Security platforms often focus on protecting organizations from the threats of cyberspace. These threats include phishing campaigns, malware, network infiltration, and ransomware deployments. Organizations must create an Incident Response Plan (IRP) to manage their response and recovery from security incidents. This plan must be strong and comprehensive.
Your IRP isn’t a stand-alone document. It should be part of a strategic contingency effort. This should include business continuity planning, crisis management, disaster recovery, and life safety.
How Your IRP Fits Into Your Contingency Plan
Your IRP is one of several components in your business’s overarching contingency plan. However, the contingency plan itself lives at the highest level – policy and executive summary.
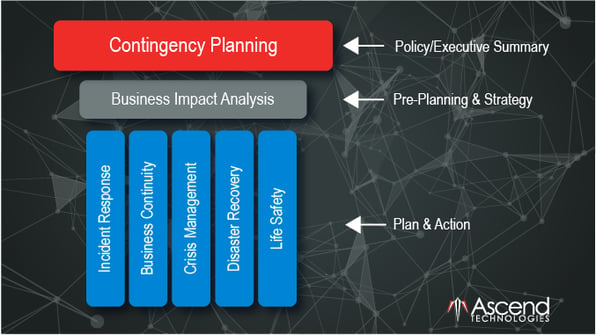
Before creating an IRP, businesses should address the pre-planning and strategy phase of the contingency plan. This requires a Business Impact Analysis (BIA). Incident response planning is one of several plans and action steps that fall underneath the BIA. Others include business continuity, crisis management, disaster recovery, and life safety.
These plans and action steps are based on your business’s unique environment. Your BIA findings should help guide you in planning these steps.
Overall, contingency planning is made up of seven steps:
- Develop a contingency planning policy statement
- Conduct BIA
- Identify preventative protocols
- Develop recovery strategies (backups, redundancy, places to work)
- Develop contingency plans (who does what, what goes where, and how it works?)
- Conduct plan testing, training, and exercises
- Maintain the plans

The Basics of an IRP
You will notice that steps 3, 4, and 5 of your contingency plan will outline your IRP. In the IRP, you expand upon that outline with more detailed information. Each incident response plan should consist of the following seven components.
#1. Incident Identification
Your IRP should clearly define what is considered an incident and what is considered an event. Each of these activities will have a different response path, so determining how to differentiate them is essential. Implement a clear reporting system that allows employees to communicate potential incidents effectively. This will ensure that the right information reaches the relevant team members.
An incident could be unauthorized access to sensitive data, while an event might be a failed login attempt. Develop a classification system that categorizes different types of security events and incidents to streamline the response process. These will be instances such as unauthorized access, malware infection, or data breach.
#2. Incident Assessment
Once you identify an incident, you’ll need to document how to assess the severity of the incident and determine its impact on the company. Then, define who will perform this assessment and its completion timeframe. Develop guidelines for prioritizing incidents based on potential impact, compliance requirements, and business risks, allowing for a faster and more efficient response.
An incident assessment matrix can help prioritize incidents based on factors like severity, potential impact, and response time. For instance, a severe incident like ransomware affecting critical systems may be prioritized over a minor incident such as a single phishing email.
#3. Lessons Learned
In this step, you’ll conduct a post-mortem of the incident to determine the root cause and discuss how successful your team was at handling the event. Documenting an incident and the process for identification and resolution is critical to improving your IRP in the future. In addition, creating a culture of continuous learning and improvement will help enhance your security posture over time.
After responding to a distributed denial-of-service (DDoS) attack, the team might identify that the firewall rules were not adequately configured, allowing the attack to cause significant downtime. As a result, they can update the rules and implement additional monitoring tools to detect and prevent future attacks.
#4. Annual Review & Testing
An IRP on paper is only successful if you can prove it works during an actual incident. Testing your plan from start to finish will allow you to see what works well and where there are gaps so you can enhance the process. Simulated incident exercises and tabletop exercises can provide valuable insights into your team's readiness and ensure your IRP's effectiveness.
Conduct a tabletop exercise simulating a phishing attack that leads to a data breach. During the exercise, the team will walk through the IRP steps, identify any shortcomings or inefficiencies, and modify the plan accordingly to ensure a more effective response.
#5. Responses to Specific Scenarios
Planning for specific incidents that are more prevalent in your industry and those that could impact any organization that utilizes technology to run your business will help you be as prepared as possible. In addition, this step ensures your IRP meets the specific needs of your business. Collaborate with a Managed Security Services Provider (MSSP) to gain insights into evolving threats and best practices for response and mitigation.
Develop specific response procedures for incidents such as ransomware attacks, insider threats, or supply chain attacks, tailored to your organization's needs and infrastructure. These procedures should detail the steps to be taken by each team member, the tools to be used, and the communication channels for sharing information.
#6. User Awareness & Training
Define the information you need to provide your employees regarding your security policies and determine how you’ll share it. Security awareness training helps your team understand your security policies and explains how they should adhere to the guidelines to protect your organization’s security.
Implement mandatory annual security awareness training covering topics like phishing, social engineering, and password security. Additionally, conduct periodic phishing simulation exercises to evaluate employee vigilance and reinforce the importance of security awareness.
#7. Cyber-Insurance Review
Conduct an annual review of your IRP and compare it with your current cyber insurance policy. You should clearly define who manages the insurance policy and what is covered to verify that the plan aligns with your coverage. Working with a knowledgeable cyber-insurance broker can help you determine the most appropriate coverage and limits, ensuring your policy remains relevant and up-to-date.
Ensure that your cyber-insurance policy covers the costs associated with a data breach, such as incident response services, customer notification, and credit monitoring services. Collaborate with your cyber-insurance broker to adjust the policy as your organization's needs change or new threats emerge. Working with a knowledgeable cyber-insurance broker can help you determine the most appropriate coverage and limits, ensuring your policy remains relevant and up-to-date.
Why You Need an IRP
Having a robust incident response plan is crucial to the success of any institution’s security policy. It allows you to set measurable standards that can be tested and used in response to security incidents, mitigating potential risks before they occur. In addition, it creates a clear path for your security team to follow should an incident occur, and it allows them to build on the process after each incident, making it more robust in case another incident should arise.
Data breaches can be highly detrimental to organizations, costing both time and money to restore themselves after a security incident. Incident response plans are meant to restore operations quickly and efficiently, saving crucial time during a security event.

How to Test Your IRP
Once you’ve developed a draft of your incident response plan, it’s time to test your IRP. The first step to testing your IRP is to conduct a vulnerability scan across your entire network in search of gaps in security coverage. The goal of this step is not only to identify these vulnerabilities but to exploit them fully. When the scan is complete, compare the results to your IRP. Does your plan include coverage for all of the vulnerabilities found in the report? If not, you should revise the IRP to include them.
Another essential part of testing your IRP is to conduct simulated attacks on your network. This practice will help gauge how effective the steps documented in the IRP are, and how well your team can follow them. After the test, meet with those involved with the incident response to conduct a post-mortem on what worked and what could be improved upon for next time. Ideally, this type of exercise should be conducted annually, at a minimum.
Ascend Can Help
Does your company have an updated Incident Response Plan? Our experts have helped organizations just like you prepare for the worst. Reach out to speak with an expert or check out the following resources on incident response:
