In 2013, recognizing the value of cybersecurity for businesses and the government at large, the President of the United States of America issued an executive order to improve critical infrastructure cybersecurity. With the aim of protecting the national and economic security of the country, the National Institute of Standards and Technology (NIST) created a cybersecurity framework for all federal agencies and business owners.
At Ascend Technologies, we’re big fans of the steps the NIST developed implement this framework because of how they’re prioritized, flexible, repeatable and cost-effective for managing cybersecurity-related risks. The NIST cybersecurity framework has stood as the gold standard for preventive security measures and aligns with our recommendations for how SMBs should approach, optimize and maintain security practices to keep their business and clients safe.
To better understand the NIST cybersecurity framework, let’s explore its facets and review how the five steps can help protect small- and mid-sized businesses.
What is the NIST Cybersecurity Framework?
The framework is voluntary guidance for organizations to better manage and reduce cybersecurity risk. It was designed to mitigate cybersecurity risks and install communications protocols for internal and external organizational stakeholders. Ascend certifies that this framework abides suitable security infrastructure for businesses of any size and any budget.
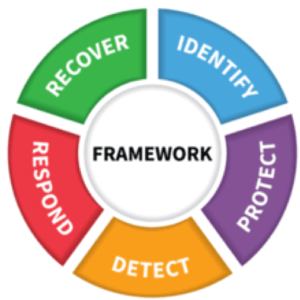
The cybersecurity framework consists of five functions that ensure a robust security ecosystem for business. The identify, protect, detect, respond and recover elements ensure each business or federal agency not only anticipates and prevents security risks, but also has a system in place for managing threats and responding in urgent situations.
The Framework Functions
Each of the framework’s five functions represents a key pillar of a successful and end-to-end cybersecurity program. They aid organizations in easily expressing their management of cybersecurity risk at a high-level and enable risk management decision-making. Let’s breakdown the functions to better understand how they work together to provide a holistic security framework.
Identify
The step that jumpstarts cybersecurity practice, identify, assists businesses in developing an organizational understanding of how to manage cybersecurity risks and how that apply to systems, people, assets, data and capabilities.
Understanding the context of how security affects business enables an organization to focus and prioritize its efforts, consistent with its risk management strategy and business objectives.
Outcomes facilitated within the identify function include:
- Identifying physical and software assets within the organization to establish an asset management program
- Identifying the business environment, the organization supports including the organization's role in the supply chain, and the organization’s place within the critical infrastructure sector
- Identifying existing cybersecurity policies within the organization to define a governance program and identifying legal and regulatory requirements regarding the cybersecurity capabilities of the organization
- Identifying asset vulnerabilities, threats to internal and external organizational resources and risk response activities as a basis for the organization’s risk assessment
- Identifying a risk management strategy for the organization including establishing risk tolerances
- Identifying a supply chain risk management strategy including priorities, constraints, risk tolerances and assumptions used to support risk decisions associated with managing supply chain risks
Protect
The second function, protect, outlines the appropriate safeguards required to deliver critical infrastructure services. This function supports a business’s ability to limit or contain a potential cybersecurity event.
Examples of outcomes fostered through the protect function include:
- Protections for identity management and access control within the organization for both physical and remote access
- Empowering staff within the organization through awareness and training, including role-based and privileged user training
- Establishing data security protection consistent with the organization’s risk strategy to protect the confidentiality, integrity and availability of information
- Implementing information protection procedures to maintain and manage information systems and assets
- Protecting organization resources through maintenance
- Managing protective technology to ensure the security and resilience of systems and assists are consistent with organizational policies, procedures and agreements
Detect
The detect function defines activities to identify the occurrence of a cybersecurity event and enables timely discovery of such events.
Examples of outcomes established within the detect function include:
- Ensuring anomalies and events are detected and their potential impact is understood
- Implementing security continuous monitoring capabilities to track cybersecurity events and verify the effectiveness of protective measures
- Maintaining detection processes to provide awareness of potential threats
Respond
The respond function establishes the appropriate actions regarding a detected cybersecurity incident and supports a business’s ability to contain its impact.
Outcomes established through the respond function include:
- Ensuring response planning processes are executed during and after an incident
- Managing communications during and after an event with stakeholders, law enforcement and external stakeholders as appropriate
- Analysis is conducted to ensure effective event response and to support recovery activities including forensic analysis and determining the impact of incidents
- Mitigation activities are performed to prevent expansion of an event and to resolve the incident
- The organization implements Improvements by incorporating lessons learned from current and previous detection/response activities
Recover
Lastly, the recover component helps identify the appropriate actions required to maintain plans for security resilience and to restore any capabilities that may have been impaired due to a cybersecurity event. This final function supports timely recovery to normal operations and ensures a reduced impact from potential events.
Examples of outcomes within the recover function include:
- Ensuring the organization implements recovery planning processes and procedures to restore systems and/or assets affected by cybersecurity incidents
- Implementing improvements based on lessons learned and reviews of existing strategies
- Internal and external communications are coordinated during and following the recovery from a cybersecurity incident
The Functions in Action
When applied to a business security process, these five functions serve to protect and arm your organization with the tools, processes and culture to respond to and even actively mitigate cybersecurity risks.
While many organizations focus on the tools and processes required to monitor and reduce risks, a truly effective cybersecurity program is only as good as the culture of awareness instilled throughout the organization.
