>
</policies>
</policyDefinitions>
So, putting it all together…
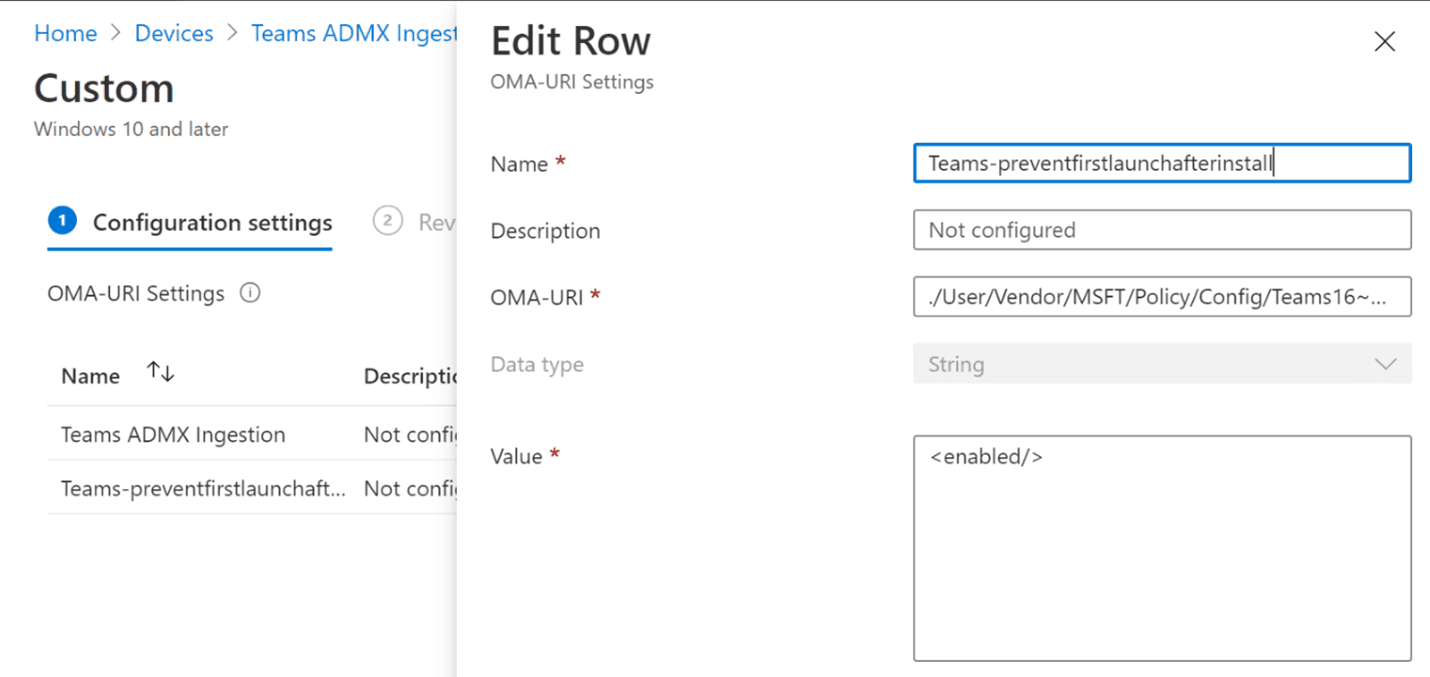
Add a configuration setting to our “Disable Teams Autostart” profile
Name: Teams-preventfirstlaunchafterinstall
OMI-URI:
./User/Vendor/MSFT/Policy/Config/Teams16~Policy~L_Teams/Teams_PreventFirstLaunchAfterInstall_Policy
Data type: String
Value: <enabled/>
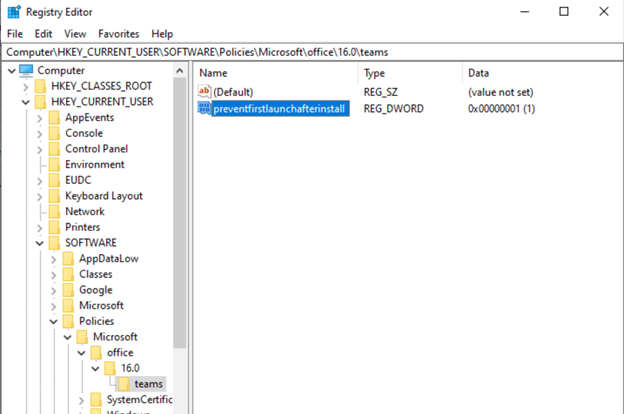
After the profile is assigned, test and verify that the setting is correctly applied in the registry.
Ascend Can Help
Windows 10 cloud-only management is becoming a reality with Microsoft Endpoint Manager. Our experts have helped organizations streamline their group policy and device deployment with our Digital Workspace Deployment solution.
Need more IT help? Check out more of our IT Tips, or reach out to talk to an expert.

