As a new wave of malware-focused phishing attacks gain popularity, our expert security engineers are on the frontlines. Here's what you need to know.
Our Security Operations team has noticed an uptick in a very specific malware campaign — one that has shared many of the same attributes across every attempted attack. Based on these common factors, it has become clear that a specific malware campaign is targeting US-based organizations. At this time, the source of the attack — whether it is a single threat actor or a cyberattack group — is unknown. However, the methodology of the attack has been analyzed by our team and is detailed below.
Here's what we've seen so far...
This attack starts in the same way as a majority of successful attacks do: through email.
The subject lines of these phishing emails vary from example to example, but they always start as a response. This is a common tactic used in phishing to make the recipient think this is a previous conversation and feel safe opening the message.
The content of the email contains a password protected zip file attachment and instructions to open the attachment.
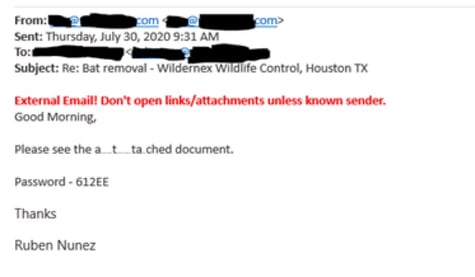
Inside the zip file is a word document. The format of this document's filename often includes a menial word and then the date. An example we have seen would be “certificate.07.20.doc".
When this file is opened, it executes a macro script that downloads and executes a file from a remote location using several standard Windows commands. In the screenshot below, you can see that the calls to certutil.exe and curl.exe have been obfuscated. We have observed that the domains and file names change in every attack, but the obfuscation methods have been the same.
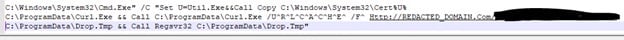
Regsvr32 has also been used every time to execute the downloaded file.
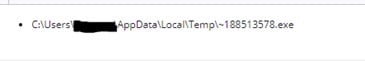
This creates another file that we believe is the final malware payload. From what we’ve seen, the file name always starts with a “~” and is named what appears to be a random collection of 9 digits. This file has always been in the “ \AppData\Local\Temp\” directory.
At this point, we’ve observed several instances of code injection as well as command & control behavior as the machine continues to be infected. IPs that we’ve observed have lead back to Russia and Romania.
While not yet confirmed, this fits with previous Emotet and Trickbot infections we’ve seen in the past. We have seen intel in the security community that there has been a recent push of Emotet, so this would align with that trend.
How Do I Protect Myself?
This attack uses several techniques and tactics that make prevention difficult. The email addresses these messages come from are all legitimate email addresses that have been accessed through compromised credentials. Additionally, the attacker's use of a password-protected zip file as the attachment is a low-tech way to get around email antivirus scanning and sandboxing.
The best defense to prevent this attack is the end user.
- If you receive an email that appears to be a response to a conversation you’re not sure you've had before, chances are good its because you’ve never actually had the conversation. Be skeptical of something along these lines that seems out of place.
- Be very careful of attachments. If it’s a password protected zip file, think twice before opening it. Usually, if someone is sending you a password-protected document, there’s a reason behind it that you should already know. If you’re not expecting this kind of attachment, don’t open it.
- If you open the document and it asks you to execute a macro, again, stop and think about it. It is not normal for Word to launch macros on your machine. If you’re in a job role where you work with macros often, usually you know where these documents are coming from and will be expecting them. Therefore, following earlier advice, if you don’t know the sender or aren't expecting a document, don't open the attachment.
For our customers, many of these detection mechanisms were already in place through our EDR, SIEM, and Malware Prevention services. Using the information we’ve collected over the last 48 hours, we’ve further refined those mechanisms and are adding to our prevention capabilities in our Email Security service to advance our customers' protection against this specific attack format.
Phishing and malware campaigns like this have become big business for attackers. Many times, these attacks lead to data theft and ransomware. Luckily, because this has become big business, the attackers are staying consistent with their tactics.
Eventually the popular attack tactics will change and evolve again — but we’ll catch them next time and continue to protect our customers as we always have.
Be safe and be skeptical of emails that seem out of place. Don't get hooked!

