Until early 2020, the oft-heard pushback from legacy security practitioners was that cloud computing could never be as secure as on-premise operations. With the COVID-19 pandemic dramatically and rapidly expanding work-from-home demands, many "cloud naysayers" were forced to adopt at least some elements of the cloud.
Now, as vaccines are deployed and the effects of the pandemic are beginning to lessen, most IT groups are grappling to determine their future course. As it appears hybrid workforces requiring newly found mobility are here to stay, concerns about securing the cloud remain front and center. Unfortunately, bad actors have also rapidly adjusted to target cloud environments, and there is a plethora of misinformation on best security practices for the cloud.
Customer Responsibility In Public Cloud Security
One of the primary areas of misunderstanding in securing public cloud usage is precisely what the cloud provider is truly responsible for. Most cloud providers have issued some variation of what AWS originally coined a "shared responsibility model," a cloud security and compliance framework dictating the provider's obligations and the responsibilities of cloud resource users. A review of such a model illustrated below clearly indicates that the customer assumes a considerable responsibility.
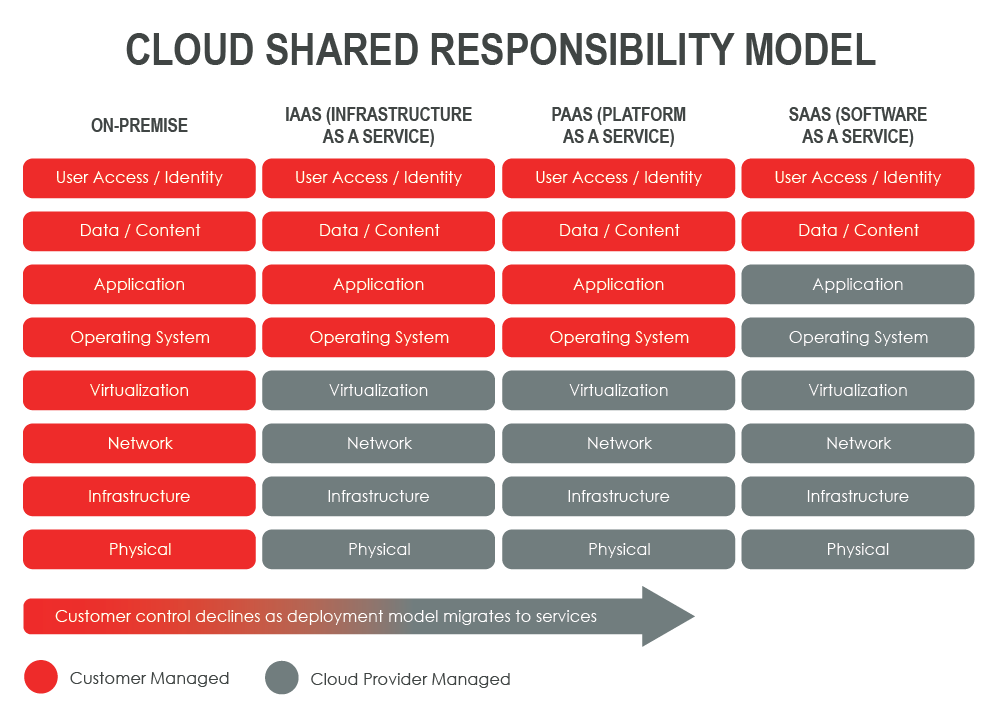
Through 2024, the majority of enterprises will continue to struggle with appropriately measuring cloud security risks.
— Gartner
Challenges in Securing the Public Cloud
Once an organization accepts its responsibility in the cloud cybersecurity puzzle, hardening is easier said than done. Not surprisingly, provider default security settings are designed to streamline cloud utilization — not security. As users configure their cloud environments to defend against security threats, they often find a confusing maze of user interfaces and methods for adjusting settings and policies.
Looking to the marketplace for assistance tools can also be frustrating. Many tools are focused on IaaS, which is certainly an attack surface. However, SaaS applications, especially workplace productivity suites such as Microsoft 365 or Google Workspace, must also be included. Damages from account takeover (ATO) and business email compromise (BEC) attacks have skyrocketed as usage of such cloud-based tools has increased.
Additionally, many marketplace tools that simply regurgitate data created by the providers are outdated in today's rapidly changing cloud environments. When using such a tool or relying on provider data (Microsoft Office 365 Security Center data, for example), many users are lulled into a false sense of security, especially when such configuration recommendations are not based on leading benchmarks. Our expert security teams have found across all sectors that cloud security controls have been poorly deployed. Organizations that attempted deployment based on provider recommendations were still missing critical security configuration controls, exposing their cloud environments.
Example O365 Study:
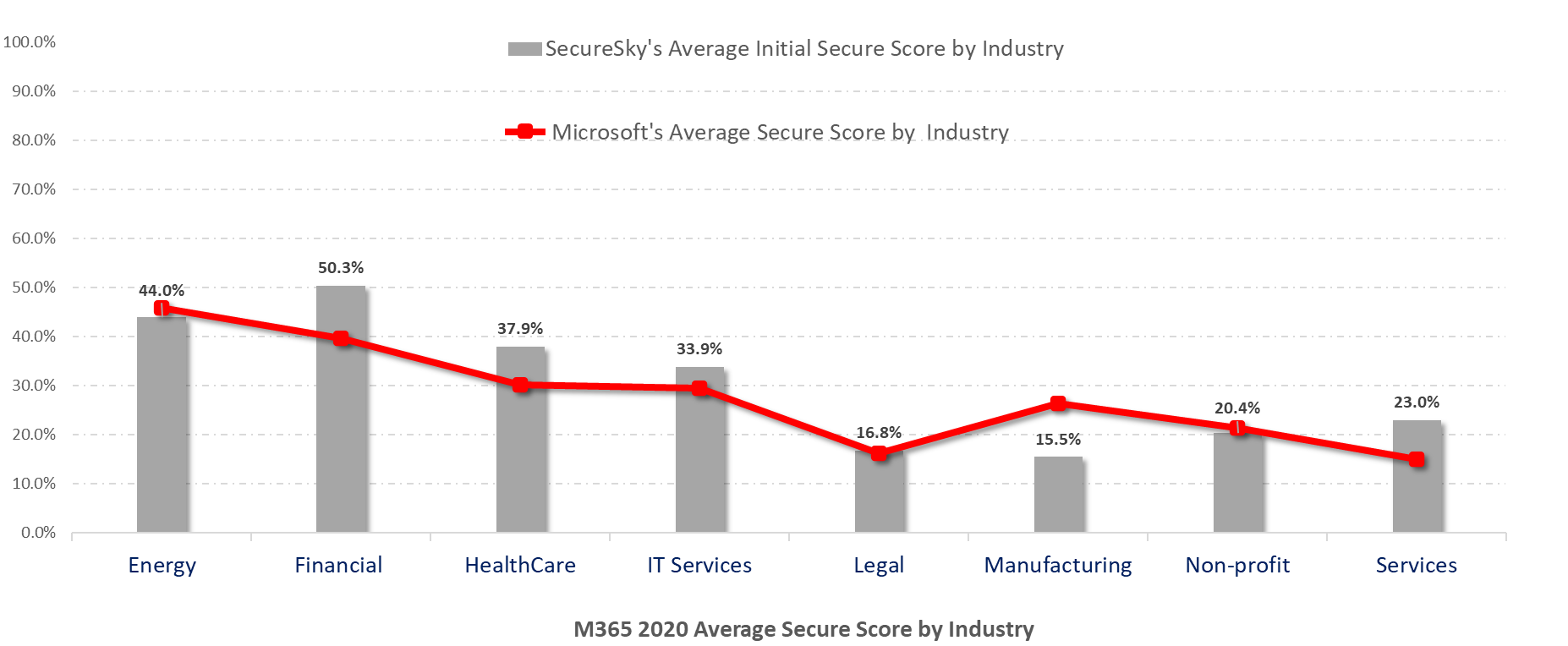
Graphic source: SecureSky Cybersecurity Threat Center
So, What Should Be Done?
Hardening cloud environments and reacting to cloud-based threats share a common approach with any element in your enterprise technology stack. Enterprises should assess vulnerabilities based on generally accepted standards and best practices, prioritize risk remediation based on likelihood and impact, and monitor and respond to threats before they become full-blown compromises.
The difference when incorporating cloud environments into your enterprise risk management processes comes down to the speed of change created by the cloud. Access a Cloud Security Posture Management (CSPM) tool that both provides complete coverage of public cloud IaaS and major SaaS providers, as well as assesses and enforces configuration standards in near real-time. Also, ensure that threat information from your cloud instances is correctly populating in your SIEM or monitoring and threat response tools. Ensure your organization is equipped to both respond to cloud-based threats and hunt for indicators of compromise in these environments.
Sources:
Microsoft Azure, https://docs.microsoft.com/en-us/azure/security/fundamentals/shared-responsibility
Amazon Web Services, https://aws.amazon.com/compliance/shared-responsibility-model/
CIS, https://www.cisecurity.org/blog/shared-responsibility-cloud-security-what-you-need-to-know/

