What sounds better? Proactively fighting potential threats or scrambling to pick up the pieces after an attacker has successfully made their way onto your system?
As threats continue to become more complex and targeted, it’s more important than ever to focus your efforts to minimize the risk before it’s too late. Vulnerability management is one way to do that.
What is Vulnerability Management?
Vulnerability management is a continual process, not only to detect risks on your network but to create a plan to prevent those vulnerabilities from causing future damage. A good vulnerability management system combines technology and a team of security experts to proactively detect and act upon security risk.
A vulnerability is a weakness in your system that leaves you open to attacks. It can be caused by a flaw in hardware, software, or in the implementation of either one, which leaves your system open to potential risk.
Many vulnerabilities are easy to detect and fix. Most software and hardware vendors keep an eye on potential vulnerabilities, writing and releasing patches. But as employees click to ignore these updates or potential vulnerabilities slip through the cracks, you’re opening yourself up to new risk and future losses.
A good vulnerability management system works through multiple stages to decrease the security risk profile for your company.
Why is Vulnerability Management Important?
The number of vulnerabilities is increasing. According to CVE Details, more than 16,500 vulnerabilities were reported in 2018, compared to 14,600 in 2017, and the number continues to grow. Additionally, because of the large number of devices accessing your network, many endpoints that leave you open to threats, and more sophisticated attacks, it’s critical to proactively handle your network vulnerabilities instead of managing them after an attacker has discovered them for you.

Constant updates and patches
Because hardware and software vendors are constantly on the lookout for bugs or vulnerabilities in their own platforms, they frequently push out updates and patches. This can be harmful as employees click to ignore those pop-ups on their computers. On the other hand, managing all of those updates can be a full-time job for your IT or security team.
More advanced attacks
As advanced, customized threats continue to spread, many attackers will actively search for vulnerabilities on their targets’ networks, rather than conducting a general, widespread attack. These vulnerabilities give attackers more opportunities for successful entry and exploitation of your network.
Industry regulations
Many industries now have regulations in place requiring companies to have a vulnerability management process to manage patches on their software and hardware systems. These regulations are good motivation to create a strategy and proactively fight potential threats.
The Stages of Vulnerability Management
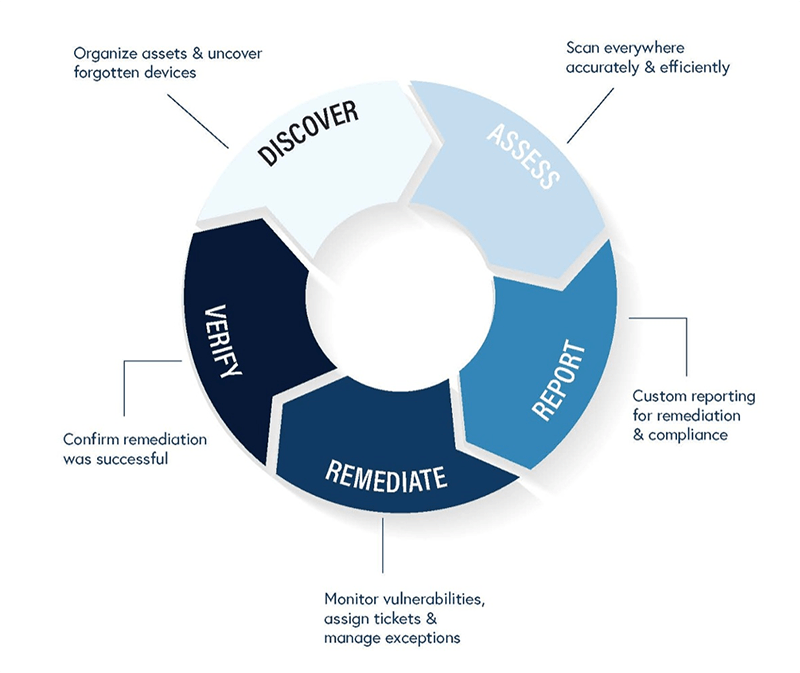
The typical vulnerability management process breaks down into multiple stages aimed at analyzing, prioritizing, and protecting your network.
Stage 1: Discover
The initial stage of the vulnerability management process is all about preparing for the vulnerability scans and tests and making sure your bases are covered. This means organizing all your company assets and uncovering any forgotten devices.
Compile all of the assets you need to test, determine their importance and who can access them (whether just administrators or your whole team). Work to maintain a continuously updated inventory so you can provide a map of the vulnerabilities throughout your network.
Stage 2: Assess
Once you’ve compiled all of your devices and inventory, the next stage involves the tests to make sure every device is scanned, both accurately and efficiently.
It’s not just about knowing the vulnerabilities, but gaining timely, efficient access to the information. If you aren’t receiving the data from a credible source, you might be wasting your time on false positives.
Once you’re aware of the potential risks on your devices, the next step is to prioritize those vulnerabilities. With the large number of vulnerabilities disclosed every day, it can seem impossible to manage them all, making it all the more significant to prioritize the biggest risks and resolve those first.
Stage 3: Report
All this data is then compiled into a custom report, giving details on the vulnerabilities and how to prioritize them. These reports will include recommendations as well as the best plan to triage the risks quickly and seamlessly.
It should include the actions to take and give step-by-step instructions to fix the problem. The purpose of the report is to significantly decrease the security risk that these vulnerabilities present in a practical way.
Stage 4: Remediate
In the stage of remediation, the goal is to monitor vulnerabilities, assign tickets, and manage exceptions.
As vulnerabilities are detected and reported, the next step in the vulnerability management process is to correct, monitor, or remove those vulnerabilities. This can be accomplished through the necessary updates and patches or workarounds to avoid the threat.
This stage is then repeated as new vulnerabilities are discovered. The network and its devices need to be continuously monitored to detect and find new vulnerabilities that might lead to potential, future threats.
Stage 5: Verify
The final step is to verify the success of the entire process. This step not only helps you see that the mitigation was successful but also maintains transparency and accountability across the company. The whole goal is to reduce the attack surface of a company, findings ways to minimize the threat of an attack by decreasing vulnerabilities.
With an ever-growing number of vulnerabilities, it’s challenging to know how to detect them on your own, let alone prioritize and remediate them. Equip your team to fight back by investing in a vulnerability management tool and team to minimize the risk and potential threats.

