As an all-around nerd, not just a security nerd, I spend a lot of time checking out non security related blogs that involve a lot of technology. One in particular is Lifehacker.com. They usually have some pretty interesting blurbs about software or attacking a problem in a different way. Nothing too heavy, but still useful.
The other day, though, I noticed an article about a new tool from Cybereason to help fight against ransomware called RansomFree.
Cybereason
Cybereason is an Israeli company with a proud history of their employees serving with the Israel Defense Force’s 8200 unit. They have a lot of experience on the offensive side of security and are using that perspective to protect the end user. They launched RansomFree as a free solution for everyone to be able to protect themselves against ransomware and cybercrime. It’s a great concept that I actually fully stand behind, but I wanted to test how effective this solution was going to be.
From the description, it appears that RansomFree is using some form of Heuristic technology. It keeps an eye on process behavior on the end point and notifies the user if any suspicious processes are found. Should be simple enough, but I’ve seen too many times where malware is very good at being able to hide inside of legitimate processes through injection or move too fast to be stopped in time.
RansomFree vs. CylancePROTECT
I decided to test this in the same manner that we test all other AV technology and compared it against CylancePROTECT.
Here’s the test:
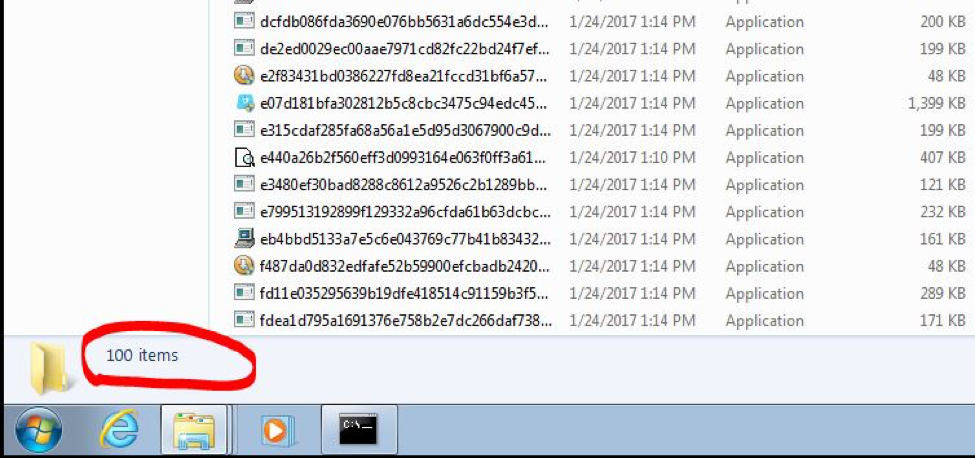
Take 100 samples of ransomware. Run them through a packer. Detonate all 100 on the host to see how long it can keep up.
RansomFree
We installed RansomFree on a test VM. It installed pretty easily and told us that we were protected.
We then downloaded our 100 samples of Ransomware. Here’s a screenshot of the package name. Remember this for later…
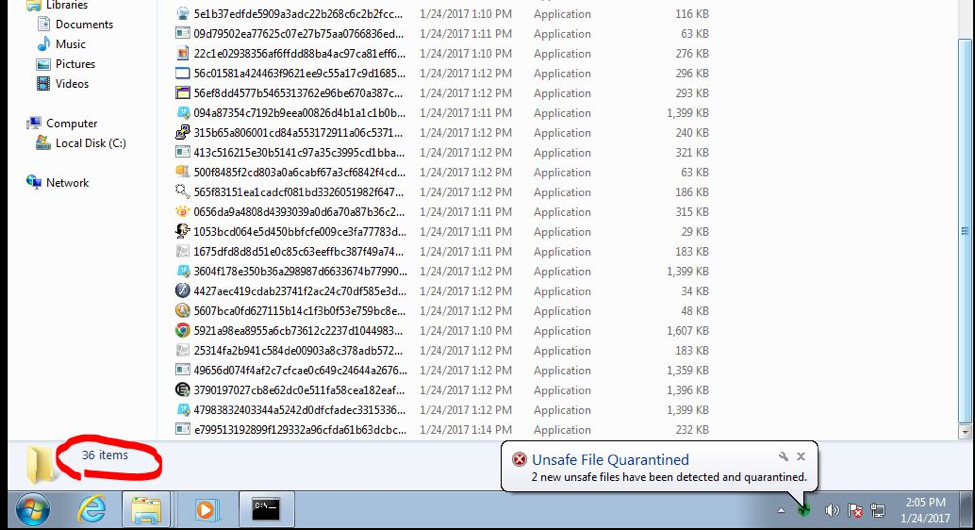
100 samples on the machine after running through a packer:
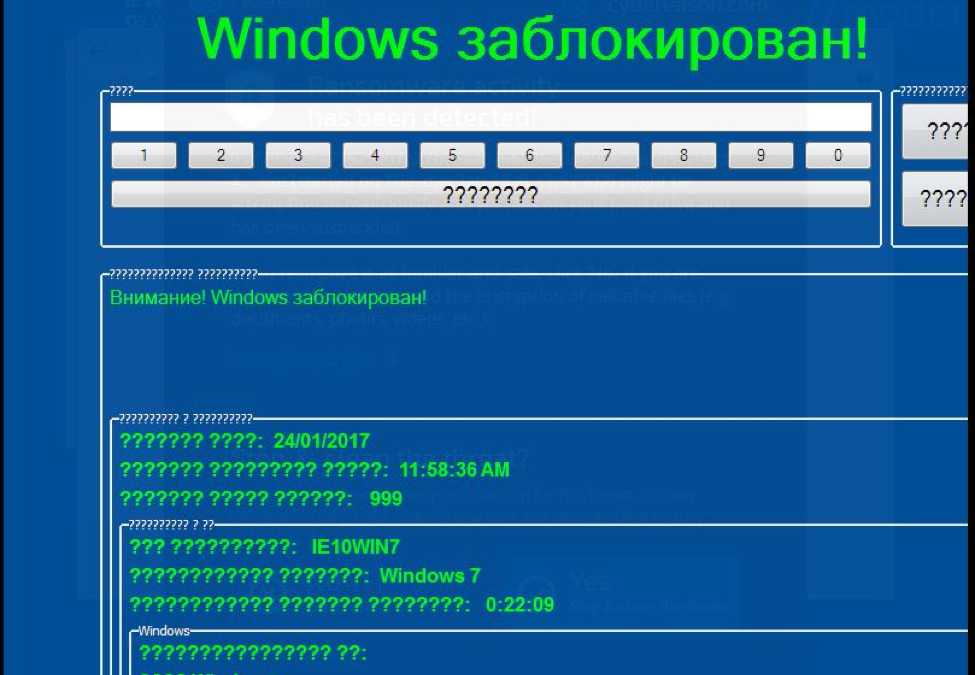
We then detonated all of them to see how RansomFree can keep up.
RansomFree Results
It didn’t. In less than a minute, the VM running RansomFree was encrypted. There wasn’t even a notification that RansomFree attempted to stop anything.
CylancePROTECT
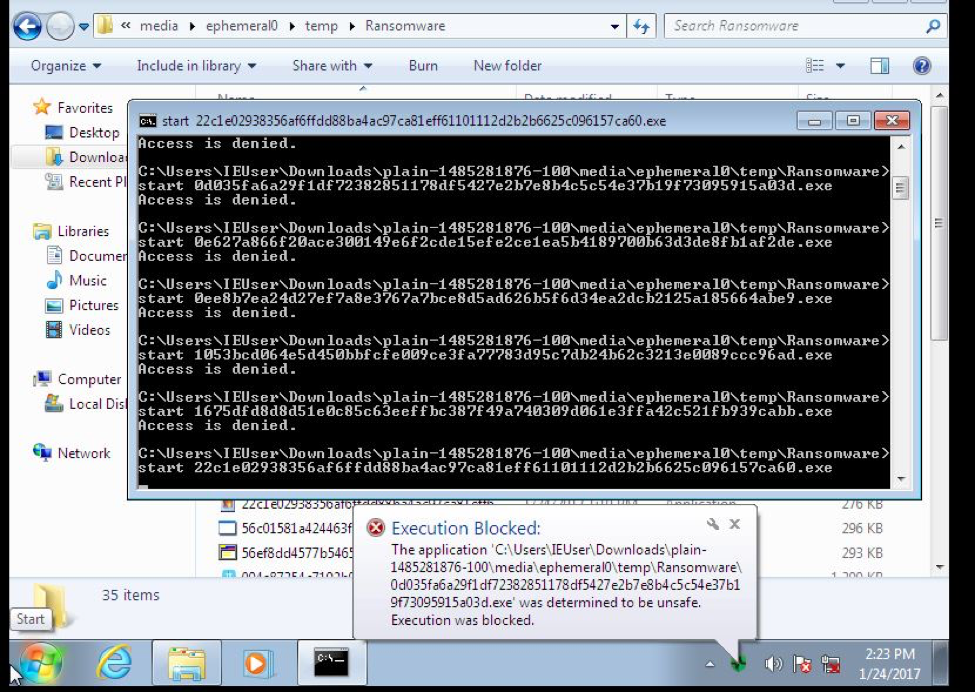
We then ran the same batch of files against CylancePROTECT.
Remember this from earlier?
In less than a minute, 64 files were quarantined before they were able to run.
CylancePROTECT Results
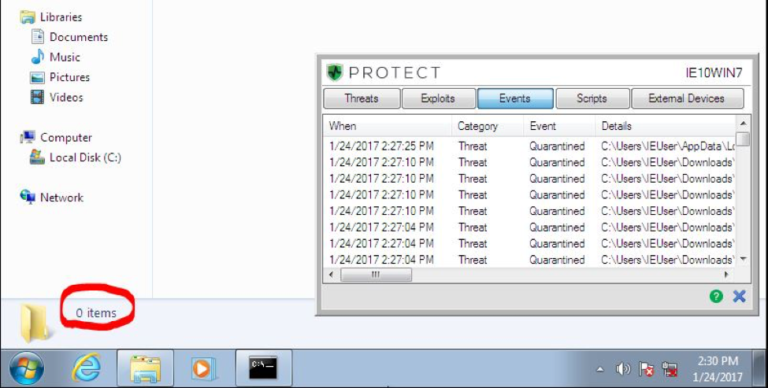
We then executed the remaining files. Almost immediately, we started seeing notifications that execution attempts were being blocked.
Within seconds, all 100 files had been quarantined. No ransomware detonated on the VM.
Conclusion
Now I know that some would say that this isn’t a fair test. Cybereason has a full-fledged product that we didn’t test. CylancePROTECT is an enterprise grade solution that isn’t free. That’s exactly why we offer our Malware Prevention Service. This allows us to take an enterprise grade solution and be able to offer it to an organization as small as 10 users. This makes it very affordable for all verticals.
In closing, RansomFree is an interesting concept and I really like the giving back to the community aspect of it. I would definitely put this on your dad’s computer next Christmas as an added layer to the AV he better already have, but I wouldn’t use this to protect a business. It will be interesting to test this again after a few upgrades.
To see this demonstration in action, please reach out to our team to sit in on one of our CylancePROTECT demos.
Written By: Derrick Masters, Security Engineer