Share link, get coupon? Not so fast.
Both business and home users are being targeted with a new wave of social media scams offering too-good-to-be-true coupons (often $50 or more).
So what’s the catch? All you have to do is click the link…or in some cases, all that’s asked is that social media users hit “share” and spread the link to their connections online.
The catch is that many of the fraudulent “retail” sites are actually drive-by malware downloaders…and that’s exactly why scams like this work.
Increasing Digital Threats, Social Media Scams
Security experts have warned that the COVID-19-based self-isolations, shelter-in-place regulations, and subsequent increases in online activity would be a cyber-scammer’s heyday. Attacks like these are a clear sign that these warnings were not without cause and cyber criminals are indeed taking advantage of the current situation.
Even as the world comes to a halt, the bad guys don’t. In fact, they can make a profit from these circumstances very easily—and they are.
Attacks like this are a clear indicator of the risks of working from home (WFH) on personal devices, as referenced in previous tips for WFH security. In the average home, personal devices like laptops and desktop computers are generally protected by less-effective security solutions—if they are protected at all. This makes it incredibly easy for cyber criminals to host a tricky social media scam or fraudulent website to successfully deliver malware to unsuspecting victims. The result? Many unprotected, or under-protected, personal computers are likely already infected with keyloggers or other trojan malware variants and those devices may now be in use for remote working, putting businesses at risk.
Employees working from home on personal devices? Learn more about Malware Prevention Home.
“Bath & Body Works Coupon” and Similar Scams Host Drive-By Malware
A member of our Security Operations Center (SOC) investigated the following Facebook scam:
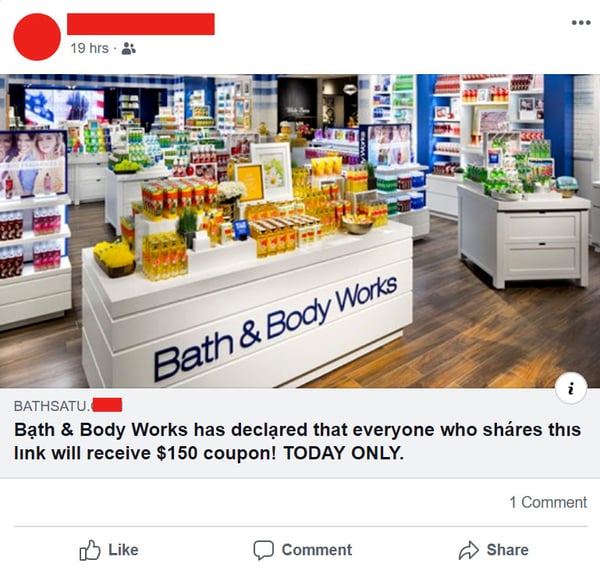
The fraudulent Bath & Body Works link promises $150 coupon to users who share their link.
Red Flag #1 – Incorrect URL
As you can see, the URL of the website supposedly hosting this coupon giveaway clearly does not belong to the real retailer, bathandbodyworks.com. This is the first sign that something isn’t right with the post.
You can also hover over (or long press) on the link to preview where it’s heading to see that this is not just a short URL for Bath & Body Works or a reputable coupon site.
Red Flag #2 – Strange Characters, Typos
Next, you’ll notice the title and preview text for the link are slightly strange. Uncommon characters and typos are present. This would not be the case for a legitimate retailer’s site or any associated promotions.
The character replacement technique may be a method of obscuring the webpage from appearing in google searches to avoid having the scam noticed or taken down by authorities.
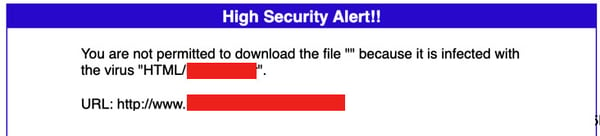
This particular site may have appeared “safe” to the untrained eye (or unsecured device) as it only held a form to fill out to redeem the aforementioned coupon, but it was actually hosting what’s called a “Drive-By Web Attack.” These attacks host varying types of malware that automatically download when the infected site is visited by a user.
In this case, the post’s URL was set to redirect the victim to the malware download. If that was blocked or didn’t succeed, the victim could be caught in the next step of the process: the form to “redeem” their coupon. At the end of the seemingly innocent form—which asked for information along the lines of whether or not you have shopped at the specified store, contact information, etc.—the user could click the link to get their coupon, and in this case that means manually downloading the malware.
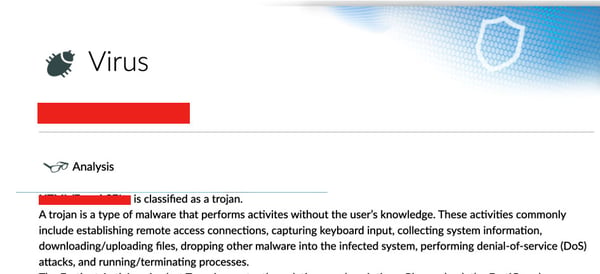
Investigation of the file determined that it was a type of trojan, likely designed to steal data or perform keylogging activities on the victim’s infected machine undetected.
It is unclear how many users may have fallen victim to this specific attack at this point in time, but it is clear that this attack can very easily infect those victims who have no security precautions on their devices.
Preventing These Attacks
Bath & Body Works is not the first company to be spoofed for an attack like this and they won’t be the last as cyber scams and web attacks increase. Here are some tips on what to look out for and what you can do to protect your web browsing for work and home:
-
Watch for too-good-to-be-true offers and/or strange looking link previews.
If it seems strange, it probably is! Pay attention to the title text, URL, and images associated with shared links to verify legitimacy.
-
Think before you click (or share)!
Watch out for warning signs before you visit a website or share a post on social media. The same goes for suspicious emails as well. The bad guys rely on you to be mindlessly scrolling and clicking to make these mistakes—don’t let them win. Keep a critical eye on offers and viral posts making their way around your social timelines.
-
Protect your devices with effective anti-virus (and more)
Not all anti-virus solutions are created equally, especially those that still rely on virus and malware signatures to determine what’s safe from what’s unsafe. Free security programs for your devices are, unfortunately, not likely to protect you from new and advanced cyber threats. In addition, for business users, there are security solutions that work together to protect all areas of your network and the devices within it. Learn more about these layers in cybersecurity bundles.
-
Share your cyber knowledge with vulnerable friends and family online.
Not everyone is aware of this information, so share it with them!
Know that you are always free to share articles from the Infogressive blog or posts on our social media accounts to help educate your friends, family, and colleagues. You can find us on Facebook, Linkedin, Twitter, and Youtube for security tips, attack breakdowns, educational cybersecurity content, and more.
We’re here to help, and we’re in this fight against cybercrime together.

