Thanks to the deluge of Crypto malware attacks recently, everyone in infosec has been VERY on edge about anything that pops in a quarantine. “Oh crap. What’d they hit? Where’s it going? What IS this?!”
Recently, we noticed such a hit with one of our customers in the financial world.
We received an alarm out of our SIEM that Cylance had quarantined something suspicious that was posing as a flash installer, flashplayer[1].exe.
It’s a Trap
I was able to see that it was located at the following file path, (obfuscate the name):

Looking for a quick win, I checked the hash against the VirusTotal database to get some more information. At the time, there was nothing detected. We’re now up to 33 out of 57 tier 1 vendors. I’m seeing references to Artemis, which is a fairly known trojan. I wish I would had this information before. Well I didn’t, so I needed to do some further digging.
Looking further into the information that Cylance was able to pull out, I was able to see right away that the metadata didn’t match up. The product name was coming up as Undeludable with a company name of Slips.
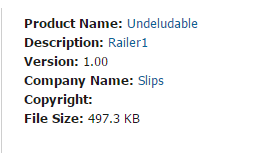
As if that wasn’t enough, the certificate was issued by Comodo, not Adobe. The publisher was a company called “BITT” LLC. Five minutes of web searching directed me to a site that was under construction.
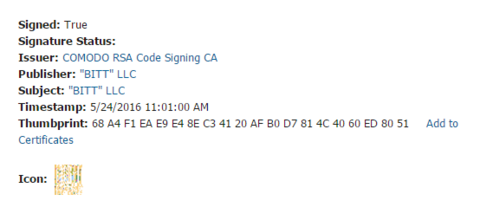
The detailed threat data out of Cylance showed Undeludable again but now I was also seeing that the original file name was referencing Unorganic8.exe. We’re definitely not dealing with Flashplayer at this point. Now I’m curious. I notified the customer that we may have just saved their bacon and kept digging.
I was able to see that this file imports MSVBVM60.DLL. This is the Visual Basic Virtual Machine. So now we have something that’s using VB and is doing process injection. I was able to pull out DllFunctionCall, an API function, as well.
I ran strings against the executable and wasn’t able to get much. What I did get gave some clues. First off, I could see very obvious signs of attempts to obfuscate any clear text information.

Anything that was cleartext gave references to Visual Basic again as well as some wording that appeared to be giberish. Some research shows that these might actually be words in other languages:
Tekstilets – Finnish
Beluringen – Norwegian
Lithuria – Albanian
Leveringssikkerheds – Danish
Additional files that were attempted to be installed, (droppers), included emese.exe and a hash
40c0597e4480dacdca113d89441de747d15c4ecfba129cc9b149cd4382a96ad8
I Have a Bad Feeling About This
At the time of the hit, analysis in VirusTotal didn’t get me much. Now, I can see that this is where our pal Artemis can be found.
Looking more into the behaviour, I found references to the following:
C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe
c:\docume~1\admini~1\locals~1\temp\40c0597e4480dacdca113d89441de747d15c4ecfba129cc9b149cd4382a96ad8
C:\Documents and Settings\Administrator\Local Settings\Application Data\emese\emese.exe
c:\documents and settings
Since when did Flash Player need to access PowerShell?
There was even more fun in the registry:
More references to VBA, but what was even more interesting were references to Wireshark!
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\Wireshark.exe
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\Wireshark.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Wireshark
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Wireshark
HKEY_LOCAL_MACHINE\Software\Wireshark
HKEY_CURRENT_USER\Software\Wireshark
And a number of web proxies:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\Fiddler.exe
https://en.wikipedia.org/wiki/Fiddler_(software)
HTTPAnalyzerAddon
Analyzer for incoming and outgoing traffic
Charles.AMF.Document
https://www.charlesproxy.com/
XK72 Ltd folder
http://www.xk72.com/
So far, I haven’t seen a single reference to flash.
Cylance Analysis
At this point, I kicked this over to Cylance to let them sandbox this and get more detail. This is what I got from one of the reps we work with:
“The sample is not Adobe Flash Player. It is signed with an adware-associated Authenticode certificate, but exhibits Trojan behavior. When executed, the sample creates several instances of regsvr.exe, and injects itself into them. After the sample’s process exits, the regsvr.exe instances make a large number of outbound connections to remote servers on ports 80 and 443. The sample downloads and stores a payload in the Windows registry, which is executed through a line of Javascript that is also stored in the registry. During the course of the investigation, the file was determined to be a Malware Trojan.”
These are the IPs that it was calling out to:
118.60.127.40 – Korea
133.67.241.255 – Japan
134.148.115.243 – Australia
139.76.26.37 – USA AT&T
142.177.242.47 – Canada
173.194.26.138 – Google
200.236.87.75 – Mexico
200.7.211.1 – Ecuador
203.105.149.2 – China
220.77.93.127 – Korea
223.188.52.42 – India
6.147.118.143 – Arizona, USA
6.176.99.249 – Arizona, USA
6.220.30.199 – Arizona, USA
7.246.177.61 – Ohio, USA
Predictive and Preventive
Most of these were major TelCo’s and ISP’s from around the world. Nothing coming back to Adobe though. Once some static analysis was done it was obvious the file was malware, but I have seen malware that’s pretty good about camouflaging itself. Had our customer had an AV product that relied on signatures or VirusTotal, it would have resulted in an infected machine and possible lost information. This post would have been more about how we do incident response instead of how we prevented the malware attack to begin with.
Written By: Derrick Masters, Security Engineer
