Cisco just released their midyear cybersecurity report, exploring the reasons why potent attacks are spreading and providing insights into undermining attackers' impact. Their findings were rather disturbing, but they do illustrate the point that businesses can prevent software vulnerability…if they’re willing to put in the work.
A major finding of the report is the staggering amount of IT infrastructure that is not up to date security-wise, riddled with vulnerabilities that cybercriminals are exploiting with modern tools and techniques. In an age when technology develops as rapidly as it does, we should expect that criminals will be working hard to stay one step ahead of their targets. The only surprise is just how far behind businesses are lagging.
Cisco did an analysis of their own products, along with those of Apache and OpenSSH. What they found is that “organizations are not diligent about addressing known vulnerabilities in either group of products. Some may simply wait to replace their infrastructure rather than go through the hassle of upgrading—or they may find they have waited so long that they can’t upgrade their products because they are no longer supported. In any case, we found that products run with known vulnerabilities for about 5 years, on average.” A whopping 106,000 of 115,000 Cisco devices analyzed — 92 percent! — had known vulnerabilities in the software they were running.
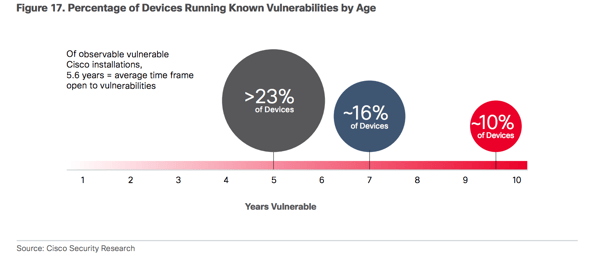
In its report, Cisco urged organizations around the world to prioritize their aging IT infrastructure and systems, on every level. Random patches and reactive measures will not do; companies have to take a hard look at their infrastructure and systems, and determine a plan to bring them all up to date in a comprehensive way. They have to get rid of products that are no longer supported, and upgrade their systems to meet modern standards.
It’s not as though organizations are just lazy – a software product’s maintenance is never done, and businesses have to prioritize their time. To update enterprise software requires an investment of manpower, money, and system downtime. Even if a company knows about certain vulnerabilities, they might not have the resources to dedicate to fixing the issue, so they bank on the odds that they will probably not be a target.
Updating a product’s infrastructure can also be an incredibly difficult process, and does not come without risks to its functionality. The possibility of performance issues caused by updates can cripple a product, and for many companies, they simply believe that this outweighs the possibility that they will become a target for cybercriminals. But Cisco’s report seeks to emphasize just how vulnerable these systems have grown, and how appealing infrastructure as a target has become to attackers.
One important consideration for companies is the fact that fixes and updates become more difficult and costlier if left unaddressed for extended periods of time. Cisco advises companies to move software upgrades and maintenance to the top of their priority list, so that each modification is attainable, and their infrastructure problem does not snowball into a giant, unmanageable task.
Cisco argues that “fragile, insecure infrastructure cannot support the emerging next-generation digital economy. To truly realize the benefits that digitization and the Internet of Things will bring, organizations need to tackle the security problems of the first digital wave.” In the broader sense, the ability for quick innovation, development, and forward movement is key to companies’ ability to stay ahead of cybercrime.
Many companies’ systems are built on infrastructures that were originally created in an environment that didn’t require our current vigilance for these attacks. But with each upgrade, they have a chance to move towards a future in which maintenance is more manageable, and system safety doesn’t get left behind.
Written by Luke Robbins

