Cybercriminals are incredibly resourceful. As security practices rise in sophistication to account for rapidly diversifying types of threats, hackers are returning to not-so-new methods to sidestep modern security practices.
One of these methods even dates back to Ancient Greece. A story from 440 BC tells of the Greek ruler Histiaeus who had a servant’s head shaved and their scalp tattooed with a secret message. The servant was then sent off to deliver the message once his hair had regrown.
This practice of hiding covert messages in plain sight beneath seemingly innocuous cover is called steganography.
Nowadays, steganography tactics are often digital, resulting in something as inconspicuous as a JPEG of kittens containing encrypted messages or harmful code. Unsuspecting users may share or download these hidden threats then suddenly find their computers infected with malware.
So, how can you spot threats like this before they affect your business? In order to identify how this practice could impact your business, we need to discuss it’s changing face.
How Can a JPEG Attack my Computer?
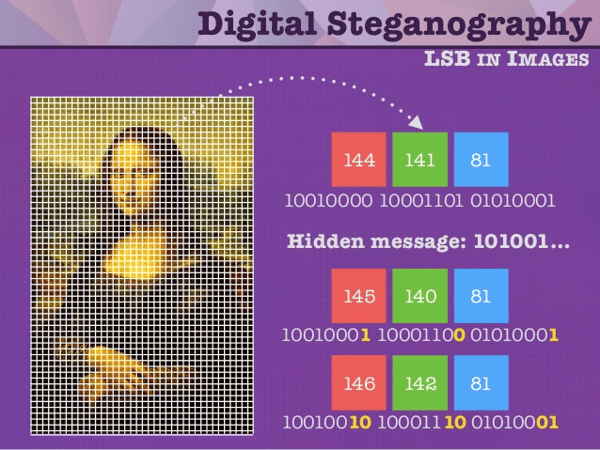 (Representation of malicious code hidden within images, Steemit, 2017)
(Representation of malicious code hidden within images, Steemit, 2017)
In 2018, bad actors used Twitter to distribute memes with hidden payloads. These images concealed remote command-and-control services for malware-infected PCs. Each time the images were shared, users extracted the country codes of their phone numbers associated with their Twitter accounts.
While these sorts of attacks had been relatively uncommon in recent years, reports found a 600% increase in attacks that use stenography in 2017. This rapid increase isn’t to say the threat is new by any means — it’s merely representative of the fact that the amount of content where an attack can be hidden has grown in spades across the internet.
This highlights the importance to watch for a resurgence of known threats and to ensure you have the right technology and cyber awareness training in place to detect them.
The Evolution of Steganography
The rise of steganographic tools is good news for people who live under repressive regimes or others attempting to safeguard themselves against threats. When in the hands of bad actors, however, the tools make life harder for law enforcement and security agencies.
While hiding command code in images is no new practice, today’s cyber criminals have created advanced steganographic tools to make detection of threats even more difficult.
As an example of the dual-edged nature of this method, cyber expert Dominic Schaub is building a new approach to digital steganography, in the form of a "fast, stable and functional" toolset that he says functions as "a self-concealing, perfectly deniable encryption/steganography suite."
Building from an approach known as Russian Doll steganography, Shaub has created self-concealing tactics that appear to a computer as a normal Linux system at startup, which aids attackers to elude forensic analysis and gives cybercriminals plausible deniability when administering such attacks.
While this will be of great help to people living in repressive areas, Shaub’s new deniable steganographic tactics will unfortunately also be a nightmare when it comes to gathering digital evidence of attacks perpetrated by cybercriminals.
Detecting Threats
By their very nature, steganographic messages are difficult to detect. Without proper training, most instances slip by a layperson without detection. Only a full commitment to security will give your organization optics to mitigate and manage such risks.
Like all malware attacks, steganographic threats require a user to click on a link or download a file. So, the best place to start is to train your team about these types of attacks. While the technology to detect and decrypt steganographic attacks is still developing, the security industry is fighting back, and improvements are happening every day.
Here’s where you can start:
Invest in a malware sandbox that can provide behavior-based analysis and work as part of an integrated security system. Integration with network protection and a threat intelligence platform can help analysts keep track of what’s important when it comes to identifying evasive malware.
Organizations should also take an activist approach to cybersecurity hygiene measures that include both ongoing end-user education and timely endpoint update and policy enforcement measures to defend against steganographic attacks.
If you’re looking for help deploying or developing a cybersecurity awareness plan for your office, Ascend can offer additional resources to set your plan off on the right foot. From monitoring endpoint protect to expediting timely patches, updating policy settings, and making it harder for steganographic and other types of attacks to gain traction in your infrastructure. Contact us to set up a free security audit today.
