Operating in a digital world comes with the risk of losing everything in a cyber incident. It’s estimated that a ransomware attack takes place every 11 seconds, and our team has observed an increasing number of businesses having their backups targeted in these attacks. So, when bad actors penetrate your environment, how do you go from being a victim of ransomware to a victor of ransomware?
Immutable Backups
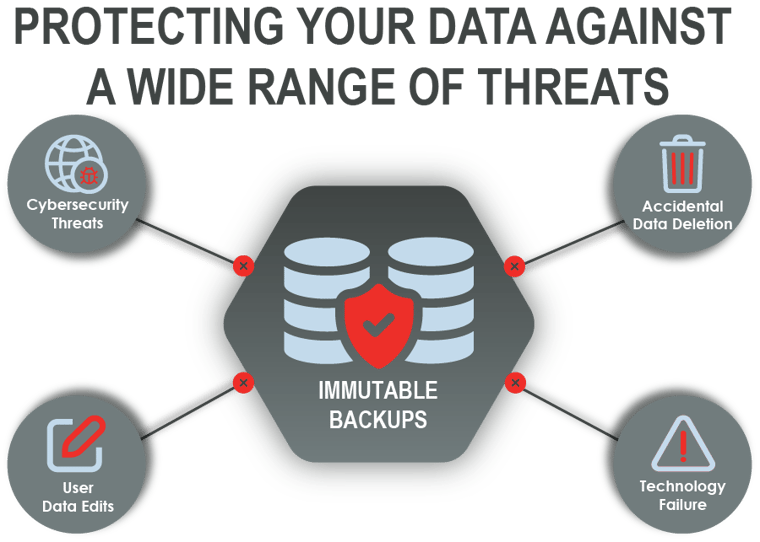
The answer could be more straightforward than you think by using immutable backups. By making your backups immutable that data, once saved, is fixed, and cannot be changed, overwritten, or deleted for a configured amount of time. Meaning that if a cyberattack hits your organization, you can rest assured that you have a ‘clean’ copy of your data to fall back on. As part of your Disaster Recovery plan, this also comes in handy in the event of natural disaster, infrastructure failure, or critical data deletion.
Additional Benefits
In addition to having peace of mind, there are other benefits to making your backups immutable. Ensuring you have accurate, untouched copies of your data helps keep your organization in compliance. Additionally, you can prevent users from making unauthorized changes regardless of their level of authorization.
Drawbacks
Making your data immutable also has a downside. They must be stored for a fixed amount of time, and it is recommended that organizations have multiple copies stored in different locations. This adds additional costs to data storage but is minimal as the cost of cloud storage has been decreasing over time. The cost of storage is also preferable to the cost of the ransom or the significant downtime your organization would face with no available backups.
A Wholistic Approach
So, are immutable backups the answer to all your data security concerns? Having an immutable backup protects against data loss, but not data leaks. They are a powerful tool to ensure your data is accessible and recoverable, but as with other security measures, you can’t just have a set it and forget it mentality. You still need to evaluate your data management and cybersecurity strategies for potential risks.
How often do you backup your data? How much of your information is considered critical data? What preventative measures does your organization take against cyberattacks? What is your disaster recovery strategy if you experience a breach? You need to answer all these questions and more while taking steps to have solutions implemented to protect your organization.
Securing your organization should include several layers that cover prevention, protection, detection, and response. Backup as a Service is just one important layer. Other layers include:
Ascend Can Help
At Ascend Technologies, we have the experts to help your organization ensure that your data is protected in a cost-effective, low-impact way. Our team can guide you through identifying, strategizing, and implementing processes and technologies that enable efficiency and productivity while protecting you from the worst-case scenario. Contact us today to get started.
