You may have heard the statistic: 90% of breaches start with email. But you’re probably thinking, that won’t happen to me.
You know the signs of a phishing email and you avoid emails that are clearly unsafe, so you’re not going to be the one who gets breached, right?
What you may not already know is there’s another type of phishing that’s harder to spot… and it’s very likely you’ll run into it at some point this year if you haven't already. In 2023, the volume of nefarious emails impersonating enterprises reached a staggering crescendo, with attacks such as BEC making up 99% of reported threats. According to the FBI, $17.3 billion in exposed losses of U.S. victims between 2013 and 2022 were the result of BEC attacks.
So what is BEC?
It’s a type of email attack that relies on the art of deception, but unlike regular phishing attacks, it uses a higher level of sophistication. In the case of BEC, the attacker doesn’t just emulate any brand or company in an attempt to get you to click–they do careful research and use that knowledge to impersonate a company executive, trusted brand, or partner. BEC attacks can use a variety of deceptive techniques, including display name deception, domain spoofing, and lookalike domains. The attackers will do whatever it takes to provide you with a sense of familiarity and trust, in hopes that you won’t be suspicious of what they’re asking.
There are many common examples like getting an email from HR@yourcompany.com asking you to update your W4 using the attached document. This may seem legitimate until you realize the HR department’s emails usually come through as humanresources@yourcompany.com or directly from a specific employee. If you’re not careful, you could have just handed over your social security number to an attacker! BEC scams can also impersonate your CEO (as in the example below) or a familiar coworker asking for some type of sensitive information, document, or something else of value. These attacks differ from traditional phishing because there is not often a malicious link or document attached to the email. Instead, the attacker will use pure social engineering to get you to hand the information over.
In fact, it happened to one of our employees. She received an email to their personal email account from our CEO (we'll call him Michael Scott)…or at least that’s what they wanted her to think.
Here’s the message:
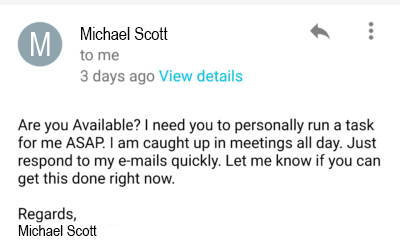
This doesn’t seem too phishy, right? It’s just an email from your boss asking for help with something. There aren’t even any links. Seems safe….
Until you look at the details and pay attention to the urgency you realize the following are red flags:
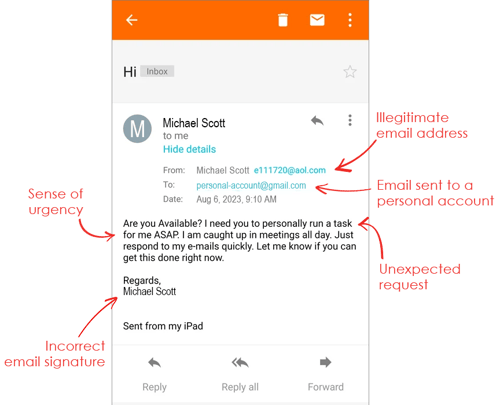
Always check the details!
How do you protect yourself or your company?
In addition to looking for the basic signs of phishing, watch out for these red flags:
Lookalike domains and display names
For example, keep an eye out for hyphens/dashes and periods where they don’t belong. If your domain is @abccompany.com, an address at @abc-company.com might look familiar at first, but a closer look will reveal that it is illegitimate. There is also a similar issue with display names: it may say an email is coming from your CEO (like the example above) or your bank, but be sure to check the sender’s full email address for signs of compromise.
Uncommon Requests
Didn’t you just update your W4 or verify your W2? Does this invoice match recent company activity? Does your boss or coworker frequently request financial transfers or valuable personal information? These are questions to ask before you click, respond, or provide any data via email. If you’re unsure or if something seems suspicious, try contacting the sender in person or over the phone. If it’s a coworker, head to their desk or call up their office phone to verify the request. If it’s a corresponding company, look up their contact information online and give them a call. Being extra cautious about handing out sensitive information could mean the difference between preventing a huge loss and falling victim to a BEC attack.
Education is key when it comes to spotting malicious emails. Every single employee is susceptible to phishing emails and it only takes one person to click or respond to potentially cause a breach. At Ascend, we offer Phishing and Security Awareness Training. We send your users crafted phishing emails at random intervals over a determined period of time. No rickrolling here: if the phishing link is clicked in the email, the user is enrolled in security training modules that teach them what they did wrong. After the baseline testing is done, you will be able to see your company’s phish prone rate decrease as the testing continues.
Your company is at risk and it’s important that you don’t wait to take the next steps. Contact us today!

