Real incidents provide the hardest and most valuable lessons. Imagine a regular workday transformed instantly into a battleground against invisible digital adversaries. This isn't a scene from a spy thriller; it's a real-life scenario that unfolded within a corporate network, leading to a security breach. The incident in question didn't just expose vulnerabilities; it provided a blueprint for safeguarding digital frontiers.
From the initial breach triggered by an innocuous action to the swift containment and lessons learned, this case is a vivid reminder that cybersecurity is not just an IT issue – it's a crucial aspect of our daily digital lives.
Account Breach
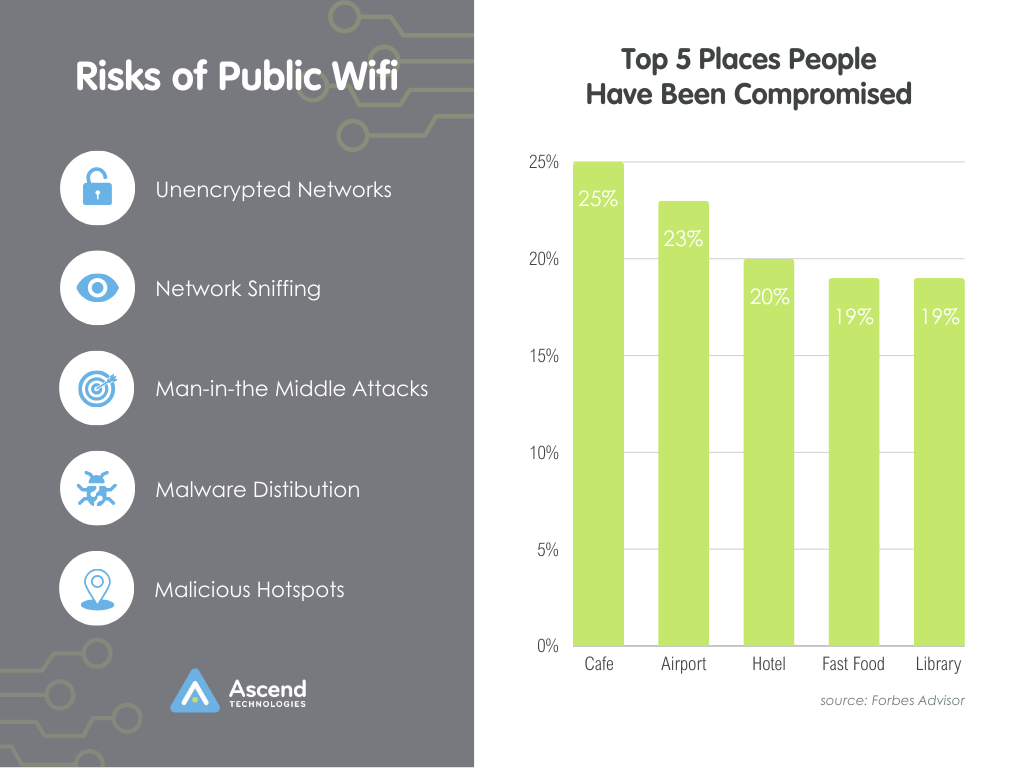
The breach began with an action most of us have performed without a second thought: connecting to a public Wi-Fi network. An employee, working remotely from a hotel, logged onto the hotel's unsecured Wi-Fi to access corporate emails.
Public Wi-Fi networks, often unencrypted, are hotbeds for cyber threats. They lack the robust security measures typically found in private networks, making them prime targets for attackers. Unbeknownst to the user, this seemingly harmless act opened the door to cybercriminals via network sniffing.
What is Network Sniffing?
The method suspected in this breach is known as "network sniffing." This technique involves capturing data packets as they travel across a network. Attackers use specialized software to intercept and analyze these packets, searching for valuable data like login credentials. In an unencrypted network, this information can be captured with relative ease.
In this case, the attacker likely used network sniffing to obtain the employee's email login details. This point in the attack is a major intervention point. Just because a bad actor has user credentials doesn't mean they can use them.
That's right; we're talking about Multi-Factor Authentication (MFA). With proper MFA procedures in place, you can stop cybercriminals here. Unfortunately, they were not properly enforced in this case. This cybercriminal easily accessed the email account without raising immediate suspicion and initiated the next phase: Phishing.
The Subtle Art of Phishing
This phishing campaign sent almost 16,000 fraudulent emails from the compromised account to all the user's contacts. Phishing emails often mimic a genuine request, like in this incident where recipients were encouraged to follow a malicious link. This attack exploits the trust between users and their contacts, significantly amplifying the potential damage.
This incident serves as a stark reminder of the importance of cybersecurity vigilance. A single lapse in judgment - using an unsecured Wi-Fi network - or misconfigured security setting - poor MFA enforcement - can have far-reaching consequences.
Additional Suspected Factors
The cyberattack may have involved more complex tactics beyond the initial breach:
- Token Theft: The attacker potentially used stolen session tokens to bypass login credentials, allowing extended unauthorized access to the account
- Adversary-in-the-Middle Attacks: This advanced technique could have enabled the interception of user credentials and authentication tokens, granting access to the user's account
- Pass-the-Cookie Attacks: There's a possibility that browser cookies were stolen and used on a different system, circumventing security checks
These suspected techniques highlight the need for ongoing education on safe digital practices and the implementation of robust security measures to protect against such threats.
Containment and Remediation
The existing security tools played a crucial role in slowing the ongoing phishing attack, limiting its impact. The organization's email security flagged the abnormal surge in outgoing emails, triggering alerts to the IT security team and blocking the delivery for many internal accounts. This rapid detection was instrumental in swiftly identifying the compromised account as the source of the phishing emails.
With swift action from the IT Security team, the compromised account was quickly isolated, halting any ongoing malicious activity. A forced password reset immediately invalidated the stolen credentials, cutting off the attacker's access, and MFA was implemented.
Through investigation, malicious inbox rules set up by the attacker to conceal their activities were discovered. The team also reviewed recent account sessions, revoking any that were unverified or suspicious to ensure the attacker couldn't maintain access. The compromised account was contained and restored to full operational status within 24 hours.
Lessons Learned
This cybersecurity incident offers crucial lessons for organizations aiming to bolster their digital defenses:
- MFA is Essential: It creates a robust barrier against unauthorized access, safeguarding accounts even if passwords are compromised
- Implement Conditional Access Policies: Enforcing MFA, especially for logins from unfamiliar locations or devices, can significantly reduce unauthorized access
- Prioritize Secure Network Connections: Always use secure, encrypted connections like VPNs, particularly when accessing corporate resources from remote locations
- Continuous Education and Training: Employees must be aware of the dangers of phishing and the risks associated with unsecured networks
- Geo-Blocking to Reduce Risk: Limiting access from geographic locations irrelevant to your business operations can decrease the likelihood of foreign-based cyberattacks
- Email Traffic Control: Mitigate the potential damage from compromised accounts by limiting the number of emails an account can send within a specific timeframe
Ascend Can Help
Cybersecurity is not a one-time effort but a continuous journey of vigilance, education, and strategic implementation of robust security protocols. Embracing these practices is a crucial step toward fortifying your cybersecurity posture.
Ascend Technologies guides organizations through their IT journey to help them lock down and protect users with vCISO and managed cybersecurity solutions. We help build resilient digital ecosystems tailored to navigate and counter the complex challenges of today's cyber world.
Talk to an expert and ensure your organization's security is not just a response but a proactive, dynamic shield against the digital dangers of our times.