The days of dividing your firewall up into three primary zones—inside, outside, and DMZ—have come to an end. Security standards such as PCI-DSS, HIPAA, NIST, and a host of others, all suggest the use of segmentation in order to protect critical systems.
But what’s the best way to design that segmentation? What goes where and who gets to talk to whom and how? Some segmentation due to WAN links and simple geography is a necessity, but it can cause the network architect to narrow their design focus to only operational concerns posed by bandwidth restriction.
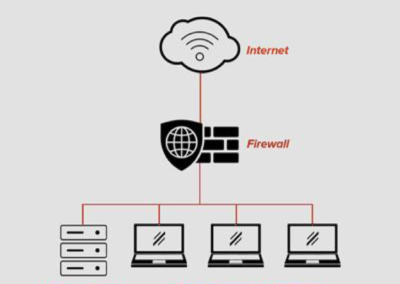
A network that is segmented operationally tends to lump all servers together based on their status as servers, rather than their specific purpose. This means that terminal servers, application servers, file and print servers, and database servers tend to reside on one subnet with minimal or no access control between them. The downside of this is that when a terminal server user executes malicious code (such as ransomware) they have an open connection to every other server in that subnet and almost no ability to monitor or restrict the flow of data aside from taking everything offline.
Example of a flat network:
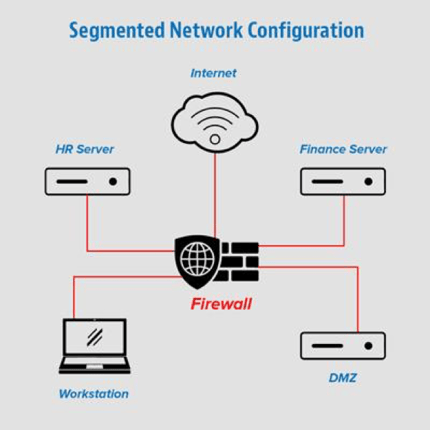
When designing your segmented network, a primary consideration needs to be the protection of your most important resources. What is the information that’s most sensitive? Is it credit card information? Patient health information? Proprietary or patented designs? Intellectual property? Those things which you can least afford to be made public are obviously those things that you should work hardest to protect.
So you have an idea of what resources you want separated from other resources, you’re on the way! Now how do you go about creating that separation and what do you do with it? Even a switch and VLANs can provide some security by making a discrete boundary between zones. Better yet, implementation of a next-generation firewall, with application filtering and logging, allows you to further specify who can send exactly what traffic to what location and get notifications of that access after the fact. An absolute must if you ever need to perform a forensic investigation.
Besides sensitive information, something else to keep in mind is vulnerabilities. Many organizations have that one application that they can’t afford to get rid of. The cost of updating the application or even the underlying operating system is prohibitive or the vendor is not supporting the app any longer. By segmenting a vulnerable server to its own zone you can specify exactly who can access it, and what applications they can use when doing so. It’s still not as good as replacing an end-of-life application or OS, but as long as you can limit the exposure of your most vulnerable systems you can probably sleep a little better at night.
Example of a segmented network:
Lack of proper segmentation allowed the Target data breach to happen when criminals exploited a vulnerability in the HVAC system managed by a vendor, and then found that they were able to reach point-of-sale systems from there. Likewise, TJ Maxx’s networks were relatively flat with point-of-sale systems all over the country becoming accessible merely by breaching the wireless network at a single store.
Proper network segmentation may take time and planning at the front end, but it pays off handsomely with a more highly available network where transactions can be tracked in detail by the system administrators and security teams. At Ascend, our experts have been segmenting networks this way for more than a decade and we have the expertise and experience to apply security-conscious network configurations to even the most complex environments. If you decide your organization needs help or guidance on how to go about a project like this, let’s get started.
Written By: Jeff Murphy, Security Engineer