Leaving your remote desktop protocol (port 3389) servers open to the internet has been known to be a cybersecurity “bad idea” for years, but the Bluekeep vulnerability, as well as the more recent Seven Monkeys batch of disclosed vulnerabilities, have made this vital to your business’s survival.
What is Remote Desktop Protocol?
Remote Desktop Protocol (RDP) is a Microsoft protocol that allows remote users to initialize connections and transfer data between computers or machines over a network connection. Put simply, RDP is a feature that allows users to access computers from other computers, rather than requiring physical, in-person access to perform tasks or transfer data.
While this capability is incredibly useful for both business and home users of Windows devices, there are also security considerations that come with using RDP. Leaving RDP “wide open” to the internet and falling behind on critical security updates are both ways that RDP can go from “useful tool” to “easy attack vector” for a cyber breach.
BlueKeep & Seven Monkeys
Beginning in May 2019, RDP Vulnerabilities began making news with the discovery and subsequent naming of the critical BlueKeep vulnerability affecting Windows devices. Microsoft urged all users to apply the security patch via Windows update immediately. Later that month, however, it became clear that despite the urgency of the vulnerability, 1 million devices were still vulnerable to the BlueKeep exploit.
The situation has only gotten worse with the recent release of seven important & critical patches for RDP vulnerabilities. This batch of updates has been titled Seven Monkeys as of August 13, and cybersecurity experts say this batch of RDP vulnerabilities are far more critical than the initial BlueKeep in May.
These 2019 RDP vulnerabilities are ‘wormable,' meaning they can be used to propagate or move laterally within a system once initial access is gained. To put it simply, if an attacker exploits an RDP vulnerability on one machine, the attack can easily spread throughout an entire network using the same unpatched vulnerability. This makes it doubly important that these vulnerabilities are patched on all systems—not just those exposed to the internet.
The rise in RDP-based attacks also affirms the importance of network vulnerability scanning. A vulnerability scan can assess your external-facing assets to identify easy entry points for cyberattacks—like an open RDP port—and help ensure that your systems are architected as intended. These discoveries help your organization understand what your network might look like to a potential attacker and can help you determine your next steps in securing your environment.
The Infogressive Perspective
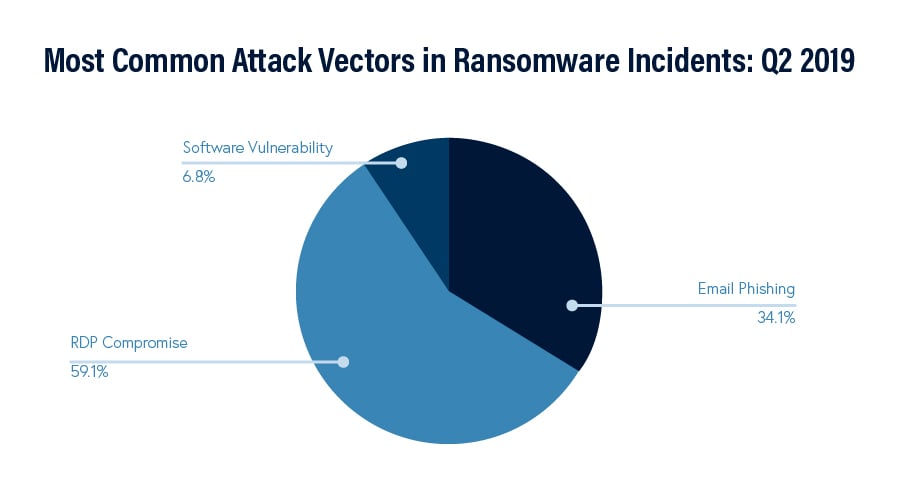
Considering recent Incident Response engagements that we’ve performed, the majority were caused by an attacker exploiting remote access vulnerabilities left open to the internet. In fact, this growing attack vector has surpassed malicious emails as attackers’ initial entry point in cyberattacks.
Infogressive customers who are protected via our Perimeter Security service are already protected from these vulnerabilities externally*, and customers who subscribe to our Vulnerability Management service will have a full report with their upcoming scans (or have already received a report) detailing any systems affected and instructions on how to completely patch them.
If you’re not sure of your organization’s status in regard to Bluekeep, Seven Monkeys, or any other network vulnerabilities, please contact us today. We can help!
*Any firewalls configured outside of Infogressive’s standard recommendations may not be protected against RDP vulnerabilities. Please contact Infogressive support about any concerns regarding Port 3389 on your Infogressive firewalls.
Written by Jeff Murphy, Security Engineer

